
Deep dive into the Qilin ransomware – a leading RaaS double extortion threat. Learn Qilin’s tactics, attack vectors, encryption methods, and real incident impacts, plus expert defense strategies and how Xcitium’s Zero-Dwell stops Qilin ransomware in its tracks.
Introduction
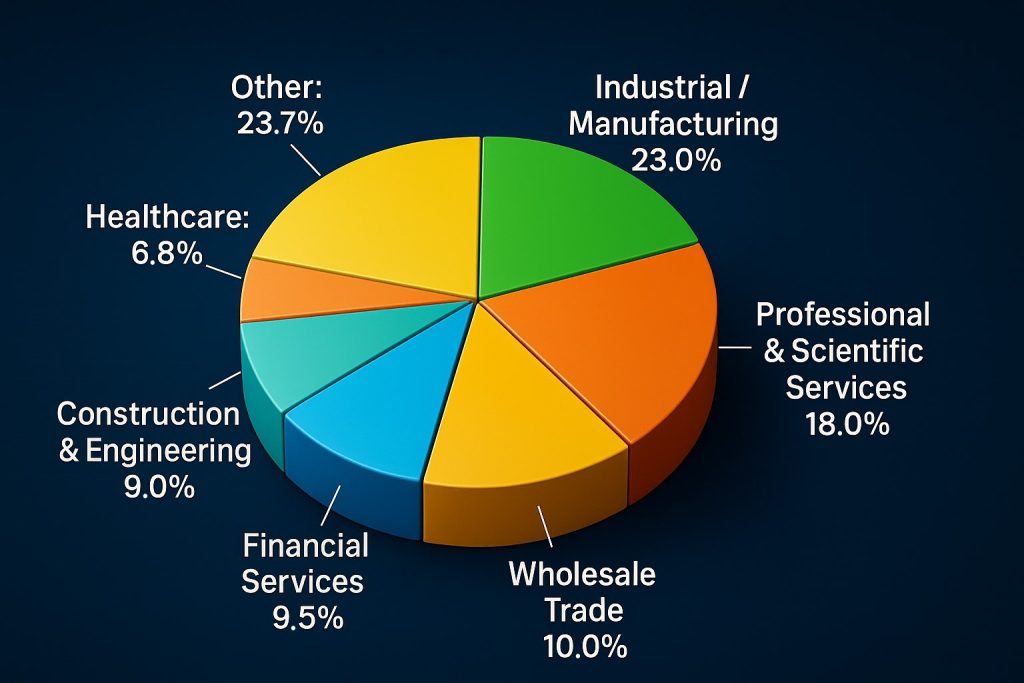
Qilin ransomware definitely belongs under the category called “Ransomware as a Service” or ‘RaaS’ and emerged as a cybercrime menace during the middle of the year ‘2022’. Qilin ransomware used the Chinese mythological figure ‘Qilin’ as its new name. It acts very effectively because of the double extortion method used by it. Qilin encrypts file directories and steals valuable information from its victims. One attack targeted Synnovis, a UK-based healthcare organization, in early 2024. The group demanded $50 million in ransom. They also stole 400 GB of sensitive data. This attack caused significant fear and disruption within the organization. It is clearly targets the ‘organizational’ setup with proper ‘cybersecurity’ protection.
Threat Actor Overview
The group functions as a professional RaaS group. They sell their ransomware platform to their affiliates and take an earnings share as their pay. The ransomware platform assumes the major responsibilities of handling the hard work. The platform offers a web interface that assists the hacking group create custom malware payloads. This platform assists the group’s hackers publish the stolen information on their dedicated leakage platform. Additionally, it assists them communicate ransom requests on the part of their hackers. As an expense of their woes, the hacking group assumes a cut of approximately 15-20% of their ransom earnings. This leaves the hackers with an earnings share of 80-85% of the bounty. This payment arrangement aids the hackers rake in the increased ransom earnings by conducting their operations across big game hunting stly over their industrial targets.
This attack might take place because of financial motives on the part of the group called the Qilin organization. Qilin has steadily increased its attack frequency. The group targets organizations capable of paying high ransoms. These include manufacturers, financial institutions, retailers, healthcare providers, and government entities. As of early 2024, ransom demands ranged from $50,000 to $800,000. This shows the group specifically focuses on victims who can afford these amounts.
