Discover how 175,000 Ollama AI servers are publicly exposed across 130 countries, posing significant security risks like LLMjacking. Learn about the threats and essential mitigation strategies.
The Unseen Vulnerability: A Global AI Exposure Crisis
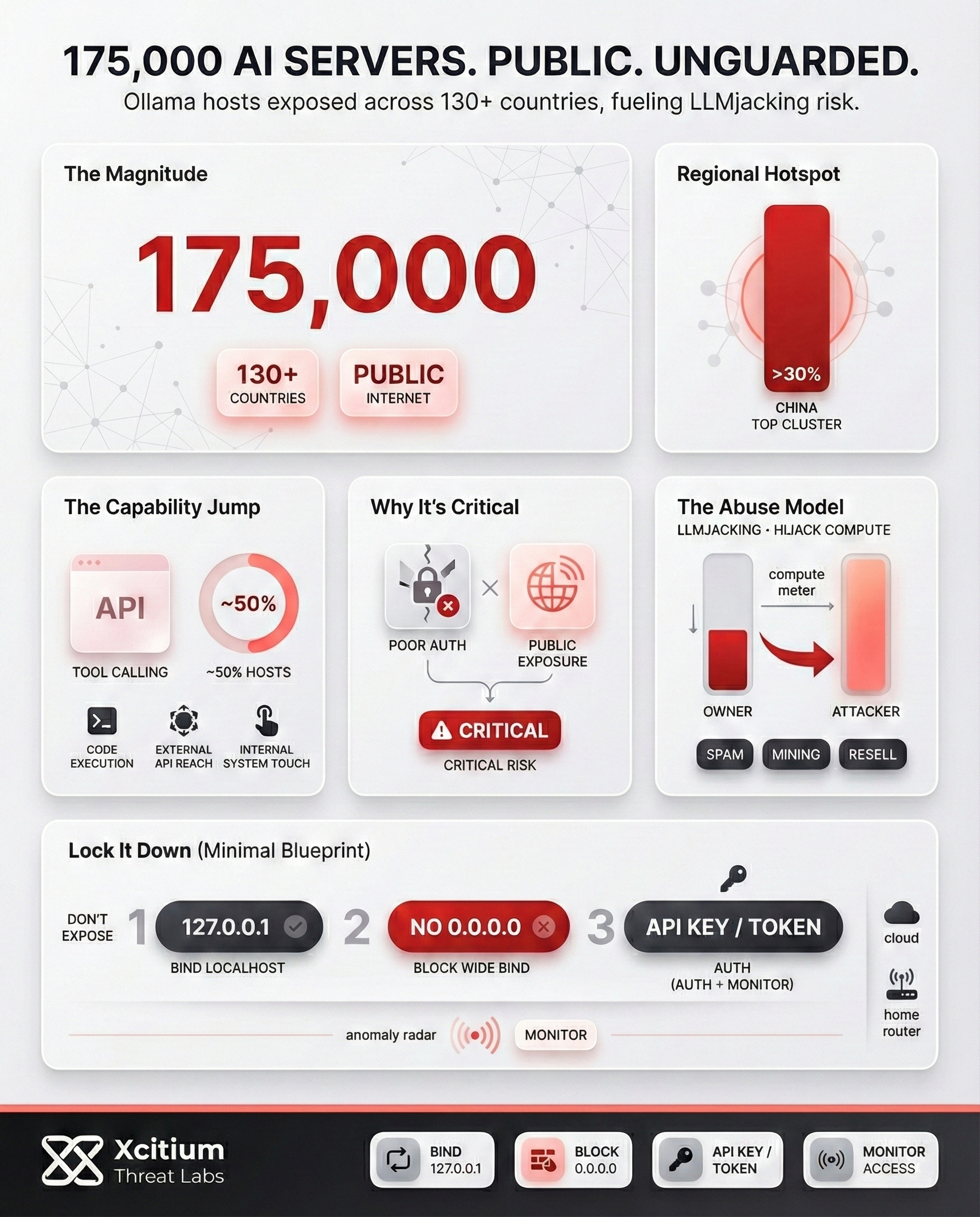
A joint investigation has recently revealed a major cybersecurity problem; a massive number of 175,000 Ollama hosts in 130 countries are publicly accessible. This is an unmanaged layer of artificial intelligence computing resources. These resources are operating without the security guardrails and monitoring typically provided by platform providers.
