Discover the critical RCE vulnerability CVE-2025-59470 in Veeam Backup & Replication. Learn about its impact, exploitation risks, and essential patching steps to protect your data infrastructure.
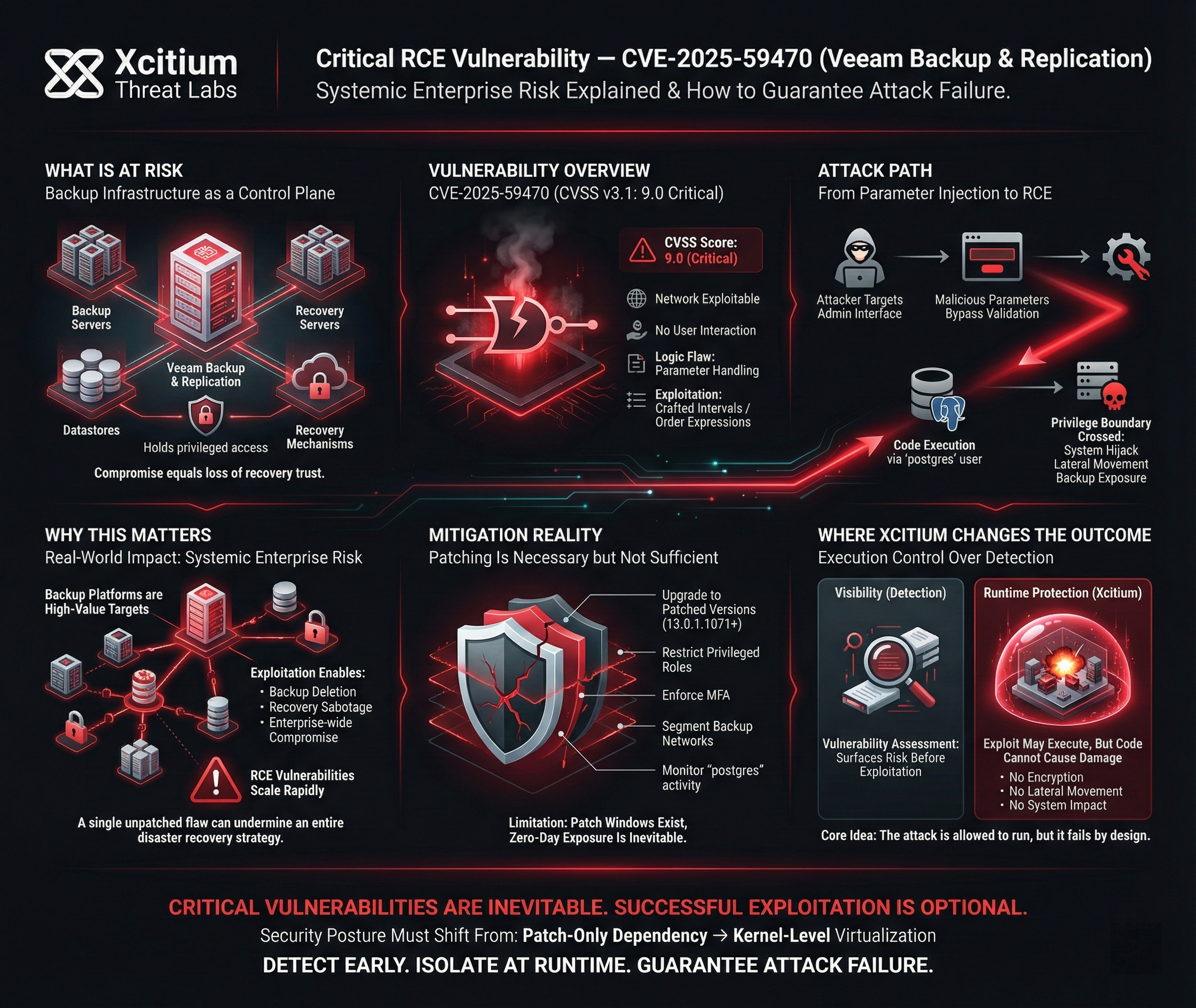
Recently, a critical RCE risk in Veeam Backup & Replication was revealed. This is one of the staples of disaster recovery for protecting organizational information. This vulnerability identified as CVE-2025-59470 and a CVSSv3.1 base score of 9.0.
It therefore becomes imperative for all users who are affected by the software to take immediate measures. The flaw that has been identified has the potential to give hackers control over the back up servers.
Understanding CVE-2025-59470: A Deep Dive
In essence, CVE-2025-59470 allows highly privileged users, who in this case are users with the role of either Backup Operator or Tape Operator, to execute arbitrary code that runs because of the operation of postgres in the backup server system as the postgres user. This particular flaw arises from the mishandling of specially crafted parameters that include things like interval or order expressions in an application.
