
AsyncRAT is a notorious C# Remote Access Trojan (RAT) used by threat actors globally. Learn how this open-source malware works, its MITRE TTPs, and crucial defenses against data theft and system compromise.
What Is AsyncRAT? Origin, Capabilities, and Threat Landscape
AsyncRAT is a renowned strain of Remote Access Trojan (RAT) malware designed specifically with the purpose of providing illicit hackers unnoticeable control over compromised systems. The name AsyncRAT itself, “Asynchronous Remote Access Trojan,” identifies the fundamental purpose behind the malware, which is the usage of asynchronous communication.
Created originally using C# and the .NET framework, it first appeared publicly on GitHub in 2019. Its original purpose, designed by its creator, had been as legitimate software for remote administration, although its potent capability for backdoor entry rendered it immediately appealing to cybercriminals.
This open-source threat greatly reduces the entry barriers for cyber attackers, even for those lacking extensive programming knowledge. The AsyncRAT enables the attacker to perform commands, harvest vital information, and track user activity in the background as soon as the system is compromised.
The Engineering Behind the Threat: How AsyncRAT Works
AsyncRAT is written in C# and compiled into Microsoft Intermediate Language code, allowing it to utilize the .NET environment developed by Microsoft to provide high levels of modularity and ease of portability on Windows-based operating systems. This modularity and adaptability have also allowed it to easily mutate and spawn numerous different malware variants, with more than 465 MSIL variants recorded by the end of 2025.
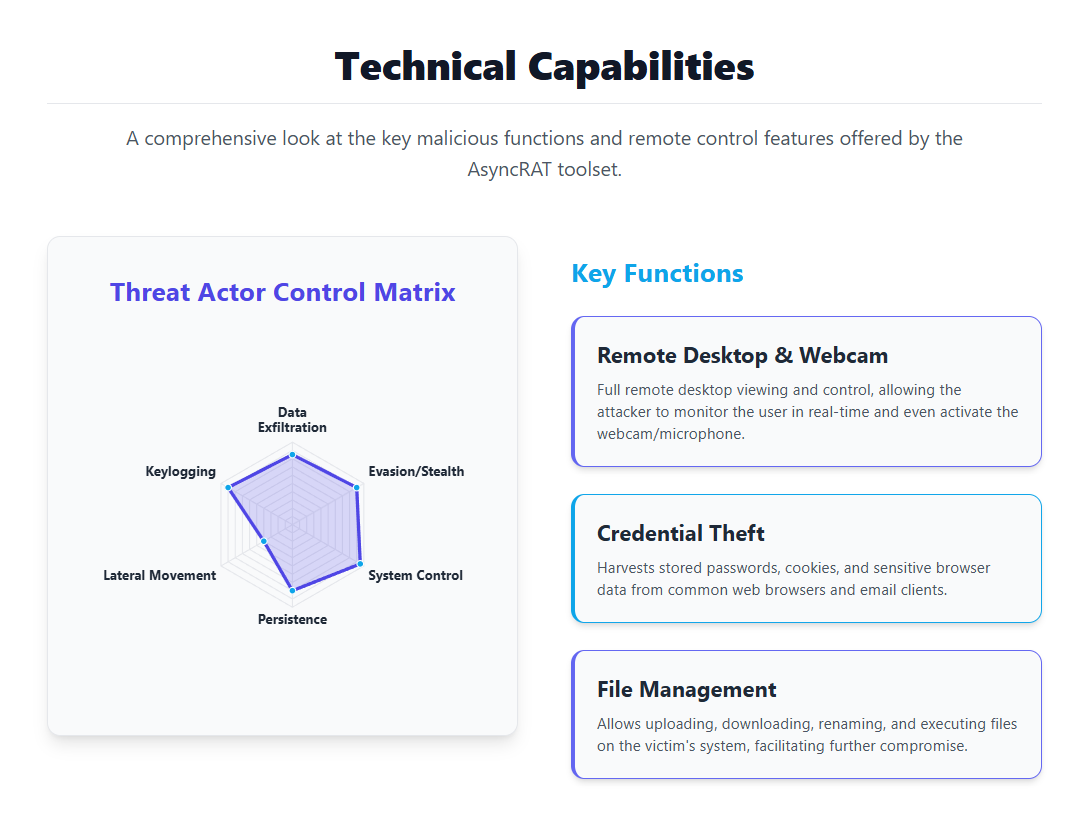
After deployment, AsyncRAT functions as a full-fledged spyware and remote control tool. Its functions include the functionalities of a keylogger, taking screenshots, and the control to manage the target’s microphone and camera. Interestingly enough, the main purpose of the employment of AsyncRAT aims at being the final stealer or launcher for the preparation of the auxiliary payload of ransomware. Moreover, AsyncRAT also has the functionality to disable defense mechanisms or initiate a denial-of-service attack.
