An authentication bypass (CVE-2026-24061) has left nearly 800,000 Telnet servers vulnerable. Discover the CVSS 9.8 flaw, its long-term impact, and how to secure affected devices.
Massive Telnet Exposure Worldwide
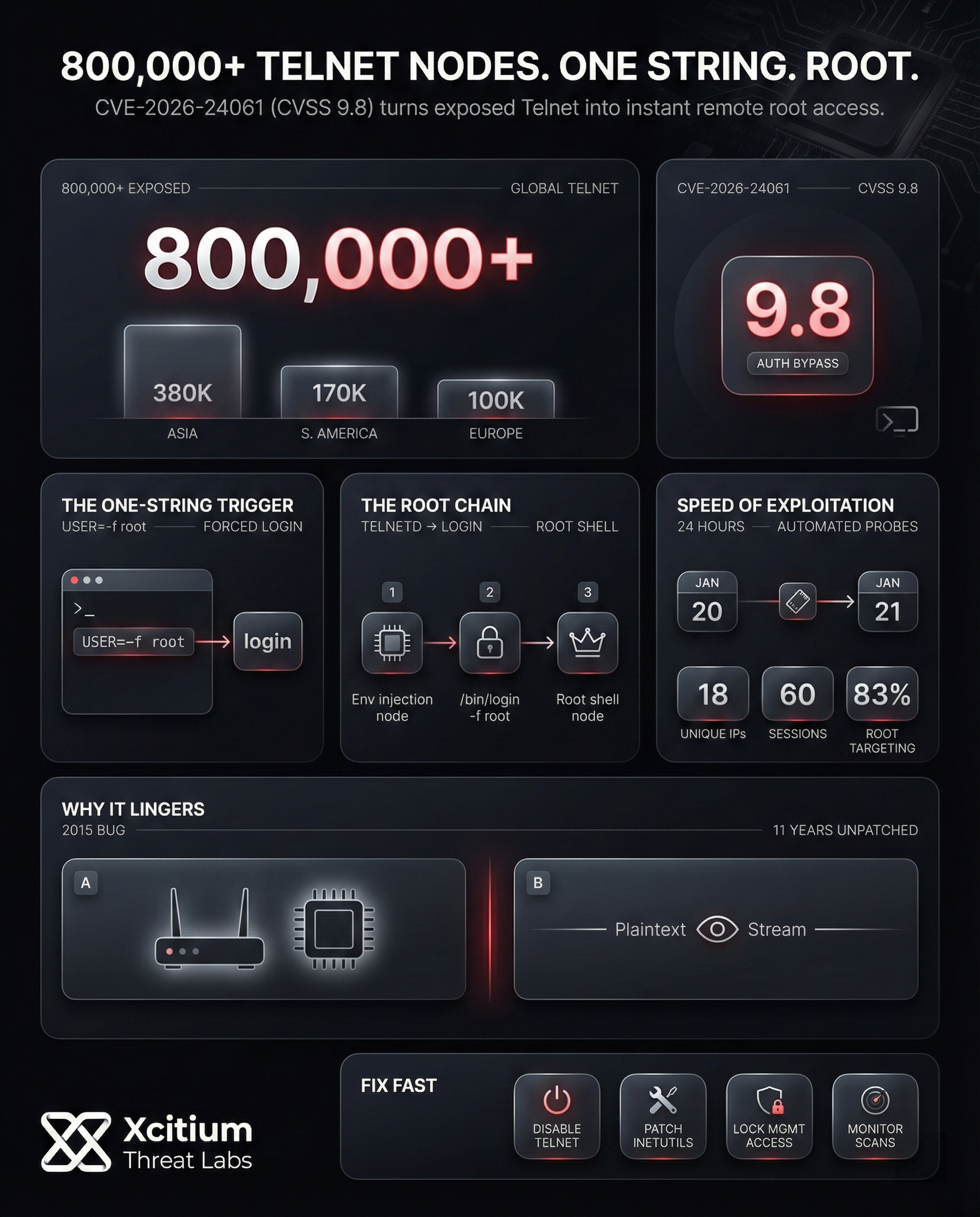
Telnet, a legacy and unencrypted protocol, remains widely exposed on the internet. In accordance with recent reports, nearly 800,000 Telnet-enabled hosts remain reachable on the internet, thereby posing a significant security risk.
Global Vulnerability Insights
Primarily legacy embedded devices.
