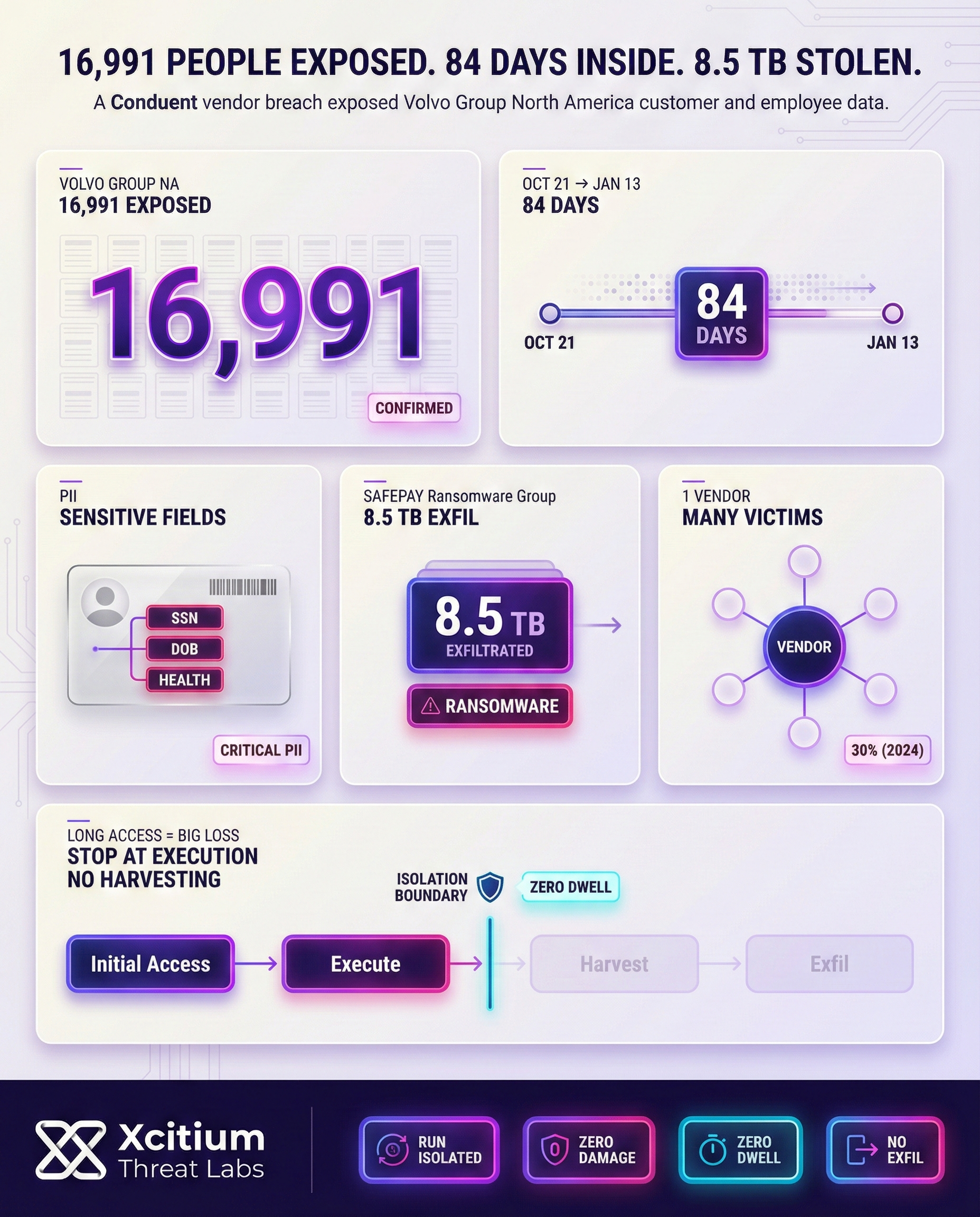
Volvo Group North America confirmed the breach, which involved the personal information of customers and employees, and provided the date it confirmed employees were impacted, which was January 21, 2026, nearly one year after Conduent first learned of the breach, demonstrating the time it takes to assess vendor-related breaches.