Stealth by Design: AsyncRAT’s Infection, Injection, and Sandbox Evasion
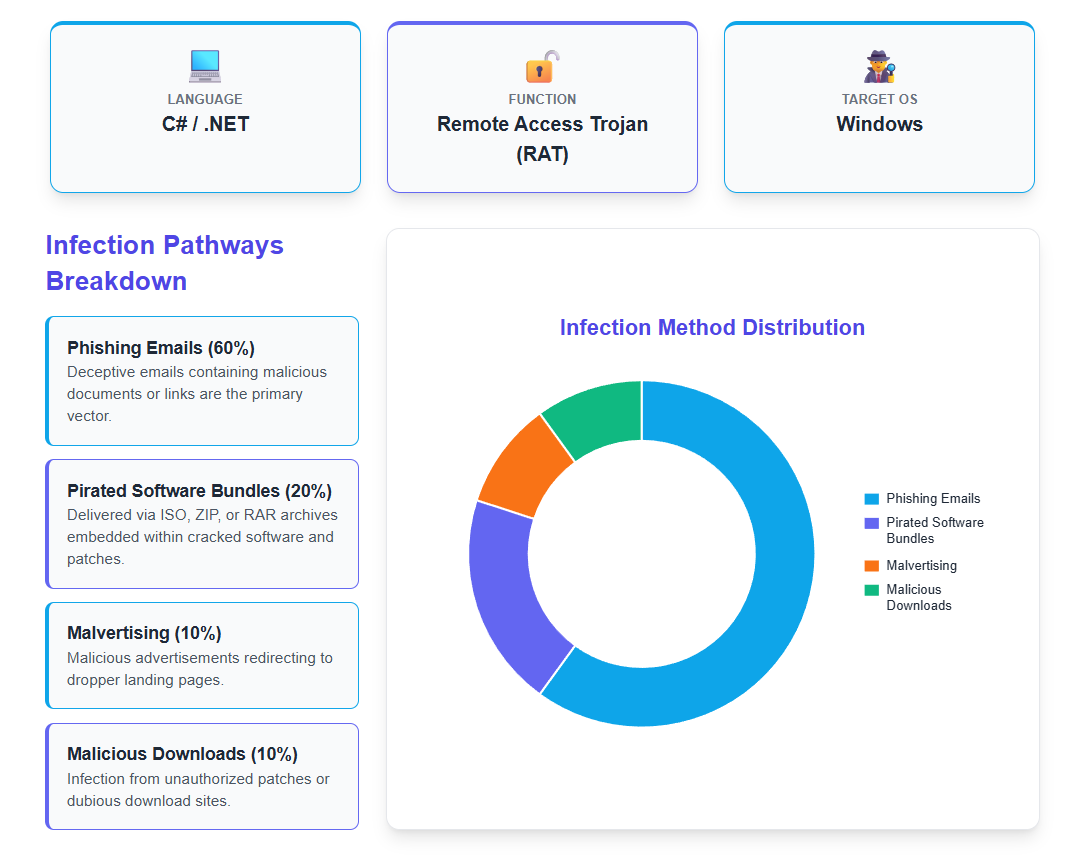
The threat actor usually shares the functionality of AsyncRAT via social engineering methods such as the use of phishing emails containing attachments with extensions like ZIP, ISO, and HTML. SEO Poisoning campaigns are also used to share the malware by posting links on websites that have been infected with harmful information with generic search terms such as “employment agreements.”
To circumvent current endpoint security, attackers have used file-less attacks, where they load their malware into memory, and Reflective Loading, which entails injection of AsyncRAT into trusted .NET applications like RegSvcs.exe.
The malware also uses anti-analyze techniques and performs checks on WMI for VMware and/or VirtualBox virtualization detection. If the malware determines that the environment is sandboxed/virtualized, the flow of execution can stop. Additionally, for its persistence mechanism, AsyncRAT checks for the availability of administrative privileges and uses them to create scheduled tasks with the help of SchTasks.exe.
