
Anubis ransomware is a new RaaS combining file encryption and data wiping. Learn about its dual-threat tactics, recent attacks.
The Anubis malware is a relatively new threat that is dominating the headlines because of the dual methods it uses. Anubis does not only have the ability to encrypt files like common variants of malware. Instead, it will encrypt files and delete them. Therefore, even when the user pays for the decryption key, the files will not be recovered because the malware will delete them.
Further, this ransomware is considered to be a Ransomware-as-a-Service (RaaS), which means that it is maintained by a group that uses affiliated actors to launch attacks to benefit from the profits.
What is Anubis Ransomware?
- Anubis is a Ransomware‑as‑a‑Service (RaaS) operation.
- It appeared in late 2024, originally tracked as Sphinx.
- It uses ECIES encryption with unique keys per victim.
- Anubis performs double extortion through data theft.
- Victims are threatened with public data leaks.
- It includes a wiper module.
- /WIPEMODE can permanently destroy files.
- Recovery may be impossible even after payment.
- Shadow copies and backups are deleted.
- Security and database services are terminated.
- Files are renamed with the “.anubis” extension.
- Custom ransom notes are dropped.
- Delivery is mainly through phishing emails.
- Fake documents and installers are commonly used.
- Affiliates earn up to 80% of ransom payments.
- Targets include healthcare, engineering, and enterprises.
- Anubis is designed for maximum financial and operational impact.
Origins and RaaS Operation of Anubis Ransomware
Anubis is a young ransomware family, which was first detected in late 2024. Security experts have found the emergence of Anubis as the time when the leaders of this group have started joining the cybercrime forums in December 2024. In early 2025, Anubis started promoting an affiliate program in the Russian cybercrime forums, which provided lucrative terms to its participants.
What is particularly interesting is that it is not part of any malware family with the same name. (There has been an Android banking trojan and a “Anubis” backdoor with a different family in the past, but they are not related to this ransomware package either.) The Anubis ransomware service has been created from scratch as a criminal enterprise. The criminals even developed a beta version called “Sphinx” before launching it as Anubis.
ANUBIS NETWORK
// RaaS AFFILIATE OPERATIONS //
Encryption Ops
AFFILIATE: 80% ANUBIS: 20%Data Extortion
AFFILIATE: 60% ANUBIS: 40%Initial Access
AFFILIATE: 50% ANUBIS: 50%Flexible Affiliate Program: Anubis has an affiliate program that uses the RaaS affiliate model and is highly flexible compared to those used by other malware groups. The group’s administrators allow the affiliates to negotiate payment percentages that differ from the typical file encryption ransom payments. For instance, the default ransomware program allows the affiliates to earn 80 percent of all payments made with Anubis charging 20 percent, while another program allows 60-40 split payment with an access-for-sale program offering 50-50 split profits sharing.
This means that the criminals can work together with Anubis to either use the ransomware directly or to monetize the stolen data as Anubis offers this service through its platform. This kind of business acumen indicates how today’s ransomware gangs function as a startup. However, they even innovate their “business plans.” Moreover, all these applications can be managed through an online control panel as well as professional marketing posts on the cybercrime forums.
Dual-Threat Attack: Encryption & Data Destruction
Anubis’ “wipe mode” feature that makes it stand out from other forms of ransomware. Anubis not only possesses the capacity to encrypt files but also goes ahead to erase them. The feature allows it to leave the victim with empty files that are unrecoverable even when a ransom has been paid. The uniqueness of Anubis has earned it the name “dual-threat” ransomware.
This puts the victims under immense pressure. The attackers can encrypt all the data and threaten the victim to pay, or they will suffer the loss of data, leading to the downfall of the organization’s operations.
DUAL-THREAT ARCHITECTURE
1. Encryption Mode
Utilizes ECIES (Elliptic Curve) to lock assets. Appends .anubis extension and deploys custom branding across the OS.
2. Wiper Mode
The “Kill Switch.” Irreversibly erases file contents, leaving 0 KB shadows. Data is gone even if the ransom is paid.