What Sets the Qilin Group Apart
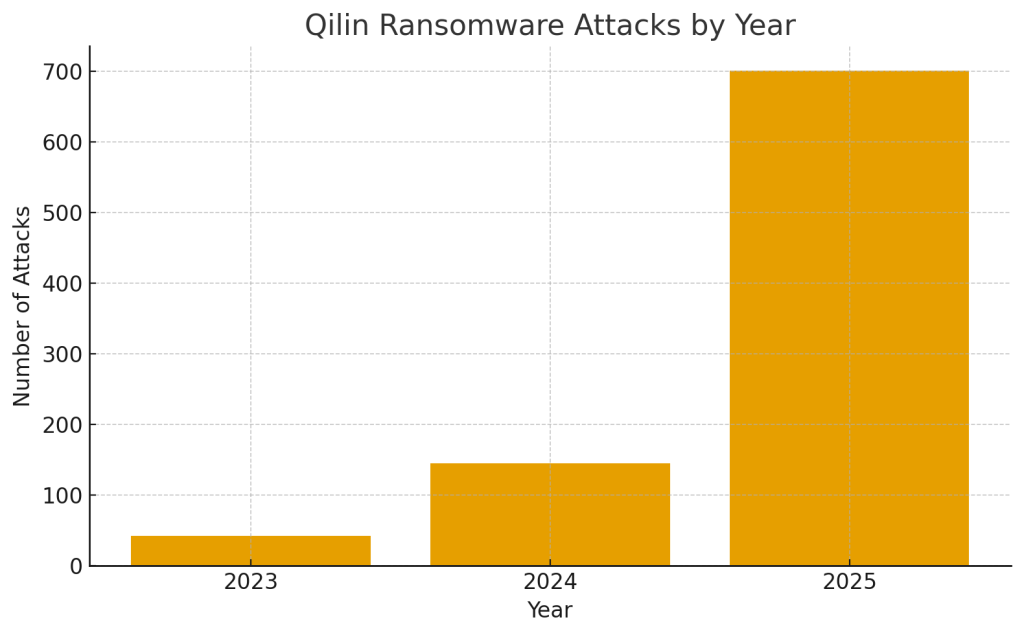
By the middle of 2024, the group had managed to attack more than 150 organizations spread across over 25 nations. This led the group to emerge as one of the most active ransomware attacking entities of the sort recorded so far the following year—the group’s attack rate having multiplied by over 280% just a few months after the group took over due to the bankruptcy of the leading ransomware group called the ‘RansomHub’ group at the beginning of the year.
What differentiates the group so greatly is the professionalism and infrastructure that the group offers. The group’s affiliate platform (which the group promotes on the ransomware affiliate platform RAMP) offers highly customizable software with extensive documentation provided. The group’s malware allows affiliates the option to create their builds on Windows and Linux operating systems, as well as on VMware ESXI. Additionally, the group offers the kind of customer support that cybercrime groups normally do not offer. This ranges from legal advice on dealing with the pressure of the police down to how the group’s PR can help make the group’s extortionary tactics more believable. All of these elements make the group more than just a ransomware crew; it’s an overall cybercrime platform.
Attack Vectors
The various tactics used by the Qilin ransomware group involve different strategies that take the form of social engineering tactics, weak authentication exploitation, as well as exploitation of known vulnerabilities. Some of the common tactics used by the group include the following:
- Phishing and Social Engineering – Most attacks come with an email that’s a phishing/spear email that brings the downloader/loader or could even take passwords.
- Compromised RDP/VPN Access – Attackers access the exposed RDP/VPN connections using brute force or the fact that the passwords are stolen or purchased on the dark web.
- Exploiting Known Vulnerabilities (CVEs) – This malware rapidly uses unpatched vulnerabilities on Internet-connected infrastructure, including vulnerabilities of the Fortinet VPN system and the Veeam Backup and Replication system (CVE-2023-27532). Any out-of-date Internet application may serve as an entry point
- Remote Monitoring and Management (RMM) Tools – Once the attacker gains the first point of entry, the affiliate utilizes legitimate administrator tools and environments provided by the Cobalt Strike framework.
- Credential Theft & Lateral Movement – Attackers steal highly privileged access using tools like Mimikatz or scripts with the ultimate goal of orchestrating mass ransomware attacks via PsExec, WMI, or SSH.
As such, a defense-in-depth approach becomes the priority due to the various entry points of the malware that may remain unpatched.
