
With the deprecation of Skype for Business in May 2025, the majority of enterprise communications have shifted to Microsoft Teams. While the platform enables better collaboration, it has also opened new doors for cybercriminals. One of the most perilous trends is using Microsoft Teams to conduct phishing and malware distribution.
The End of Skype
Microsoft has officially announced the retirement of Skype for Business as of May 15, 2025. With over 270 million monthly active users, Microsoft Teams has become the go-to solution for remote and hybrid collaboration. Companies that once relied on the simplicity of Skype are now bringing on the more complex Teams ecosystem—without necessarily understanding its security implications in many instances.
In contrast to Skype, Teams provides integrated file sharing, real-time collaboration, calendar integration, and support for third-party apps—all of which introduce a broader attack surface if not properly secured. This also exposes Teams as a potential channel for phishing attacks.
Phishing via Microsoft Teams
In a recent investigation by Red Canary, attackers leveraged compromised Office 365 accounts and newly created fake Teams identities to impersonate internal IT departments. Here’s how the attack worked:
Attack Flow Overview
- Fake IT Message: The victim receives a Teams message from a spoofed user claiming to be “John from IT Support.” The message may include urgency like:
“We noticed suspicious logins on your account. Please verify your credentials here to avoid account lockout.” - Chat Invitation on Teams: Attackers send formal-looking chat invitations, often mimicking Teams’ default message styling.
- Click on Malicious Link: Users are directed to a fake Microsoft login page or a file hosted on a malicious SharePoint clone.
- Access Gained: Once credentials are entered, attackers either:
- Deploy malware (e.g., AgentTesla, RedLine Stealer)
- Reuse credentials for lateral movement
- Establish persistent access via OAuth abuse
Why Teams Is Targeted
- Trust Assumptions: Internal chats are often implicitly trusted.
- File-Sharing Integration: Allows payload delivery via OneDrive/SharePoint.
