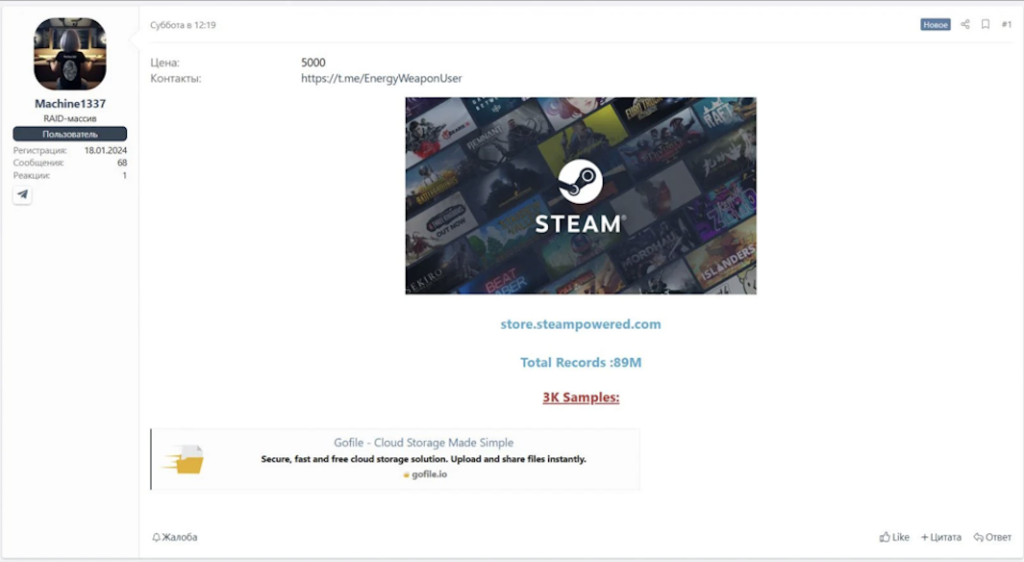
In mid-May 2025, alarming reports circulated online claiming that 89 million Steam user accounts had been breached. A dark-web seller using the alias Machine1337 (also known as EnergyWeaponUser) posted a forum advertisement offering a database of “89M” Steam records – phone numbers and one-time 2FA text codes – for just $5,000. The screenshot below even shows the Steam logo and “Total Records: 89M.” Security monitors quickly picked up the story: for example, the threat actor’s sales pitch and sample data were reported by BleepingComputer on May 13.
However, closer analysis revealed this was not a new Steam hack. Experts found that the only data shown in the sample were expired SMS two-factor codes and phone numbers – not passwords or payment details. As Valve later explained, “we have examined the leak sample and have determined this was NOT a breach of Steam systems”. In fact, the leaked records were just old 2FA text messages (valid for only 15 minutes) and recipient numbers. In short, even if genuine, these data alone can’t let anyone log into Steam accounts.
Timeline: Discovery & Investigation
The supposed breach story emerged around May 13–14, 2025. A LinkedIn post by security firm Underdark.ai alerted the community to a dark-web listing of 89M Steam records. News sites like BleepingComputer, PCWorld and TechRadar reported the claim that a hacker was selling Steam account data on a forum. These outlets noted that 3,000 sample records were shared, containing nothing more than SMS login codes and numbers. Importantly, Twilio – the SMS provider implicated by the seller – told BleepingComputer it had “not found any evidence of a breach or leak”. By May 15, 2025, Valve had officially weighed in.
Valve’s Official Response
Valve moved quickly to quash the rumors. In a Steam community news post and comments to media, the company stated unequivocally that “no Steam systems have been breached”. Valve’s statement explained that the only data involved were old one-time SMS codes and phone numbers, not linked to any Steam account or personal data. As Valve wrote: “The leak consisted of older text messages that included one-time codes… The leaked data did not associate the phone numbers with a Steam account, password information, payment information or other personal data”. They emphasized that expired SMS codes cannot be used to compromise accounts. Valve also advised users that no password or email changes were needed due to this incident , and encouraged everyone to enable the Steam Mobile Authenticator (app-based 2FA) for extra security.