Technical Analysis – How Qilin Operates
Once Qilin ransomware gains a foothold in a network, it executes a sophisticated, configurable attack routine. The malware usually arrives as a loader or dropper placed on a victim machine, often saved in a innocuous location like C:\Temp\w.exe. To start the encryption process, the attackers (or an automated script) launch the Qilin executable with a unique password provided as a command-line argument. This password acts as a cryptographic key: Qilin’s code will hash the password and verify it matches a hash embedded in the binary’s configuration, otherwise the ransomware won’t activate. This clever mechanism prevents the malware from running inadvertently or being analyzed without the correct key. It essentially locks the “weapon” until the affiliate pulls the trigger with the right password.
Once unlocked, Qilin will aggressively spread and execute across the network. The ransomware can spawn copies of itself and use tools like PsExec for distribution to other machines (controlled via a --spread-process parameter). In Windows environments, Qilin has even been launched in Safe Mode to bypass endpoint security, a mode where many antivirus and EDR agents don’t run. Affiliates can also configure Qilin to create persistence mechanisms; in one incident the attackers created a malicious Group Policy Object that triggered the ransomware on user logon, ensuring it executed even after system reboots. Techniques like these highlight Qilin’s goal of domain-wide encryption – it strives to infect as many servers and workstations as possible once inside.

Encryption and File Impact
The ransomware application utilizes the AES-256 algorithm with an RSA-2048 or RSA-4096 algorithm. This allows only the hackers to access the required information. Some of the ransomware variants even offer the option of using ChaCha20, reflecting the versatility of the ransomware group regarding algorithms used. The ransomware application even allows its users/affiliates to choose their type of ransomware and algorithms directly on the interface of the ransomware application known as Qilin.
Through the attack, the malware introduces an additional file extension specific to the victim—a randomly generated string that could be .MmXReVIxLV—which serves as an identification of the victim or company on their portal. Tor links are used on the ransomware note that contains this identification.
Qilin causes the highest disruption by deleting active processes (databases, email servers, Office applications) so that the files can potentially get encrypted. This ransomware avoids the system directories but focuses on business documents, backups, and share folders. Some versions of this ransomware offer partial file encryption so that the execution can happen at a better pace. At the end of the attack, the ransomware leaves a considerable amount of files inaccessible except with the perpetrators’ private key.
Evasion and Anti-Analysis Techniques
Qilin ransomware carries advanced evasion capabilities. The coding of the ransomware contains highly obfuscated routines that make the program’s control flow complicated. Further, it requires the entry of a run-time password; thus, it cannot run within the sandbox environment.
To effectively disable the defenses, it terminates security-related tasks, deletes the system’s log information, and deletes the Volume Shadow Copies. The new version of the ransomware that relied on the Rust programming environment and was traced at the end of the fourth quarter of the year 2024 removes the Windows Event Log records. After
Additionally, the group utilizes Bring Your Own Vulnerable Driver (BYOVD) attacks. They install vulnerable but genuine drivers that are digitally signed using outdated Toshiba power management drivers or the Zemana Anti-Rootkit drivers with the intent of getting kernel-level access. This facilitates the killing of the various security-related components by the kernel.
On the whole, the malware works stealthily, breaches security protection measures, steals logon credentials, and provides very aggressive encryption. The malware’s well-designed and very versatile cryptographic system makes it one of the dangerous ransomware viruses that organizations currently battle with.

Data Exfiltration (Double Extortion)
A typical double extortion ransomware operation, the group’s modus operandi begins with the stealthy exfiltration of valuable information, including documents, databases, customer records, and financial details. This creates the incentive of potential disclosure even if the victim company manages to restore its system through backups. A malware called Rclone may aid this activity.
But if the victimised organizations do not consent, the stolen records are published on the Dedicated Leak Site on Tor by the group called the Qilin. This platform displays the names of the victimised organizations and sample datasets along with a timer set prior to the release of the records. Despite the Chinese logo resembling the character ‘Qilin’, the text used on the platform contains Russian and English languages. The group even runs a clearnet mirror called ‘WikiLeaksV2’.
Within negotiations, the group utilizes the accessed information as a form of intimidation of the victim by showing them file listings or instances of the sensitive information they possess. This may include the decryption of a few of the accessed files as confirmation of the successful performance of the decryption tool. After the ransom payment, the group assures the victim that the accessed information will be deleted; this information will instead go on the black markets if the ransom payment fails.