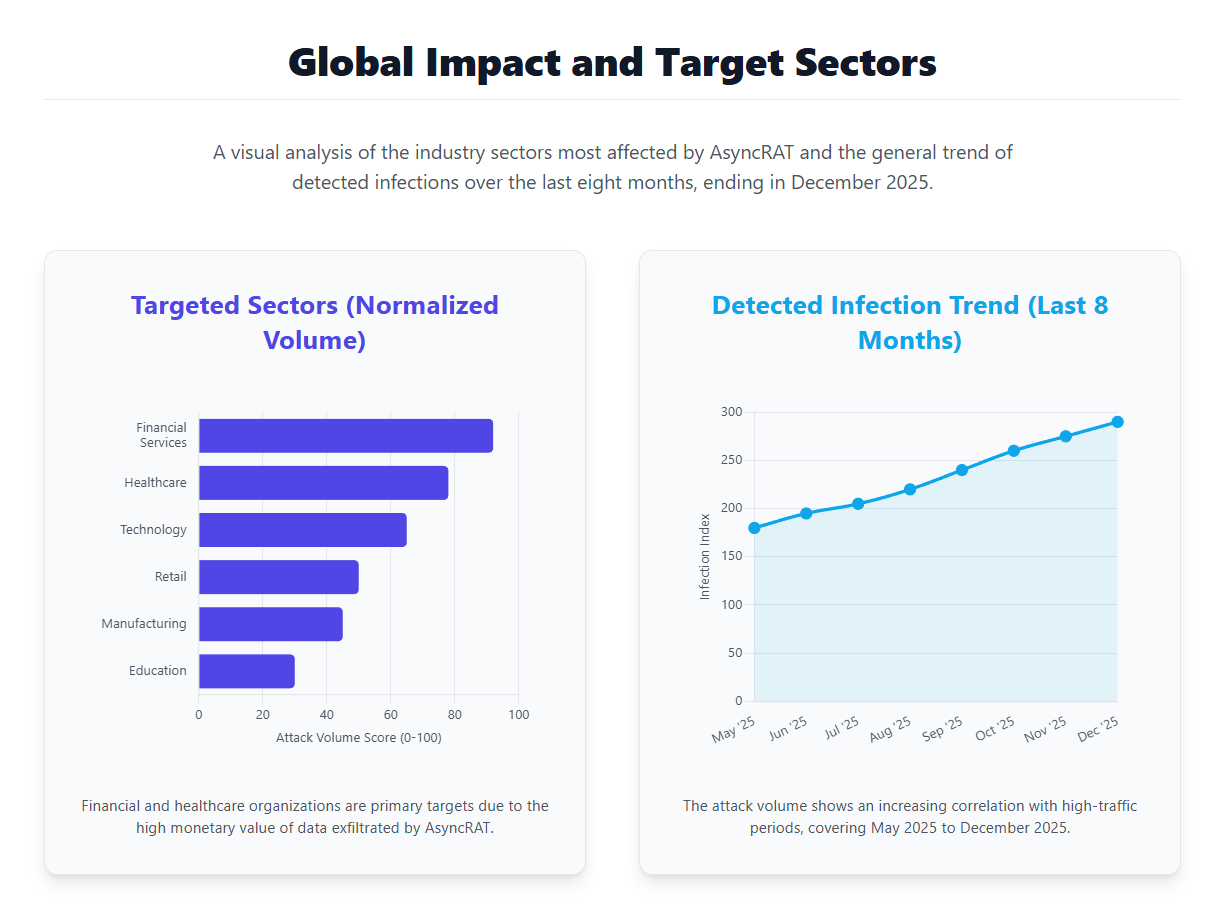
Global Impact and Notable Campaigns
- Global Phishing Campaigns: Used in large-scale phishing, leading to thousands of compromised endpoints worldwide.
- COVID-19–Themed Attacks: Embedded in fake health content, causing widespread credential theft and intrusions.
- Education Sector Breaches: Enabled remote access, data theft, and ransomware follow-ups, disrupting operations for weeks.
- SMB Financial Impact: Incidents resulted in tens to hundreds of thousands of dollars in losses from downtime and response costs.
- Ransomware Staging Tool: Frequently used as initial access, contributing to multi-million-dollar extortion demands.
- Credential Theft at Scale: Keylogging campaigns caused mass credential leaks and underground resale.
- Critical Infrastructure Exposure: Infections led to production delays and six-figure recovery costs.
- QuirkyLoader Campaigns: AsyncRAT distributed via QuirkyLoader spam campaigns, impacting large numbers of Windows users.
- Discord-Based Distribution: Malicious Discord invite links used to spread AsyncRAT, enabling credential theft and remote control.
- Paste.ee Abuse: Attackers leveraged Paste.ee as C2 infrastructure, complicating detection and takedown efforts.
