Cybercriminals exploit iCloud Calendar invites to send phishing emails from Apple’s servers, allowing fake alerts to bypass spam filters.
Recent cybersecurity reports describe a new phishing tactic using Apple’s iCloud Calendar service. Attackers craft malicious calendar invites that appear to come from a legitimate Apple email address. Because these invites originate from Apple’s servers, they can bypass spam filters. In one case, an invite was used to send a fake PayPal charge, tricking the recipient into thinking they were charged $599.
How the Scam Works
Scammer creates an iCloud Calendar event, fills the Notes field with the phishing message, and invites one or more external addresses (often a Microsoft 365 mailing list). When the event is sent, Apple’s servers automatically email the invite from the calendar owner’s Apple address (noreply@email.apple.com). As a result, the message passes email security checks (SPF/DMARC/DKIM) and appears authentic in the recipient’s inbox.
Example: Fake PayPal Invoice
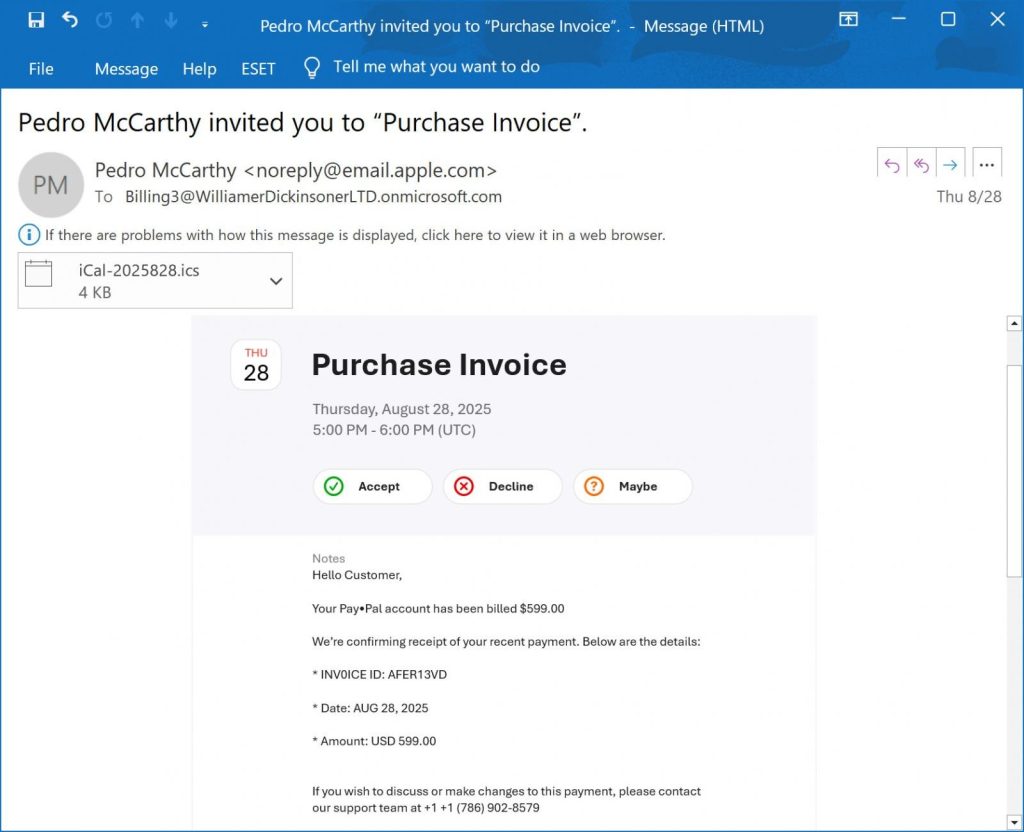
In this case, an invite claimed the recipient’s PayPal account had been billed $599.00 and urged them to call a number to cancel the charge. Victims who called were then pressured into installing remote-access software or handing over data, often resulting in stolen funds or malware.
How to Protect Yourself
- Verify directly: Confirm any unexpected payment alert by logging into your account (e.g., via PayPal’s site) instead of using links or phone numbers from the message.
- Watch for red flags: Look for generic greetings or spelling mistakes – legitimate companies normally address you by name.
- Enable 2FA: Use two-factor authentication on important accounts for extra security.
- Report suspicious messages: Forward any suspicious emails or invites to the company’s security team (for example, phishing@paypal.com).