But the double extortion makes the attack on its targets extremely more dangerous as even organizations that are well-backed up cannot avoid the effects of the attack on the released information that may result in a punishing financial blow due to the release of sensitive materials that may result in penalization. Previous leaks on the group’s part include medical records on patients during the SYNNOVIS attack and designs of the Nissan company’s subsidiary.
Recent Incidents & Impact
Qilin ransomware has become one of the most dangerous RaaS families worldwide. Attacks increased significantly between 2024 and 2025. One major incident involved Synnovis, a U.K.-based medical diagnostic company, in June 2024. The group managed to steal approximately 400GB of patients’ records and set the ransom at an astonishing $50 million.
Victims of the attack include Central Texas Pediatric Orthopedics and Next Step Healthcare. The publisher behind the Big Issue titles was also affected. Another major victim was the auto parts conglomerate Yanfeng.
Asahi Group Holdings was hit at the end of 2025. The attack took systems offline for three weeks. The attackers claimed to steal 4 terabytes of design data from Nissan Design Center’s Creative Box.
The group’s activity surged in 2024, with 179 reported victims. In the first ten months of 2025, over 700 more victims were reported. Since its creation, Qilin has conducted 926 attacks. Of these, 168 attacks were reported, resulting in the theft of more than 2.3 million records. The stolen data exceeds 116 GB. The U.S. tops the list of affected nations followed by France, then Canada, South Korea, then Spain.
The implications are severe—not only lost productive time but notice of breaches and possibly ransom payments. The success of the group’s affiliate program has nudged others into action. As pressure mounts on the group through increased law-enforcement investigation, the group remains among the active ransomware threats on the internet today.

Defense & Mitigation Strategies
A layered defense strategy that assumes attackers will bypass certain security measures must be employed when defending against the Qilin ransomware. These critical security elements include:
- Adopt a Zero Trust Posture: All users and devices should be considered untrusted entities. Impose least privilege access, segregated access to sensitive systems, and force a new authentication step on administrative tasks.
- Prompt Patch Management: Update promptly on internet-accessible infrastructure such as VPNs and firewalls. Manage software assets and focus on patching successfully exploited CVEs.
- Blocked Remote Access: Disable unnecessary RDP services, enable multi-factor authentication on all remote access methods, and choose complex passwords with an inertia lockout protection. Hardening remote access will eliminate the first attack vector of the Qilin.
- Strong Credential Hygiene: Implement MFA on all systems and remove stale accounts, do not reuse passwords, and reset potentially vulnerable passwords. This is made easier with strong identity governance that mitigates the effects of compromised passwords.
- Network Segmentation and Monitoring: Isolate the user networks from the server environment, or implement ACLs/internal firewalls that limit communication. Monitor the unusual transfer of data or connectivity with malicious IPs to identify early signs of exfiltration.
- Endpoint Protection and Isolation: Implement EDR tools with ransomware behavior detection and tamper protection.
- Backups and Recovery Planning: Make sure there are backup systems that are offline/immutable and tested regularly. Disaster recovery procedures should enable the rebuilding of critical systems without paying the ransom.
- User Training and Phishing Defense: Educate employees on how to identify attack e-mails and perform simulation exercises on the organization’s employees. Enhance the security of e-mails through email filters and sandboxes.
- Protect Privileged Accounts: Limit admin rights, implement dedicated admin computers, control Domain Admin group accounts. Monitor admin account activity alerts.
Xcitium-Specific Protection Mechanisms
Modern endpoint security solutions such as Xcitium’s Zero-Dwell are purpose-built to defeat ransomware like Qilin. Xcitium’s approach centers on a patented “Zero-Dwell” technology that prevents unknown malware from causing any harm by isolating it at runtime. This has huge implications for stopping threats like Qilin:
- Auto-Containment of Ransomware: When a Qilin ransomware sample attempts to run on an Xcitium-protected endpoint, it is immediately executed in a virtualized container environment with no access to the real file system or critical OS resources. The ransomware will believe it’s encrypting files, but in reality it’s encrypting only the virtual disk within the container. The device’s actual data remains untouched. Xcitium’s containment essentially freezes the threat’s dwell time at zero – the malware is never given the chance to roam free on the system. This default-deny isolation happens instantaneously and without user intervention.
- Preventing Damage and Lateral Spread: Because the contained Qilin sample cannot access the real disk, it cannot encrypt any files. It also cannot alter system processes or move to other machines. Xcitium blocks all write privileges for untrusted processes. This stops file encryption, backup deletion, and registry changes. Even if the ransomware tries to network scan or propagate, those actions occur within the isolated sandbox.
