In today’s rapidly evolving cyber threat landscape, traditional perimeter-based security models are becoming obsolete. The idea that once inside the network, users and devices can be trusted, is a security flaw that is now widely recognized. As cyberattacks grow more sophisticated and organizations embrace digital transformation, the need for a new, more robust security model has never been more critical. Enter Zero Trust Architecture (ZTA)—a security framework that is quickly shifting from an optional strategy to a mandatory approach in modern cybersecurity.
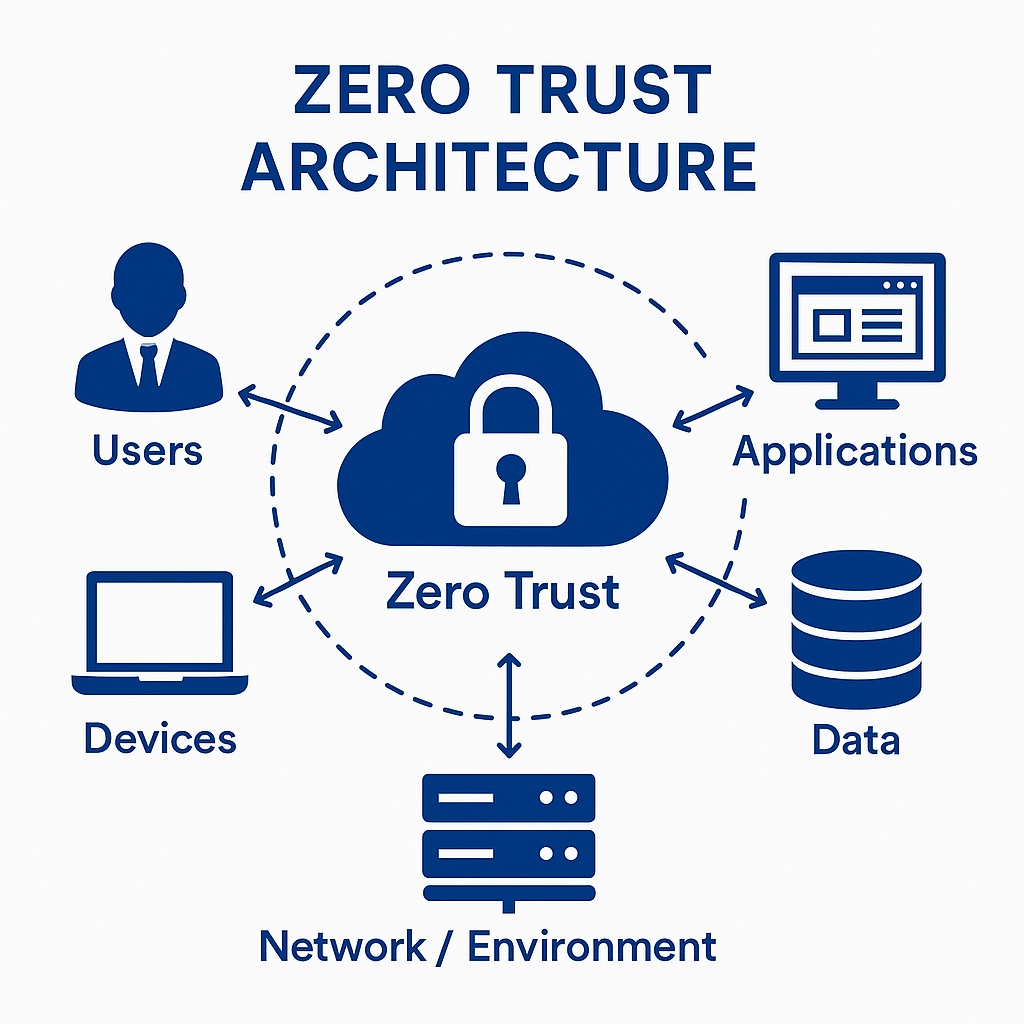
What is Zero Trust Architecture?
Zero Trust Architecture is based on a fundamental principle: “Never trust, always verify.” This means that no user or device is automatically trusted, whether they are inside or outside the corporate network. In traditional security models, once a user or device gains access to the network, they are trusted by default. Zero Trust flips this assumption, continuously verifying every user, device, and application before granting access to any resources, regardless of their location within the network.
This approach fundamentally changes how organizations handle cybersecurity by ensuring that trust is constantly reassessed. Access to resources is granted only when users or devices are authenticated and authorized, greatly reducing the risk of a breach.
Why Zero Trust is Becoming a Necessity
The digital transformation, accelerated by the rise of cloud computing, IoT, and the widespread adoption of remote work, has rendered traditional network security models increasingly ineffective. In a perimeter-based security model, once attackers breach the perimeter, they can move laterally within the network undetected, accessing sensitive information and systems.
Zero Trust addresses this issue by eliminating the concept of a trusted internal network. It applies granular access control and ensures that the “trust but verify” principle is applied to every transaction, providing stronger protection for both internal and external network users.
The Rise of Insider Threats
Another key driver for the adoption of Zero Trust is the increasing prevalence of insider threats. Data breaches are no longer solely the result of external hackers; a significant number of data breaches now originate from within organizations, often involving trusted employees or contractors. Insider threats can be particularly damaging because insiders typically have legitimate access to sensitive data and systems, making it difficult to detect and prevent their malicious activities.