Rarely patched or updated.
Most of these systems are older or embedded devices that rarely receive updates.
Critical Authentication Bypass in TelnetD
Lately, researchers announced a critical authentication bypass vulnerability, CVE-2026-24061, in the GNU InetUtils telnetd service. This vulnerability allows an attacker to obtain a root shell without a password using this flaw, which carries a CVSS score of 9.8. This vulnerability occurs because the telnetd service passes the client’s environment variable ‘USER’ to the system’s ‘login’ command. This allows an attacker to obtain a root shell without a password if the client sets ‘USER’ to ‘-f root’ when making a connection to the server.
- An attacker initiates a Telnet session and sets the ‘USER’ environment variable to ‘-f root.’
- The ‘telnetd’ service runs ‘/usr/bin/login -f root.’
- The ‘login’ command grants a root shell to the attacker.
CVE-2026-24061 Analysis
The attacker negotiates a terminal session by injecting USER=-f root into the environment variables.
The telnet daemon blindly passes the value to the login utility: /bin/login -f root.
The system’s login program interprets -f as “force login without password,” granting instant root privileges.
In this manner, any exposed Telnet server is immediately compromised when this vulnerability becomes known.
Why Telnet Remains a Risk
There are a number of reasons why this vulnerability has been lingering for such a long time. The Telnet protocol has been in existence for a long time, and many devices, both old and new, include it by default. Shockingly, the code vulnerability was introduced as recently as 2015 but has remained unpatched for almost 11 years. The fact that many routers and other devices are never updated means that this vulnerability has remained. Telnet sends everything, including passwords, in plain text.
Key reasons Telnet is still a weak spot include:
- Built-in Legacy Support: Many old systems include Telnet by default.
- Slow Patching: The code vulnerability has remained for more than a decade.
- Unencrypted Data: Telnet sends passwords in plain text, which is a problem in modern networks.
- IoT/Embedded Use: Vulnerable Telnet services can remain on devices that are rarely updated.
Exploitation in the Wild
No time was lost by the attackers after the vulnerability was made public. On January 21, 2026, which is one day after the patch was issued, at least 18 unique IP addresses started probing for the CVE-2026-24061 vulnerability in approximately 60 Telnet sessions. The attacks were made by sending USER=-f strings to force a root login. The majority, at 83%, were targeting the root.
Attack Activity Report
Key observations from early attacks:
- Immediate Scanning: The exploit attempts began within 24 hours after the disclosure.
- Root Targeting: 83% of the exploit sessions targeted the root.
- Automation: The majority of the exploit sessions were automated, with a few being done manually.
Any Telnet service that is reachable from the internet should be considered compromised.
Mitigation and Protective Measures
As such, the solution to the problem is to install updates or disable the service. The GNU InetUtils 2.8 release was issued on January 20, 2026. This release fixes the problem. So, the first recommendation is to install the updates on all affected machines. If updates are not immediately available, the service can be disabled by stopping the telnetd service. Experts recommend that the service can be replaced by SSH.
The recommended course of action is:
- Upgrade: Install GNU InetUtils 2.8 or higher.
- Disable Telnet: Disable the telnet service by using the following command: sudo systemctl disable telnetd.
- Block Port 23: Block the incoming connections on port 23.
- Switch to SSH: Use SSH for remote logins instead of Telnet.
Conclusion: A Single Legacy Port Can Become Mass Root Access
This Telnet flaw is a reminder that the most dangerous exposures are often the oldest ones. When an authentication bypass can grant remote root access, every reachable Telnet service becomes an immediate, automatable target, and at 800,000 plus exposed hosts, that risk is not theoretical.
Why This Threat Still Wins in Real Environments
Telnet persists in the places defenders patch the slowest, legacy servers, embedded systems, and inherited configurations. Once scanning begins, the window between disclosure and exploitation is measured in hours, not weeks.
Where Xcitium Changes the Outcome
For organizations using Xcitium Vulnerability Assessment, this exposure should be visible before attackers find it.
- Internet exposed Telnet services are identified and prioritized for remediation.
- Missing fixes and risky versions are flagged so teams can patch faster, or disable Telnet entirely.
- Attack paths are reduced early, because the best way to stop remote root is to remove the reachable entry point.
Close It Before It Spreads
Patch to fixed versions, disable Telnet, block port 23, and move remote administration to SSH. Then continuously verify that legacy access paths do not quietly return.