Multiple news outlets quoted Valve’s clarification. For example, GameSpot reported Valve’s statement that the incident was “NOT a breach of Steam systems” and that any leaked codes came from the text-message 2FA service, not Valve’s own databases. WindowsCentral similarly summarized Valve’s response: the leaked data were just 2FA text logs with no account links, and “customers do not need to change their passwords or phone numbers” because of it.
Nature of the Exposed Data
What exactly did this data contain? All sources agree it was nothing like usernames or passwords. The leaked sample comprised SMS verification codes and phone numbers from Steam’s 2FA system. Valve and analysts pointed out that these codes were already expired when leaked. As PC Gamer paraphrased Valve: “those codes are only active for 15 minutes and aren’t tied to your Steam account… the only thing they do include is a phone number”. A German tech site (Heise) found that the sample had “phone numbers and (expired) one-time codes, but no references to access data such as user name, Steam ID or even password hashes”. In short, no sensitive personal information was exposed.
Even the phone numbers alone aren’t directly useful for account access on Steam, since Valve confirmed there’s no link in the data between a phone number and a Steam account. Valve noted that anytime a text code is used to change an email or password, the account owner also gets an email/Steam notification – so unexpected codes would trigger alerts. In practice, the consensus is that the exposed data posed no immediate threat to Steam accounts beyond the usual phishing risks.
Possible Source of the Leak
The true origin of the data remains uncertain. The seller Machine1337/EnergyWeaponUser claimed to have stolen it, but it’s unclear where it came from. Some analysts suspected an intermediary SMS service. For example, WindowsCentral noted that Underdark.ai speculated the logs came from Twilio (which handles 2FA SMS for many companies). However, Twilio firmly denied any breach of its systems. Valve also stated it has no partnership with Twilio for Steam codes , suggesting that the logs likely came from some other SMS gateway or were scraped by a rogue employee or partner. The attacker’s identity beyond the forum pseudonym is unknown. (Notably, media pointed out that EnergyWeaponUser had been linked to other data dumps before , but no direct proof ties them to any exploit here.)
In summary, who was responsible for obtaining the data isn’t confirmed. The important point is that it was not due to a hack of Steam’s own servers. Valve is reportedly still looking into where the leaked SMS logs originated, but the company says Steam’s infrastructure was not compromised.
Recommended Actions for Users
Despite no breach at Steam, this scare is a good reminder to tighten account security. Valve and security experts recommend the following steps:
- Enable the Steam Mobile Authenticator. Using the app-based Steam Guard is more secure than SMS codes. If you haven’t already, turn on the Steam Guard Mobile Authenticator in your Steam settings.
- Use a strong, unique password. Even though no passwords were leaked, it’s wise to ensure your password is robust (consider a password manager to generate and store one). Changing an old or reused password can’t hurt.
- Review authorized devices. Check the list of devices/active sessions in your Steam account and remove anything unfamiliar. This helps ensure no one else is accessing your account.
- Be wary of phishing. Treat any unexpected verification codes, password-reset emails or Steam chat messages with suspicion. Valve explicitly advises ignoring account security messages you didn’t initiate. Do not click untrusted links in Steam messages or emails.
- Monitor your account. Keep an eye on your Steam account activity and email for any irregular login alerts. Valve will notify you if your password or email address is changed, and those should not happen without your consent.
Following these standard security practices will protect your account regardless. Importantly, Steam has not asked users to change passwords because of this incident , and there’s no evidence hackers have your credentials. But enabling strong 2FA and good password hygiene is always recommended.
In short, “Steam data breach” turned out to be a false alarm. Reports of 89 million breached accounts were based on a misinterpreted sample of old SMS 2FA codes and numbers, not an actual compromise of Steam’s database. Valve’s official communications make it clear: Steam was not hacked, and no user passwords or financial data leaked. Affected users should remain vigilant (enable 2FA, use strong passwords) but need not panic or frantically change credentials due to this incident. All credible sources – from PCWorld to GameSpot to Valve’s own blog – reinforce that the reported breach was “not a real Steam hack”. Steam players can therefore breathe easy, knowing their accounts remain secure, while continuing to follow good security practices.
Sources: We relied on reports from security news outlets and Valve’s official statement to compile this account. These include TechRadar, PCWorld, BleepingComputer, GameSpot, PC Gamer, WindowsCentral, and others. All agree that the supposed breach was a misinterpreted 2FA log leak, not a Steam server hack.