Zero Trust helps mitigate the risks of insider threats by continuously monitoring user behavior and access requests. By ensuring that users only have access to the resources necessary for their roles, Zero Trust limits the potential damage caused by compromised accounts or malicious insiders.
Key Components of Zero Trust Architecture
To implement Zero Trust effectively, several critical components must be integrated into an organization’s security framework. These include:
- Identity and Access Management (IAM): A robust IAM framework is central to Zero Trust, ensuring that only authorized users can access sensitive systems and data. IAM systems must continuously authenticate users and devices, ensuring that access is tightly controlled and monitored.
- Multi-Factor Authentication (MFA): Multi-factor authentication adds layers of security by requiring more than just a password to gain access. By verifying users through additional factors such as biometrics, authentication apps, or hardware tokens, MFA significantly enhances security.
- Least Privilege Access: The principle of least privilege ensures that users only have access to the minimum resources they need to perform their job functions. This reduces the potential attack surface and limits the damage if a user’s account is compromised.
- Network Segmentation: Zero Trust requires breaking the network into smaller, more secure segments. Network segmentation limits lateral movement within the network, containing breaches to specific areas rather than allowing attackers to roam freely.
- Continuous Monitoring: Zero Trust systems require continuous monitoring to detect anomalies in user behavior, device activity, and network traffic. Real-time visibility into traffic patterns and access requests allows for immediate adjustments to access controls as needed.

Implementing Zero Trust: A Step-by-Step Approach
Implementing Zero Trust is not an overnight task; it requires careful planning, strategy, and ongoing management. Here’s a step-by-step guide for organizations looking to adopt a Zero Trust Architecture:
- Identify Critical Assets: Start by understanding which data, applications, and services are most valuable and vulnerable to attacks. These assets should be prioritized for Zero Trust protection.
- Map User Roles and Access Needs: Align user privileges with their job functions, ensuring that each user has access only to the resources they need. This minimizes unnecessary exposure and potential risks.
- Deploy Multi-Factor Authentication (MFA): Implement MFA across all systems and endpoints to strengthen user authentication. MFA is one of the simplest and most effective ways to enhance security.
- Use Micro-Segmentation: Break your network into smaller segments to control lateral movement within the environment. Micro-segmentation helps contain breaches by preventing attackers from moving freely across the network once inside.
- Monitor and Audit: Continuously monitor network traffic and user behavior for unusual patterns. Implement logging, analytics, and alerting to detect potential security incidents early.
- Regularly Review and Update Policies: Zero Trust is an ongoing process. Regularly review your access control policies and security configurations to ensure they are up-to-date with emerging threats.
Challenges in Implementing Zero Trust
While Zero Trust is a powerful security model, its implementation can present several challenges. These may include:
- Legacy Systems: Many organizations still rely on legacy systems that may not be compatible with Zero Trust principles. Migrating to a Zero Trust framework may require significant updates or replacements of outdated systems.
- Complex IT Infrastructures: Organizations with complex IT environments, including hybrid cloud architectures and numerous third-party integrations, may face difficulties in deploying Zero Trust across all systems and devices.
- Resistance to Change: Organizational inertia and resistance to change can slow the adoption of Zero Trust. Employees and teams accustomed to traditional security models may be hesitant to adopt new processes and technologies.
Despite these challenges, the benefits of Zero Trust far outweigh the obstacles. The model’s ability to significantly reduce the risk of data breaches and insider threats makes it an essential investment for organizations of all sizes.
Why Zero Trust is Now Essential
Cyberattacks are no longer rare events—they are persistent, evolving, and increasingly sophisticated. The average enterprise experiences multiple breach attempts each week. Zero Trust offers a structured way to manage these threats, reducing the attack surface and providing a continuous, adaptive security posture.
Additionally, Zero Trust helps organizations comply with industry regulations like GDPR, HIPAA, and CCPA, ensuring that access to sensitive data is tightly controlled and monitored. As businesses embrace cloud services, remote work, and third-party integrations, Zero Trust becomes essential for protecting against the increasingly complex and distributed threat landscape.

The Future of Zero Trust
Looking ahead, Zero Trust is expected to become a foundational element of cybersecurity strategies in 2025 and beyond. As cyber threats continue to evolve, and with the growth of cloud computing, IoT, and remote work, organizations will need to rethink their security models. Zero Trust offers a comprehensive, adaptive, and scalable solution to combat today’s dynamic threats.
By implementing Zero Trust, organizations can ensure that they are better prepared to defend against both external and internal threats in an increasingly complex digital world.
Zero Trust is the Future of Cybersecurity
In conclusion, Zero Trust is no longer just a buzzword—it is a critical necessity in modern cybersecurity. As businesses adapt to the changing digital landscape, the traditional perimeter-based security models are no longer sufficient to protect sensitive data and resources. By adopting Zero Trust Architecture, organizations can implement stronger access controls, reduce the risk of breaches, and ensure resilience against evolving cyber threats.
Zero Trust is the future, and its implementation is no longer optional—it is essential.