- Analysis and Verdict without Disruption: While Qilin is contained, Xcitium’s platform analyzes its behavior in real time. The system uses both static and behavioral AI engines. These engines check whether the process is safe or malicious. Users can keep working because the unknown file cannot affect the host system. If the file is a false positive, administrators can easily release it from containment. This approach provides security with minimal business interruption – something critical when dealing with fast-moving threats.
Case Study: Xcitium vs. Qilin Ransomware
Xcitium’s Zero-Dwell has proven exceptionally effective against ransomware in real-world evaluations. In fact, in an independent year-long test by AVLab, Xcitium’s solution achieved a 100% malware neutralization rate, blocking all 3,103 in-the-wild malware samples (including ransomware) without allowing any system compromise.
Internal tests specific to Qilin have yielded similarly strong results: when Xcitium researchers pitted the platform against a collection of Qilin ransomware samples, every single sample was isolated and instantly taken down. The Qilin payloads could not encrypt files or spread, effectively rendering the attack moot. This kind of outcome validates that a Zero Trust strategy can stop even advanced, evasive ransomware. Unlike traditional antivirus which might miss novel variants, Xcitium’s approach doesn’t need to recognize the malware – it simply cages it until a verdict is reached, by which time the ransomware has failed to achieve its objectives.
In summary, Xcitium’s ransomware protection offers a powerful last line of defense should other controls fail. Zero-Dwell directly addresses the ransomware problem by removing the opportunity for malware to do harm. It complements preventive measures (like patching and user training) by assuming breach and constraining what malware can do.
As Qilin and other RaaS groups evolve, real-time threat isolation becomes essential. Solutions must detect and neutralize unknown malware immediately. Xcitium combines isolation, intelligent analysis, and a global threat intelligence cloud. This platform provides strong protection against ransomware tactics, including rapid encryption and data destruction.
IOCs and Technical Indicators
Indicators of Compromise (IOCs) for Qilin ransomware can help organizations detect and block the threat before it causes damage. Security teams should watch for the following Qilin-specific indicators and patterns:
- Encrypted File Extension: Qilin appends unusual, random-looking extensions (like
.MmXReVIxLV) to encrypted files. A sudden wave of files sharing a strange extension is a strong sign of active encryption. - Ransom Note Filename: Qilin typically drops notes named README.txt or [unique_id]-DECRYPT.txt across directories. Multiple new README files containing Qilin/Agenda references are a clear IOC.
- Malicious Driver Use (BYOVD): Qilin has abused legitimate but vulnerable drivers such as TruEnergyDrv.sys and zamguard64.sys. Their unexpected presence or loading on an endpoint is a major red flag.
- Network Indicators: Large outbound data transfers to unfamiliar IPs, FTP/HTTP/S spikes, or internal hosts attempting to access Qilin’s .onion negotiation portals are strong indicators of exfiltration and staging.
- Process Behavior: Execution from temp directories with long password-like arguments (e.g., C:\Temp\w.exe ), attempts to delete Volume Shadow Copies, or killing security services signal ransomware activity.
Integrating these IOCs into SIEM, EDR, and network monitoring enables early detection and isolation before encryption takes hold.
Sample Hashes
Conclusion
Qilin is not just another ransomware family—it’s a fully armed, rapidly evolving RaaS ecosystem built to bypass traditional defenses. Its affiliates operate with professional-grade tooling, advanced evasion techniques, and a proven record of high-impact breaches. No organization—regardless of size, sector, or maturity—is immune. The only reliable strategy is one that assumes breach and removes the attacker’s ability to do damage.
This is exactly where Xcitium’s patented Zero-Dwell platform changes the game.
Unlike signature-based or behavior-dependent solutions that act after malicious activity begins, Xcitium neutralizes ransomware at the moment of execution. Every unknown file is automatically isolated in a secure environment—eliminating lateral movement, blocking encryption attempts, and stopping data destruction before it can start. Even advanced RaaS threats like Qilin become harmless.
With Xcitium, ransomware has zero dwell time, zero impact, and zero chance to compromise your business.
As threat actors evolve, your security must evolve faster.
Choose the only endpoint protection designed to make modern ransomware irrelevant. Xcitium is your chance.
Transform your security posture with the power of Xcitium’s Advanced EDR.




