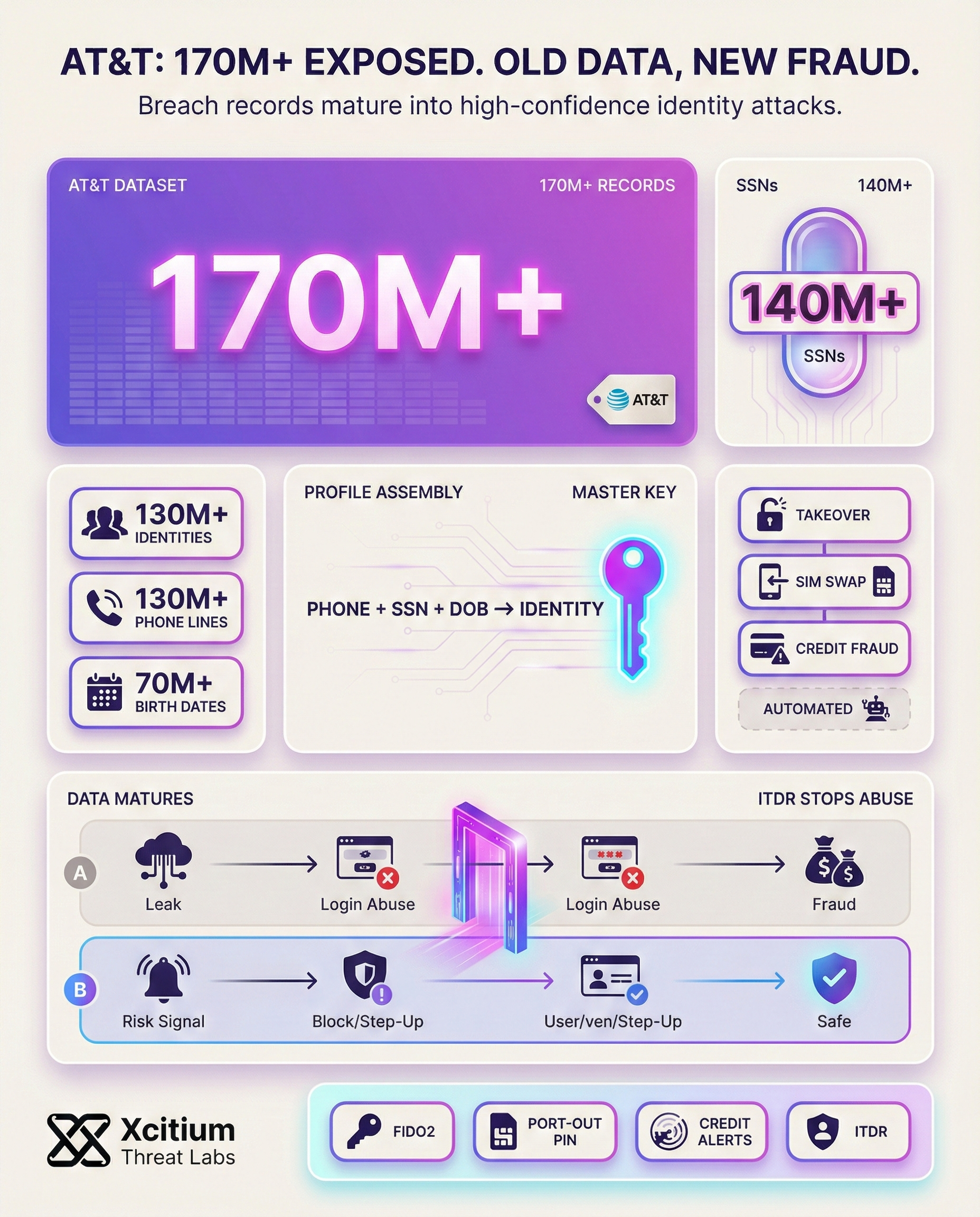
Recently, a large dataset associated with AT&T has re-emerged, validating that time does not reduce the severity of a security breach. Rather, as cybercriminals combine and enhance their stolen data, these “old” security breaches are now more potent than ever. This latest breach, reportedly has a staggering 170M+ records, providing a goldmine for identity thieves and sophisticated scammers.
Analyzing the Scale of the Resurfaced 170M+ Records
The sheer volume of data in this set is enough to cause concern in any current or former AT&T user. However, the true concern lies in the type of personal data that is being included in these records. According to recent reports, the data leak includes a broad range of data points that can be used to create a complete digital identity.
Furthermore, if these data points are combined into a single profile, the entire risk profile changes. Thus, an email address is no longer just an entry point for spam messages but rather a key to access a wealth of personal data.
While the volume of this dataset is staggering, the real danger lies in the specific types of personal information used to reconstruct digital identities.