A recent investigation into global AI infrastructure has identified a staggering volume of unmanaged Ollama servers open to the public internet.
This exposure affects over 130 countries, creating a massive, unmanaged layer of AI compute infrastructure globally.
Over 30% of the identified instances are located in China, marking it as a primary zone of localized risk.
Unprotected resources are being exploited for “LLMjacking,” where cybercriminals hijack compute power for unauthorized AI workloads.
The Staggering Scale of Exposed AI Infrastructure
The number of exposed Ollama AI servers is staggering. These compromised servers are found in cloud infrastructures as well as home networks worldwide. It is noteworthy that China has the highest number of these compromised servers, which amounts to more than 30%. Other countries where there are a high number of these servers include the US, Germany, France, South Korea, India, Russia, Singapore, Brazil, and the UK. This goes to show that this is a worldwide problem, which calls for an international solution.
The Escalating Danger of Tool-Calling Capabilities
Crucially, close to half of these hosts have tool calling capabilities advertised through their API endpoints. Tool calling allows LLMs to execute code and access external APIs and systems. It is a game-changer for the threat model. While a text generation endpoint might be used to generate malicious content, tool calling is a different beast altogether. In this context, a combination of poor authentication and network exposure is considered the most severe threat by researchers today. In addition to this, some hosts also feature uncensored templates for their prompts.
The combination of insufficient authentication and public network exposure creates the most severe risk in the current AI ecosystem.
Tool-enabled endpoints allow models to execute code, access external APIs, and interact with internal systems.
Certain hosts utilize uncensored prompt templates, effectively removing built-in safety guardrails and filters.
While standard text generation may produce harmful content, tool-enabled exposure allows for active system exploitation and unauthorized interaction.
LLMjacking: The New Frontier of Cybercrime
The exposed nature of such systems makes them prime targets for a new form of cybercrime called LLMjacking. In this type of cybercrime, the resources of the victim’s LLM infrastructure are hijacked for the criminal’s own gain, making the victim bear the expense of such activities.
These illegal activities can vary from sending spam emails or engaging in disinformation activities to cryptocurrency mining or selling access to other criminal groups. The threat is not just hypothetical; a report by Pillar Security has identified the exploitation of exposed LLM service endpoints for a campaign called “Operation Bizarre Bazaar.” In this campaign, exposed endpoints are systematically validated and then sold for discounted prices on the silver.inc website.
Fortifying Your Defenses: Essential Mitigation Strategies
Therefore, to mitigate the extensive exposure of Ollama AI servers, a multi-faceted strategy must be adopted. In this case, organizations and individuals must consider employing robust security controls. To start off, there is a need to prevent exposing Ollama instances to the public internet. At this point, there is a need to configure Ollama to bind to 127.0.0.1, which represents localhost.
In addition, there is a need to prevent Ollama from binding to 0.0.0.0. In effect, there must be secure API key-based or token-based authentication mechanisms for any publicly accessible LLM server. There must be continuous monitoring of AI infrastructure for any unauthorized access and unusual activity. In effect, there must be new strategies to distinguish between cloud and residential infrastructure. In essence, LLMs, particularly LLMs that support tool-calling, must be treated like any other externally accessible infrastructure.
Conclusion: When AI Compute Is Public, It Becomes Someone Else’s Infrastructure
175,000 publicly exposed Ollama servers across 130 countries is not an edge case, it is a global attack surface waiting to be rented. When an LLM endpoint is reachable from the internet, the question is not if it will be abused, it is who will monetize it first.
Why This Threat Matters Now
Tool calling changes the risk class entirely. Nearly half of exposed hosts advertise tool-enabled APIs, which can enable code execution and interaction with external systems. That makes “LLMjacking” more than stolen compute, it can become an operational intrusion path.
Why So Many Environments Stay Exposed
Most incidents here are not advanced exploitation, they are basic exposure and weak control.
- Services bound to public interfaces instead of localhost
- Missing or weak authentication on LLM endpoints
- No continuous monitoring for abnormal usage patterns
- Tool-enabled APIs exposed without security guardrails
- Cloud and home deployments treated as “temporary,” then forgotten
Secure AI Infrastructure Before Attackers Start Billing You
Stop treating LLM servers as experimental tooling. Treat them as internet-facing infrastructure, reduce exposure, enforce strong access controls, and prevent hostile execution paths before they turn into real-world loss




