Recently, Iran imposed a sweeping internet blackout to stifle nationwide protests. This post examines how Tehran enforced the digital lockdown, its impact on communication and society, and the broader cybersecurity implications of this unprecedented censorship.
Nationwide Internet Shutdown amid Record Protests
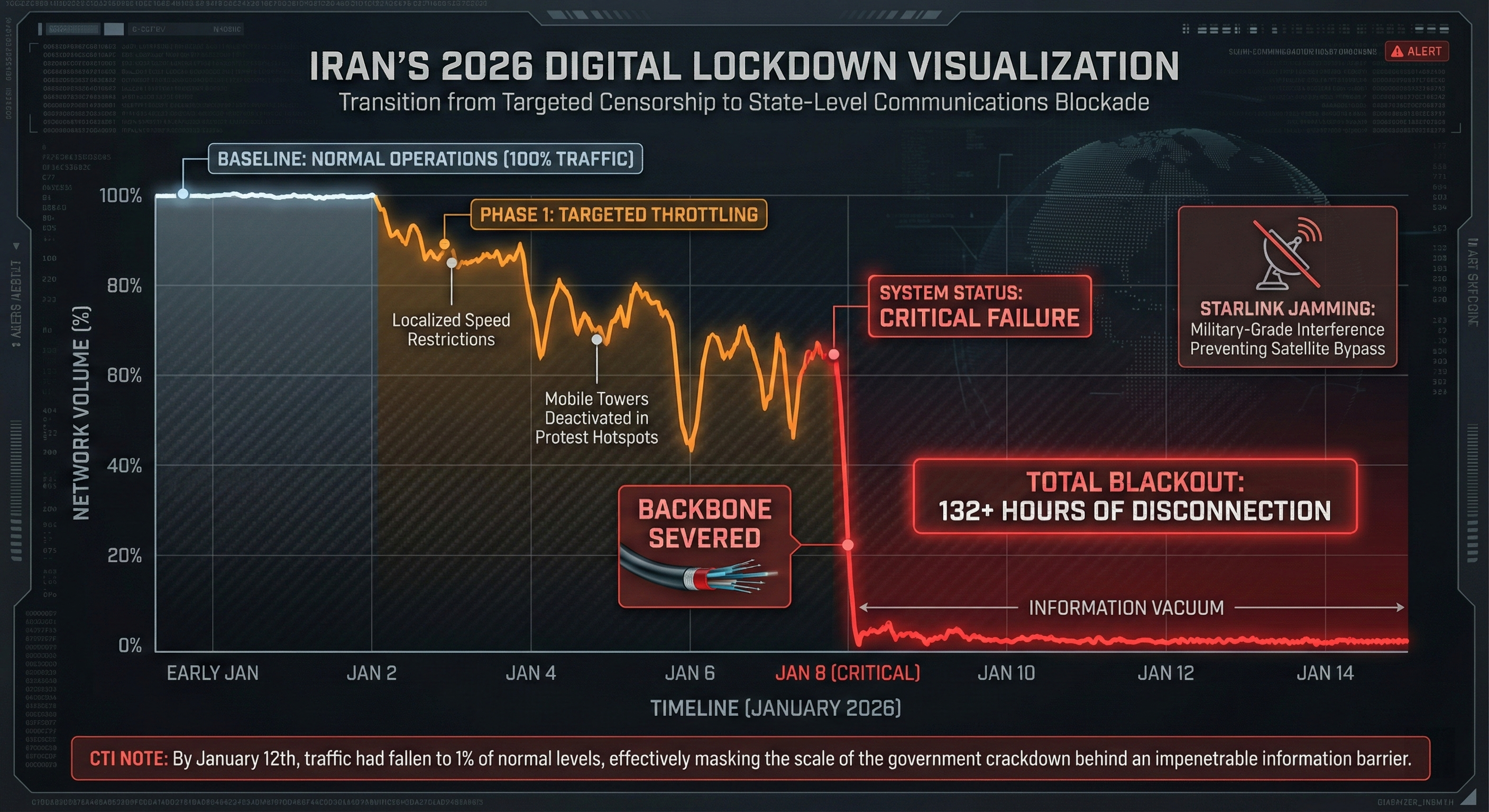
Recently, as a result of what has been described as “one of the biggest anti-government protests in years,” a digital lock down was imposed on Iran by its government. The Iranian government severed all internet and telecommunication lines across the country as a means of preventing information regarding the protests from leaking out. It has been reported that on January 8th, internet services across Iran went down as a result of calls by protesters demanding a change of government. This could be considered a turning point because RFE/RL has indicated that “Iranian authorities continue to block access to the internet as part of their crackdown on anti-government protests.”
In truth, Internet monitors noted that as of January 12th, Internet traffic was down to about 1% of normal levels. This meant that there was very little, if any, independent information escaping the country. NetBlocks pointed out that the unprecedented shutdown had now lasted over 132 hours, and further noted that reported casualties were likely underestimated because they were “masked by the absence of connectivity”. Effectively, Iran’s digital shutdown left citizens and the world at large in the dark about what’s been happening.
Technical Tactics: Internet Throttling, Blackouts, and Jamming
Censorship in Iran involved many technical approaches. Some of these included:
- Targeted throttling: The government began to deliberately reduce internet speeds and turned off mobile communication base stations around areas of protests.
- Nationwide blackout: A nationwide blackout was ordered on January 8, cutting most of the fiber optic backbone cables, resulting in the death of landlines and cellular communication across the nation. By the afternoon, the monitors were able to verify that Iran was “in the midst of a nationwide internet blackout,” with the usual traffic reduced to nearly zero.