- App Overload: Users are overwhelmed by Teams features and tend to click without verifying.
Recommended Security Settings
Securing Microsoft Teams requires layered defense and a “zero trust” approach:
| Setting | Action |
|---|---|
| Disable External Access | Teams Admin Center → Org-wide settings → External access |
| Enforce MFA | Microsoft Entra → Users → Per-user MFA |
| Enable Safe Links/Safe Attachments | Microsoft Defender → Threat Policies |
| Restrict File Uploads | Teams Admin Center → Messaging policies → File sharing |
| Audit Guest Access | Admin Center → Azure AD → Enterprise applications → Users |
Skype vs. Teams
| Feature | Skype for Business | Microsoft Teams |
|---|---|---|
| File Sharing | Limited | Integrated with OneDrive |
| Third-party App Support | None | Extensive |
| External Collaboration | Rare | Common |
| MFA Support | Minimal | Fully integrated (via Entra) |
| Security Complexity | Low | Medium to High |
How to Train Your Users
- Scenario-Based Phishing Simulations
Use tools like Microsoft Attack Simulator or KnowBe4 to simulate realistic Teams phishing scenarios. - Highlight Real Examples
Include screenshots of real phishing messages (with red flags annotated). - Create “Spot the Phish” Challenges
Encourage users to participate in monthly awareness campaigns.
Examples
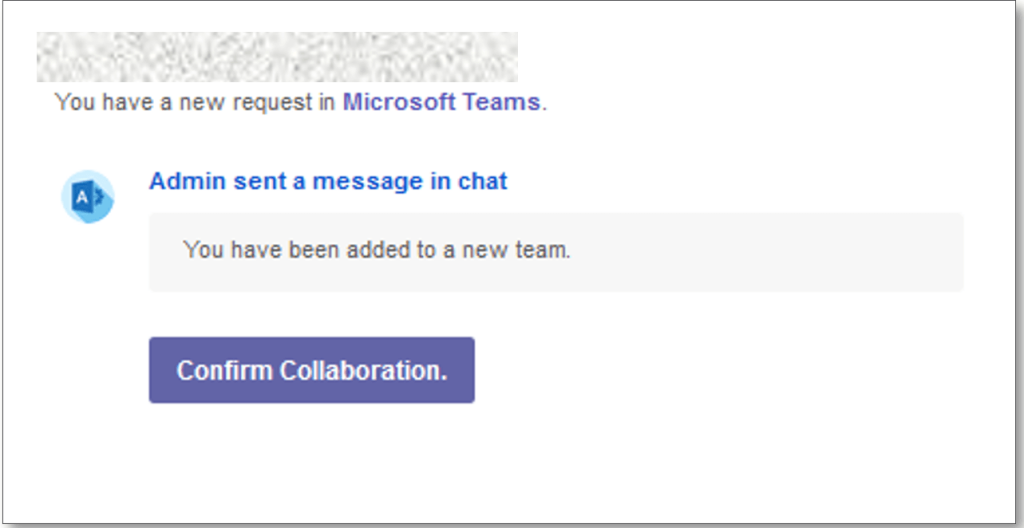
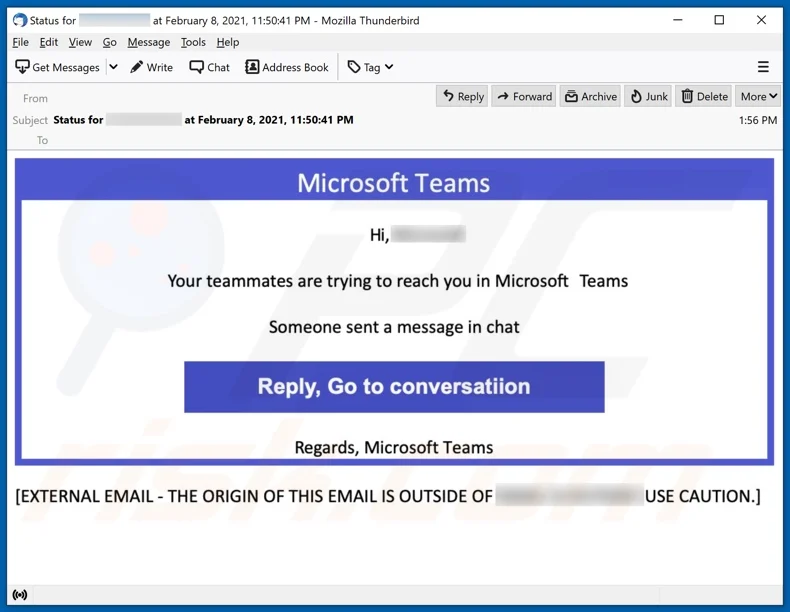
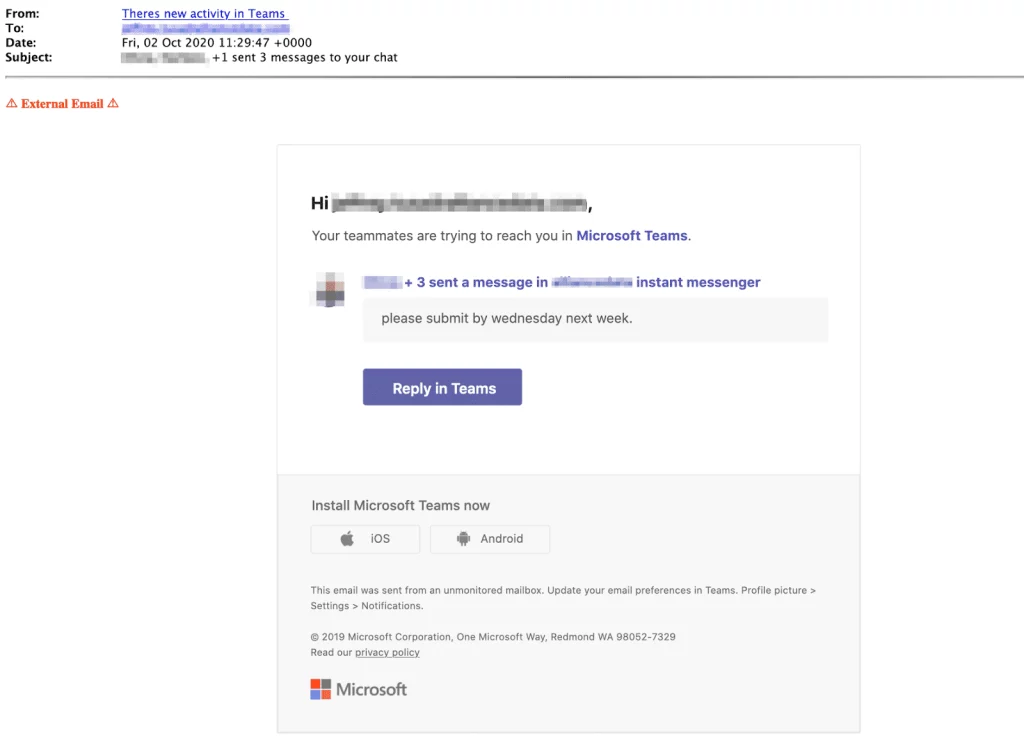
❓ Can You Spot the Phish?
Which of these messages is suspicious?
“🔒 Security Notice: Due to unusual activity, please verify your credentials via this secure Microsoft link: bit.ly/ms-login-urgent”
“📅 Join your scheduled meeting: https://teams.microsoft.com/l/meeting-id”
“🛠️ Remote support tool download: https://tools-corp.support/files/remote_assist.exe”
🛑 Correct Answer: 1 and 3 are phishing messages. Only the official Microsoft Teams link (2) is safe.
Microsoft Teams is here to stay, especially as Skype for Business sunsets. However, with great collaboration power comes great responsibility. Organizations must adapt their security awareness, architecture, and detection strategies to protect the new digital workplace.