Operational Impact
Anubis shifts from “Double Extortion” to Permanent Digital Destruction. By destroying data while demanding payment, it applies maximum psychological pressure on victims.
It uses ECIES (Elliptic Curve Integrated Encryption Scheme) for protecting encryption keys, and it is coded using the Go programming language. The malware uses its own Anubis logo as icons for files, as well as wallpaper, and it also appends an ‘.anubis’ file extension once it encrypts the files.
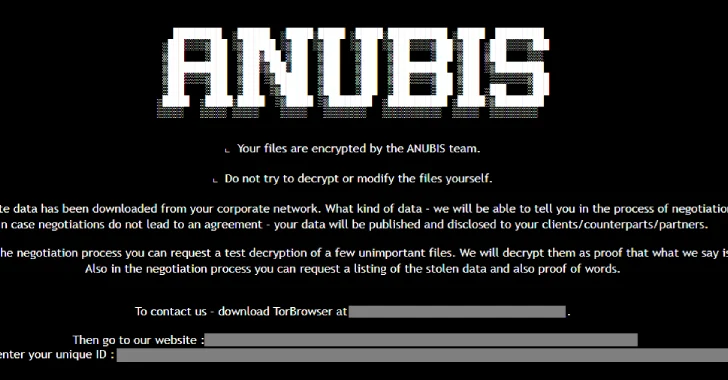
The victims are given a ransom note, which is named “RESTORE FILES.html.”
However, what makes Anubis particularly dangerous is its “wiper.” Once activated, the “wiper” deletes the file contents following encryption and reduces files to “0 KB.” Even if backups or a decryption tool are available, important files could already be lost, and that’s why Anubis is more than a ransomware – it’s a permanent digital destroyer.
Real-World Attacks and Impact on Victims
- Global victim base (2025): By mid-2025, Anubis had listed at least 7 victims on its leak site across healthcare, engineering, construction, and hospitality sectors.
- Geographic spread: Victims confirmed in the United States, Canada, Australia, and Peru, showing no regional or industry focus.
- Australia – Healthcare breach (Nov 2024): A medical center was compromised, with patient data exfiltrated and later leaked after ransom demands were refused — exposing highly sensitive medical records.
- Canada Data theft (Dec 2024): A Canadian organization suffered data theft and public leaks after failing to pay the ransom.
- Double-extortion model: Anubis not only encrypts files but also steals and publishes data, increasing legal and reputational damage.
- Wipe mode threat: If enabled, Anubis can permanently destroy encrypted files, making recovery impossible for organizations with weak backups.
- High operational maturity: Analysts believe Anubis is run by experienced ransomware operators, possibly ex-members of older groups, based on their affiliate program and professional victim negotiations.
- Growing threat: Its data theft + data destruction model could make Anubis a trend-setter for future ransomware campaigns.
Throughout this attack chain, Anubis exhibits a professional level of coding and operational security. It operates in stages, checks for privileges, evades defenses, and maximizes impact. These techniques correspond to well-known tactics in the MITRE ATT&CK framework used to describe adversary behavior.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
Anubis attacks typically start like many other breaches through phishing emails. The group uses spear-phishing messages with malicious attachments or links to gain an initial foothold. Because human error is often the weakest link, this social engineering tactic has been effective.
| Tactic | Technique | Description |
|---|---|---|
| Initial Access (TA0001) | T1566 | Phishing: Uses malicious emails with fake business documents or links to deliver the Anubis ransomware. |
| Execution (TA0002) | T1059 | Command-Line / Script Interpreter: Executes the ransomware binary with command-line flags to control encryption, wipe mode, and target directories. |
| Privilege Escalation (TA0004) | T1134.002 | Token Manipulation: Checks and attempts to relaunch itself with administrator privileges using low-level disk access tests. |
| Defense Evasion (TA0005) | — | Disables security products, backup services, databases, and applications to prevent detection and file locking. |
| Discovery (TA0007) | — | Scans the file system and selectively targets valuable business and user data while skipping system and developer directories. |
| Impact (TA0040) | T1486 / T1490 | Encrypts data using ECIES and deletes Volume Shadow Copies to prevent system recovery. |
| Impact: Destruction (TA0040) | T1485 | Data Destruction: If wipe mode is enabled, encrypted files are overwritten, making recovery impossible. |
Throughout this attack chain, Anubis exhibits a professional level of coding and operational security. It operates in stages, checks for privileges, evades defenses, and maximizes impact. These techniques correspond to well-known tactics in the MITRE ATT&CK framework used to describe adversary behavior.
