Discover how the ShinyHunters group uses sophisticated vishing and SSO abuse to bypass MFA and steal sensitive cloud data from major enterprises.
The New Frontier of Identity-Based Cloud Extortion
The new breed of cybercriminals is moving away from exploiting sophisticated software vulnerabilities and instead choosing to exploit the weakest link in the chain: humans. Recent reports have identified an advanced campaign by cybercriminals known as ShinyHunters, focusing their attention on Single Sign-On platforms.
These cybercriminals are employing sophisticated techniques that combine psychological and technical attacks, allowing them to exploit identity providers and obtain master keys to an entire organization’s cloud infrastructure.
This allows them to move laterally across various SaaS applications. This means that companies are now at an unprecedented risk of losing their data and facing extortion.
Understanding the Mechanics of Modern Vishing Attacks
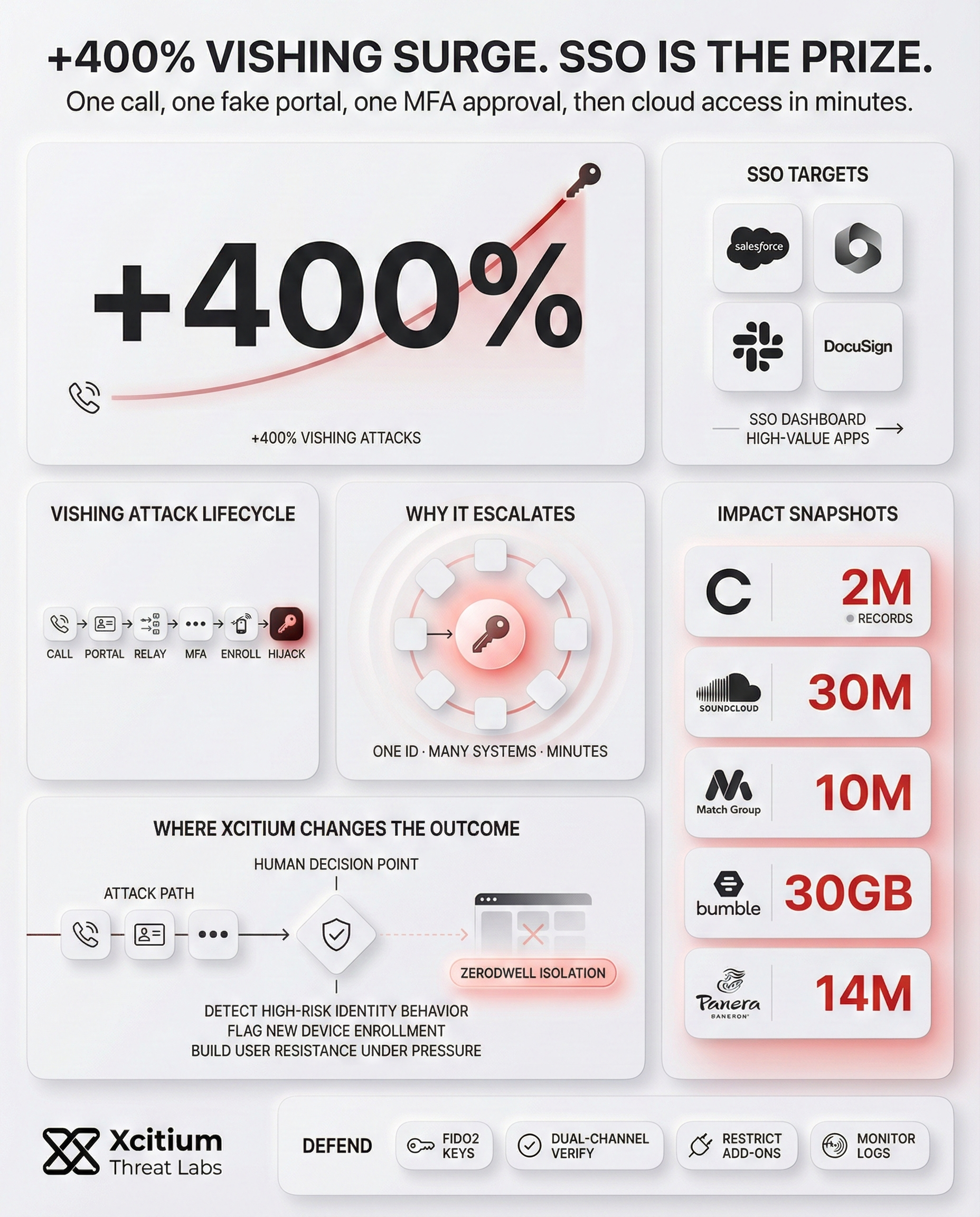
Voice phishing, also known as vishing, has emerged as the primary tool for identity thieves over the recent months. According to statistics, the cases of vishing have increased by over 400% over the course of the last year. The attackers usually pose as the IT helpdesk staff or corporate administrators over a direct phone call.