This is a network-exploitable vulnerability, which means the attacker doesn’t necessarily have to have direct physical access to the system in order to attack it. The attack type targets the application’s logic for parsing parameters, which doesn’t validate inputs from administrative users properly.
Consequently, it would enable an attacker to elevate privileges from the application domain to dominion over the database service. This would culminate in lateral movement, data extraction, and even the destruction of important data backups.
The Real-World Threat: Why This Matters
- Veeam Backup & Replication has a strong position as a market leader in the area of backup software and, therefore, it’s a very attractive target for hackers.
- Advanced threat actors like ransomware operators and APTs are actively targeting environments used by Veeam.
- CVE-2025-59470 has not been observed to be exploited in the wild yet, but given past precedents, once technical details and/or proof-of-concept attacks become available, it will likely be rapidly exploited by attackers.
- Backup infrastructure is a common attack surface, as evidenced by the fact that Rapid7 stated that more than 20% of its 2024 incident response engagements included Veeam access and/or exploitation.
- Remote Code Execution (RCE) vulnerabilities can cause massive, global impact if left unpatched.
- A new RCE vulnerability in WatchGuard recently affected more than 115,000 firewalls, and this is just one example of how quickly vulnerabilities such as this one can be used in large-scale attacks.
- Unpatched critical vulnerabilities in widely used products introduce systemic risks in enterprise environments.
Essential Mitigation Strategies and Best Practices
The first and most important step in addressing CVE-2025-59470 is to apply an update to utilize Veeam Backup & Replication Version 13.0.1.1071 or later. The new release contains patches for all known vulnerabilities to provide your environment with an improved level of protection. Nevertheless, patching is not a sole means to protect your environment.
Effective mitigation strategies will require a multi-layered approach:
- Strict Access Control: The Backup Operators and Tape Operators roles must be strictly limited to the most trusted individuals. Multi-factor authentication for all administrative logins must be enforced.
- Network Segmentation: Isolate Veeam Backup & Replication servers from untrusted networks. Ensure they are accessible only by necessary personnel and through secure channels.
- Continuous Monitoring: Audit the logs for unusual activity. Investigate unexpected scheduled job executions, unauthorized changes to backup config files, and running processes with the postgres user id. Such behavior might indicate attempted or successful exploitation.
- Zero Trust Principles: Implement the principles of Zero Trust in the backup environment. This assumes the lack of trust inherently and checks all attempted accesses, regardless of source.
Related Vulnerabilities Addressed in the Patch
It is worth mentioning that the recent patch, version 13.0.1.1071, has remediated other severe vulnerabilities apart from CVE-2025-59470. These include:
- CVE-2025-55125: An RCE vulnerability allowing root access via a malicious backup configuration file (CVSS 7.2).
- CVE-2025-59468: Another RCE flaw enabling postgres user access through a malicious password parameter (CVSS 6.7).
- CVE-2025-59469: An arbitrary file write vulnerability that could grant root privileges (CVSS 7.2).
These extra patches reinforce the need for the general update. They all work together in creating more security for your Veeam infrastructure. Being up-to-date is an on-going process as far as the dynamic world of threats is concerned.
Conclusion: When One Control Is Not Enough
CVE-2025-59470 reinforces a hard truth in modern infrastructure security.
Critical vulnerabilities are not rare events. They are inevitable. What matters is whether they are discovered in time and whether they can be abused when they are not.
Why This Exposure Matters
Backup and recovery platforms sit at the center of enterprise resilience. When an RCE vulnerability exists in systems like Veeam, the impact goes far beyond a single server:
- Backup infrastructure becomes an entry point for full environment compromise
- Ransomware operators gain direct access to recovery mechanisms
- Patch delays turn into operational and financial risk
- A single exploit can undermine an entire disaster recovery strategy
Where Xcitium Changes the Outcome
Effective defense requires two complementary controls, each addressing a different failure point.
- Xcitium Vulnerability Assessment ensures this flaw should have been visible.
It identifies exposed versions, highlights critical misconfigurations, and surfaces risk before attackers do. - Xcitium Advanced EDR ensures that even if the vulnerability exists, the attack cannot succeed.
Exploit code may execute, but code can run without being able to cause damage.
No encryption. No lateral movement. No system impact.
One product exposes the risk.
The other guarantees the failure of the attack.
Build Resilience Before Exploitation Begins
Patching is essential, but it is never instant. Visibility without protection is incomplete. Protection without visibility is reactive.
Secure critical infrastructure by detecting vulnerabilities early and neutralizing exploits at execution.
Choose Xcitium Vulnerability Assessment and Xcitium Advanced EDR.