Case Study: Xcitium vs. Anubis Ransomware
This demonstration shows how Xcitium protects systems from ransomware in real time. Multiple real-world Anubis ransomware samples were executed, simulating a live attack scenario. Instead of relying on signatures or cloud lookups, Xcitium’s patented Zero-Dwell platform automatically identifies every unknown process and isolates it immediately, preventing any interaction with the operating system.
As a result, the ransomware cannot encrypt files, establish persistence, or communicate with its command-and-control infrastructure. Even previously unseen threats are stopped before they can cause harm.
By eliminating the window of exposure, Xcitium ensures continuous protection, keeping systems secure, data safe, and operations uninterrupted. This video highlights how advanced threats like Anubis are neutralized instantly, demonstrating the effectiveness of Xcitium’s proactive security approach.
Indicators of Compromise (IOCs)
- Encrypted file extensions:
.anubis,.anb - Ransom note files:
RESTORE FILES.html,HOW_TO_DECRYPT.txt,RECOVER_DATA.html - File system artifacts: files renamed with
.anubis, file icons replaced with Anubis logo, and in wipe mode many files showing 0 KB size while still existing - Malicious processes:
anubis.exe,svc-anubis.exe, or randomly named Go-compiled executables running from user or temp directories - Command-line indicators: execution with
/WIPEMODEargument to trigger destructive wiping - Backup deletion activity:
vssadmin delete shadows /all /quiet,wmic shadowcopy delete,bcdedit /set {default} recoveryenabled No - Registry persistence:
HKCU\Software\Anubis,HKLM\Software\Microsoft\Windows\CurrentVersion\Run\Anubis - Network indicators: outbound HTTPS connections to attacker-controlled C2 servers, suspicious DNS lookups to newly registered or random-looking domains, unexpected Tor or proxy traffic
- Known malware hashes (SHA-256):
271998018494403a9b5d0d4b01eb0c44,8a12e997e672b80319c5b852b237e5a9,f71d8db7fda7659718330efcbd0776f0,0f1b8aa83e5f9c40ad32561a95ed2c67
Anubis Ransomware SHA-1 Samples & Zero‑Dwell Threat Intelligence Reports
Conclusion: When Ransomware Is Designed to Destroy, Prevention Is the Only Defense
Anubis represents a dangerous evolution in ransomware strategy. By combining strong encryption with deliberate data wiping, it removes the last safety net victims often rely on. Payment does not guarantee recovery. Backups are erased. Operations can be permanently crippled. This is not just extortion, it is intentional destruction, designed to maximize pressure and irreversible damage.
Why This Threat Changes the Stakes
Traditional ransomware still leaves room for recovery. Anubis does not.
- Encrypted files are deliberately reduced to zero bytes
- Backups and shadow copies are systematically removed
- Recovery may be impossible even after ransom payment
- Business continuity, not just data, is the real target
Any organization that allows unknown code to execute is exposed to permanent loss.
Where Xcitium Changes the Outcome
For organizations using Xcitium Advanced EDR, Anubis never reaches its destructive phase.
- Unknown ransomware processes are isolated at execution
- Encryption routines cannot touch real files
- Wipe commands cannot destroy production data
- Code can run without being able to cause damage
The attack collapses before data is altered, erased, or held hostage.
Protect What Cannot Be Rebuilt
When ransomware is built to erase, response is too late. Prevention must happen at execution.
Protect your data before it is encrypted.
Protect your business before it is erased.
Choose Xcitium Advanced EDR.