Vishing Attack Lifecycle
Anatomy of a Modern Social Engineering Campaign
Attacker builds trust by posing as IT or Admin support via phone.
Victim is manipulated into visiting a look-alike phishing portal.
Credentials are harvested and instantly used to access the real service.
The victim is tricked into authorizing a malicious MFA push notification.
Attacker registers their own hardware to secure persistent access.
Identity takeover complete. Persistence maintained indefinitely.
The attackers usually claim that the employee needs to update their security settings. During this call, the attacker sends the victim to a phishing site.
The attackers usually use corporate sites such as sso.com or internal.com. For instance, the attackers might use a URL that resembles the actual corporate site.
There are a number of key steps involved in this process:
- Initial Contact: The attacker contacts the victim through a process of social engineering to create immediate trust.
- Credential Harvest: The victim is asked to input their username and password on a fake login page.
- Real-Time Relay: The attacker immediately logs in to the actual service with the entered credentials.
- MFA Manipulation: The attacker convinces the victim to approve a notification or enter a one-time code sent to their phone.
- Device Enrollment: The attacker logs in to the service with the entered credentials to ensure they retain access.
With this process, the attacker gains complete control over the victim’s digital identity. Furthermore, the attacker retains control over the victim’s digital identity even if they change their password.
Why SSO Dashboards Are the Ultimate Prize
While Single Sign-On solutions offer employees unprecedented levels of convenience, they have also created a single point of failure that can have disastrous consequences for a company’s security. After all, if an attacker is able to successfully breach an SSO identity, they are then given immediate access to a dashboard of highly sensitive applications.
These types of platforms may include Salesforce, Microsoft 365, Slack, and DocuSign. For a group like ShinyHunters, this dashboard represents a gateway into the inner workings of a company’s most sensitive data.
They can download thousands of files, access private communication channels, and steal sensitive information within minutes of successfully breaching an identity. As such, a single identity breach can equate to a total breach of an organization’s security.
Real-World Impact and the Match Group Incident
The consequences of such identity-related attacks are not hypothetical. For instance, the recent breach of the Match Group is a good example of the destructive power of such attacks. The attackers used a false domain to gain access to the organization’s resources.
Consequently, sensitive information regarding popular online platforms such as Tinder and Hinge was shared with unauthorized individuals. This is a good example of how even the most technologically advanced organizations can fall victim to such well-executed vishing attacks. The consequences of such attacks include the loss of billions of dollars worldwide. The brand’s reputation is often negatively impacted.
ShinyHunters Latest Vishing Attacks
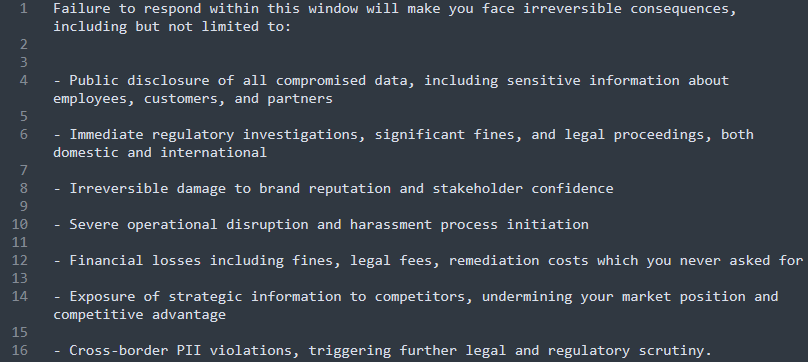
Affected Organizations & Data Impact
Detailed analysis of Vishing and SSO-based exfiltration events recorded in 2026.