- High Prevalence Ranking AsyncRAT ranked among the most widespread malware families globally, maintaining high infection volumes throughout the year.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique | Description |
|---|---|---|
| Initial Access | T1566.001 | Spearphishing Attachment – Delivery via malicious email attachments. |
| Execution | T1059.001 / T1059.007 / T1105 | PowerShell; JavaScript; Ingress Tool Transfer – Script-based execution and payload retrieval from C2. |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder – Persistence via registry keys or startup folders. |
| Defense Evasion | T1497 / T1140 / T1202 | Virtualization/Sandbox Evasion; Deobfuscate/Decode Files; Indirect Command Execution – Sandbox evasion, obfuscation, and indirect execution. |
| Discovery | T1057 / T1082 | Process Discovery; System Information Discovery – Process enumeration and host information gathering. |
| Command and Control | T1071.001 / T1104 / T1571 | Web Protocols; Multi-Stage Channels; Non-Standard Port – HTTP/HTTPS-based, multi-stage C2 over non-standard ports. |
| Exfiltration | T1041 | Exfiltration Over C2 Channel – Data exfiltration via the existing C2 channel. |
Case Study: Xcitium vs. AsyncRAT
Xcitium effectively neutralizes AsyncRAT by leveraging its advanced Zero Dwell isolation technology to prevent the malware from ever reaching the host system. While AsyncRAT is a formidable remote access trojan designed for system monitoring and data exfiltration, Xcitium renders it powerless through immediate identification and containment.
As soon as the malicious executables are triggered, the isolation engine flags every process and moves them into a secure, virtualized environment. This ensures that even high-volume attacks such as forty simultaneous threats are captured and quarantined in real-time without impacting the underlying operating system. By keeping the environment completely isolated, Xcitium provides a proactive defense that identifies and blocks sophisticated threats before they can cause any damage.
Indicators of Compromise (IOCs) for Defense
- Agile C2 Infrastructure: Rapidly shifting IP addresses that render static blacklisting ineffective.
- AsyncMutex_6SI8OkPnk: A unique mutex created upon infection to prevent duplicate instances, serving as a primary host-based marker.
- Suspicious SchTasks.exe Execution: Monitoring for scheduled tasks referencing non-standard directories like
%ProgramData%orC:\Users\Public. - Process Injection: Evidence of memory injection into legitimate .NET processes, specifically
RegSvcs.exe. - Dynamic DNS Usage: C2 communication utilizing resilient domains from providers like
duckdns.org(e.g.,asyncmoney[.]duckdns[.]org). - Non-Standard TCP Ports: Anomalous outbound network traffic on specific ports such as 7829, 7840, 7841, and 7842.
AsyncRAT SHA-1 Samples & Zero‑Dwell Threat Intelligence Reports
Conclusion: An Open-Source Tool With Enterprise-Scale Impact
AsyncRAT proves that some of the most dangerous threats are not hidden in elite underground forums. They are freely available, constantly modified, and endlessly reused. What began as a remote administration tool has evolved into a global access broker, enabling espionage, credential theft, and ransomware staging across every sector.
Its success is not based on sophistication alone, but on availability. When anyone can deploy a fully capable RAT with minimal effort, scale becomes the real weapon.
Why AsyncRAT Remains So Effective
AsyncRAT continues to thrive because it exploits the same gaps many environments still have today:
- Users executing seemingly harmless files
- Malware loading directly into memory
- Legitimate system processes abused for execution
- Sandbox and virtualization checks bypassing analysis
- Persistence established before alerts are reviewed
- Detection occurring after compromise has already begun
Once AsyncRAT is running, attackers gain continuous visibility and control. From there, escalation is only a matter of time.
How Xcitium Stops AsyncRAT From Taking Hold
In environments protected by Xcitium Advanced EDR, AsyncRAT never gains a foothold.
- Unknown executables are isolated at execution
- Fileless and reflective loading attempts fail immediately
- Injection into trusted .NET processes is blocked
- Persistence mechanisms never activate
- Command and control traffic never establishes
- Staging for ransomware collapses before it starts
AsyncRAT loses its greatest advantage, time on the system.
Break the Access Chain Before It Becomes an Incident
AsyncRAT shows how quickly open-source malware can turn into enterprise-scale damage when execution is allowed by default. Prevention requires stopping unknown activity at the moment it begins, not reacting after credentials are stolen or ransomware is deployed.
Protect your endpoints from remote access trojans, loaders, and post-exploitation tools.
Choose Xcitium Advanced EDR, powered by the patented Zero-Dwell platform.