- Satellite jamming and bans: Iran used military satellite jammers to saturate the signals of the SpaceX Starlink satellite network, resulting in as much as 80% packet loss. This led to the suspension of the Starlink satellite internet service in Iran by SpaceX. In addition to that, satellite internet was prohibited by the regime in Iran.
These measures illustrate a broad censorship toolkit from localized throttling to kinetic jamming designed to sever Iranians from both domestic and global networks.
Starlink, Jamming, and the Limits of Satellite Resilience
Iran’s Starlink jamming campaign challenged the belief that satellite internet is immune to censorship. Reports of up to 80% packet loss showed that LEO satellite networks can be strategically degraded. Satellite internet is no longer neutral infrastructure it is now a conflict asset.
Space as a Cyber Domain
Once satellite networks are used for crisis communication and coordination, they become targets for:
- RF jamming
- Signal interference
- Ground terminal seizures
This places satellite providers squarely inside the cyber conflict landscape.
Implications for Cyber Resilience
Iran’s actions highlight a future where:
- Cyberwar includes RF and space-based attacks
- Resilience requires multi-layered connectivity, not a single “uncensorable” solution
Cybersecurity planning now extends beyond terrestrial networks into orbit.
COLLATERAL DAMAGE
ISOLATION
DISCONNECTEDFamilies severed. Zero news access. National silence and total communication blockade.
PARALYSIS
CRITICALBanking frozen. Flights canceled. Hospitals struggling without essential digital connectivity.
VACUUM
MASKEDVerification impossible. Scale of crackdown hidden behind an impenetrable information barrier.
Consequence on Communications & Daily Life
The lockdown had immediate, far-reaching impacts on daily life:
- Communication blackout: The internet and telephones were disconnected. People found themselves cut off from the world, having no way to get news or even reach their loved ones.
- Services affected: The digital infrastructure literally ground to a halt. Online banking and electronic payments as well as various business activities came to a standstill. Even international flights to Iran were canceled. Public services such as hospitals and pharmacies were affected by the lack of connectivity.
- Information vacuum: In the absence of government-controlled media, news and testimony had to come through the hard work of witnesses and journalists who took risks to get the word out. “The extended blackout masked the true extent of the crackdown,” said monitors, who found it “exceedingly difficult” to verify the information.
In other words, “the blackout served not only to isolate the population, it also clouded understanding of what was happening on the ground.”
The Cost of Internet Shutdowns to Iran: $1.5 Million Every Hour
In a broader sense, Iran’s shutdown shows how controlling the internet has become a strategic security tool. U.S. officials even discussed using “cyberattacks to disrupt the communication and decision-making systems of Iranian security agencies” in response to the crackdown. Globally, satellite internet has emerged as a battleground. Starlink has become a “critical tool” in conflicts from Ukraine to Myanmar, prompting regimes like Iran’s to deploy sophisticated jammers. Analysts also warn of the costs: prior research estimated each hour of blackout costs Iran about $1.5 million in lost revenue.
Overall, Iran’s internet blackout is part of a wider cyber-geopolitical struggle. It highlights the intersection of censorship, cybersecurity, and technology: as governments increasingly weaponize network outages, tools like satellite internet and encryption become key lines of defense and targets in modern conflicts.
Business Continuity Under Digital Siege
The Iranian blackout was more than an event in the civil domain; it was a stress test for business resilience. For MNCs in high-risk countries, this outage highlighted the vulnerability of connectivity as a single point of failure. Cloud-based ERP, online payments, HR, logistics tracking, and business communications went dark as soon as the national connectivity was disrupted. The latest business continuity plans take degraded access rather than total isolation as a premise.
Offline-First Operations
Organizations must adopt offline-capable architectures, including:
- Local ERP and inventory systems
- On-prem authentication and access control
- Store-and-forward data synchronization
In blackout scenarios, the ability to continue basic operations without internet access determines survivability.
Decentralized Communication
When Teams, Slack, and cloud email fail, alternatives matter:
- Mesh and peer-to-peer networking
- Delay-tolerant messaging
- Hybrid satellite-terrestrial comms
In modern geopolitics, business continuity has become a cyber warfare concern.
Conclusion: When a Nation Goes Offline, Risk Does Not
Iran’s 132 hour shutdown proves that connectivity is now a control surface. Throttling, full blackouts, and satellite jamming can collapse communication at national scale, driving traffic down to near zero and leaving citizens, businesses, and the outside world operating in an information vacuum.
Why This Matters for Security and Resilience
A state-level blackout is not only censorship, it is also a cyber resilience stress test.
- Critical services lose digital dependency chains, banking, payments, healthcare, logistics, and aviation all degrade fast
- Verification becomes nearly impossible, incident response slows, and situational awareness collapses
- Satellite connectivity is not a guaranteed bypass, it can be strategically degraded
- The economic impact is immediate, outages can translate into massive hourly losses
What Organizations Should Learn
In high-risk regions, continuity planning must assume degraded access, not normal operations.
- Offline-capable systems for core workflows
- Decentralized communication options when cloud email and chat fail
- Store-and-forward synchronization for recovery once access returns
Where Xcitium Changes the Outcome
A blackout creates the perfect cover for opportunistic intrusion, malware delivery, and destructive follow-on activity. With Xcitium Advanced EDR, those attempts fail at execution.
- Untrusted payloads are intercepted the moment they run
- Code can run without being able to cause damage
- Lateral movement and destructive impact are blocked before operations are disrupted further
If you have Xcitium in place, the attacker cannot turn a connectivity crisis into a successful compromise.
Build Continuity for the Next Digital Siege
Geopolitics can take networks down without warning. Resilience requires offline-first architecture, alternative communications, and security that prevents execution-based damage when visibility is at its worst.