Alleged data exfiltration targeting Okta SSO credentials with nearly 2 million records exposed during the breach.
Reported email fraud and sensitive data exfiltration following a high-pressure social engineering attack on internal staff.
Claimed theft of approximately 30 million user records, potentially linked to a persistence bridge from late 2025.
Compromised high-value user data across platforms like OkCupid and Hinge, exploiting identity verification gaps.
Over 30GB of internal repository data allegedly stolen through a compromised contractor account via vishing.
Identified in a massive leak database containing 14 million customer records, signaling a significant identity chain failure.
Sophisticated Evasion Tactics to Hide the Trail
It is important to understand that the attackers are not only focused on exfiltrating data but are also making concerted efforts to avoid detection. In a number of cases, the attackers have been able to utilize specialized tools to cover up their tracks. For instance, they may be able to install a third-party add-on that has been designed to search for and delete security notification emails. By clearing up “new device enrolled” notification emails from a victim employee’s inbox, they are able to prevent them from becoming aware of the attack.
The level of operational security that these attackers employ makes it extremely challenging for conventional detection systems to raise an alarm about the attack. Moreover, they may be able to utilize a residential proxy network to avoid detection. In other cases, they may be able to wait for weeks before initiating an attack in order to avoid sudden spikes in traffic.
Strengthening Your Defenses Against Identity Theft
To protect an organization against these types of sophisticated threats, it is important to have a multi-layered approach to identity and security. Organizations must look beyond passwords and implement more secure methods of authenticating their identities. However, technology alone is not sufficient to protect an organization against a vishing attack by a hacker. It is therefore important to educate the staff on how to identify a fraudulent call.
Additionally, it is important to have guidelines on how an employee should verify their identities when they are contacted by a supposed IT representative seeking their help. For example, an employee who receives a call from a supposed IT representative should always seek verification of the call through an official channel. The employee should, therefore, call the IT department on a number they know and trust.
Hardware
Security Keys
Intelligent
Log Tracking
Strict Access
Permissions
Dual-Channel
Verification
- Implement FIDO2: Organizations must use hardware-based security keys, as they are less likely to be subject to phishing and vishing attacks.
- Monitor Logs: Look out for suspicious login activity and downloads of data from SaaS services.
- Restrict Add-ons: Limit the ability of their staff members to install add-ons that have the ability to edit or delete emails.
- Verify Identity: Always use a secondary trusted channel to verify the identities of individuals seeking their help.
Conclusion: The Fastest Way Into the Cloud Is Through a Human
ShinyHunters proves that modern cloud breaches do not start with malware, they start with persuasion. A single convincing phone call, a look alike login page, and one approved MFA prompt can hand attackers a working SSO identity, then a direct path into Microsoft 365, Slack, DocuSign, and more.
Why This Threat Escalates So Quickly
SSO platforms compress risk. Once an attacker hijacks one identity, they inherit the same convenience your workforce relies on, and they can move across SaaS dashboards and sensitive data in minutes.
Why Most Organizations Are Exposed
Vishing succeeds because it exploits gaps that security tools often treat as normal behavior.
- Trust is granted over the phone, under urgency and authority pressure
- Credentials are relayed in real time, so MFA becomes a hurdle to manipulate, not a blocker
- Device enrollment turns a one time mistake into persistent access
- Security signals can be delayed, deleted, or ignored before anyone reacts
Where Xcitium Changes the Outcome
If you have Xcitium, this attack would NOT succeed.
With Xcitium Identity Threat Detection and Response and a single deployment of Xcitium Cyber Awareness Education and Phishing Simulation, vishing driven SSO takeovers lose their leverage.
- High risk identity behavior is detected and stopped before access turns into data theft
- Suspicious new device enrollment is flagged immediately, and access is cut off fast
- Users build instinct to verify helpdesk claims, and resist MFA manipulation under pressure
- The attacker’s advantage disappears at the human decision point, before the SSO dashboard is ever theirs
Secure the Layer Attackers Target First
Cloud security now begins with identity. Reduce trust by default, verify every request, and make social engineering fail before it becomes a breach.