The breach began with a cyber attack on Conduent, an outsourcing company, which experienced unauthorized access to their systems in late 2024.
Personal information, such as names, Social Security numbers, birthdates, and information related to their health plans, of 17,000 Volvo customers and employees was stolen. Conduent revealed the breach in late 2025, and this analysis will discuss how the breach occurred, what information was stolen, and how it affects customers.
Conduent Breach and Volvo’s Impact
Volvo Group North America (the arm handling Volvo’s trucks, buses, and heavy equipment in the US/Canada/Mexico) was hit indirectly. Attackers infiltrated Conduent’s network on October 21, 2024 and stayed until January 13, 2025. Conduent discovered the breach in January 2025 and disclosed it months later.
Regulatory filings reveal that 16,991 Volvo-related individuals had data exposed in the incident. In total, nearly 17,000 Volvo customers or personnel are confirmed affected. Volvo stresses its own systems were not breached only the third-party vendor’s systems were compromised.
Data Exposed in the Hack
The hackers stole highly sensitive records. Conduent confirmed intruders exfiltrated data including full names, Social Security numbers, dates of birth, health insurance details, ID numbers, and medical information.
In all, millions of people were affected (for example, 10.5M in Oregon and 15.5M in Texas). Among those, almost 17,000 Volvo-related individuals had their data exposed. This kind of information (PII and health data) significantly increases the risk of identity fraud and misuse.
Breach Mechanics and Attackers
Investigators link the attack to the SafePay ransomware group, which claimed credit for stealing over 8.5 TB of data from Conduent. Threat actors entered Conduent’s network on October 21, 2024 and remained until January 13, 2025, giving them months to copy files.
Conduent reports finding no evidence yet that the stolen Volvo data has been abused. After the breach was discovered, Conduent locked down systems, brought in forensic experts, and began notifying clients. The long “dwell time” (nearly three months) is typical of complex supply-chain breaches and allowed attackers to extract large data volumes before detection.
Third-Party Breaches on the Rise
This incident represents a rising trend within the cybersecurity arena. Vendor supply chain breaches are on the rise. Analysis of the industry has revealed that 30% of breaches in 2024 were attributed to an external third-party vendor, nearly double what was experienced the previous year.
In this case, by compromising one vendor, hackers can compromise many victims. For instance, the MOVEIT file transfer breach experienced by thousands of victims within 2023 was attributed to a vendor breach. Such breaches are more expensive to deal with since they may result in a 40% increase in containment costs compared to breaches experienced internally.
Conclusion: One Vendor Breach, Thousands of Real People Exposed
The Conduent incident shows how quickly third party risk becomes customer harm. Volvo Group North America confirmed that a vendor systems intrusion exposed data for 16,991 people, including names, Social Security numbers, dates of birth, and health plan or medical information.
Why This Breach Matters
This was not a short disruption, it was long access.
Attackers were inside Conduent from October 21, 2024 to January 13, 2025. That is 84 days of dwell time, enough to identify valuable datasets, copy them, and leave victims with long term identity risk.
Why Every Organization Is Vulnerable
This is the supply chain reality, you inherit the security posture of everyone who touches your data.
- Vendors store sensitive PII and healthcare related records at scale
- A single compromise can affect many downstream organizations at once
- Third party breaches are rising, analysis cited in the post notes 30% of breaches in 2024 were attributed to an external vendor
Where Xcitium Changes the Outcome
If Conduent had Xcitium, this attack would NOT succeed.
Xcitium Advanced EDR, powered by the patented Zero Dwell platform, stops the attacker where supply chain breaches become catastrophic, at execution. The ransomware crew can gain initial access, but code can run without being able to cause damage, which prevents the long, quiet data harvesting window that makes incidents like this so costly.
Reduce Vendor Blast Radius Before the Next Breach
Your security boundary now includes every outsourcing partner. Enforce controls that prevent long dwell time, and treat third party access as production risk, not procurement detail.