00101110
11001010
01010101
10110011
SYS_EXPOSED
AUTH_FAIL
ROOT_INTR
DATA_LEAK
0xBC42
0x99ED
0x12FA
0xDEAD
When fragmented data points are consolidated into a single profile, the risk level escalates dramatically. A simple email address is no longer just for spam; it becomes a master key to a vast vault of personal records.
How Criminals Transform Stolen Data into High-Impact Attacks
Cybercriminals are remarkably efficient at using “repackaged” data to launch highly targeted campaigns. Consequently, they do not need a fresh hack to cause significant financial or personal damage. By using the rich profiles found in this resurfaced AT&T dataset, attackers can execute several types of sophisticated maneuvers.
For instance, they can craft incredibly convincing phishing emails that include your actual Social Security digits to “verify” their legitimacy. In addition, these details allow criminals to bypass traditional security questions used by banks and mobile carriers. As a result, SIM-swapping attacks where a hacker takes control of your phone number become much easier to execute when the attacker knows your date of birth and address.
Furthermore, this data serves as a Swiss Army knife for long-term identity theft. Criminals can use the combination of SSNs and birth dates to open fraudulent credit lines or file fake tax returns. Because the data is structured and searchable, it allows for automation, meaning thousands of people can be targeted simultaneously with minimal effort from the attacker.
Understanding the Evolution of Data Breaches in 2026
Of course, it is essential to understand that this is not necessarily a “new” breach in the traditional sense of the word. What is being seen is more of an evolution of data that has been in circulation for years.
The key difference in this particular breach is that it is of such high quality and scope. For example, in years past, perhaps only one or two different categories of data may have been involved in any single breach. However, today, the entire market is built on complete profiles that leave absolutely nothing to the imagination. This is why, in the case of the resurfaced data from AT&T, it is necessary to realize that the burden of protection is on the consumer rather than the corporation that originally lost that data.
Practical Steps to Shield Your Digital Identity Today
Although you cannot take your data back after it has been placed on the dark web, you can definitely make it harder for criminals to use it against you. Thus, taking proactive measures is the best way to mitigate risks associated with AT&T’s data breach.
- Enable Advanced Authentication: Use FIDO2 hardware keys or 2FA with biometrics instead of using SMS-based 2FA.
- Lock Your Mobile Account: Contact your mobile carrier to set up a special “port out” PIN that prevents others from switching your SIM card.
- Monitor Your Credit: Set up alerts with major credit reporting agencies to detect if someone has attempted to open new accounts in your name.
- Use a Password Manager: Make sure each account has a strong, complex password that is different from all others, preventing “credential stuffing” attacks.
In addition, be highly suspicious of unsolicited messages that purport to be from AT&T. If you receive a message asking for “verification” or reporting a “security issue,” do not click on the links provided. Go to their website or use their app to check your account status.
The Critical Role of Identity Monitoring Services
However, in a world where data is continually being recycled, monitoring your accounts may not be enough to keep up with the pace of cybercrime. Therefore, most experts recommend that you use dedicated identity protection services, which monitor the dark web and various forums for your specific details.
Therefore, being informed is your first line of defense. However, as this AT&T situation continues to change, your level of “cyber hygiene” will be what sets the difference between a minor inconvenience and a major financial disaster. Remember, in the world of cyberspace, your most valuable asset is your identity and the one most worth protecting.
Conclusion: “Old” Breach Data Creates New Identity Attacks
The resurfaced AT&T dataset reinforces a dangerous 2026 reality, breach data does not expire, it matures. When millions of records are repackaged into complete identity profiles, criminals do not need a new intrusion to cause new harm.
Why This Threat Hits Harder Than a Typical Leak
This is not just email spam risk. The exposed data points enable high-confidence identity abuse at scale, including targeted phishing, security question bypass, SIM swap attempts, fraudulent credit activity, and automated identity theft workflows.
Why Everyone Is Exposed
Most defenses are built for fresh compromise, not recycled identity data.
- Attackers combine old leaks to increase accuracy and trust signals
- Phone numbers and birth dates enable stronger impersonation
- SSN exposure turns “verification” into a weapon
- Automation makes thousands of victims economically viable
Where Xcitium Changes the Outcome
If you have Xcitium, this attack would NOT succeed in the way criminals intend.
With Xcitium ITDR, identity abuse signals are surfaced and stopped before they become account takeover or financial damage.
- Risky sign-ins and anomalous identity behavior are detected early
- High-risk access attempts are blocked fast, before the attacker gains momentum
- The attacker loses the ability to convert leaked identity data into real access
Protect the Asset That Attackers Reuse Forever
You cannot recall exposed data, but you can shut down what criminals try to do with it. Treat identity as the primary security perimeter, and defend it with controls that respond in real time.




