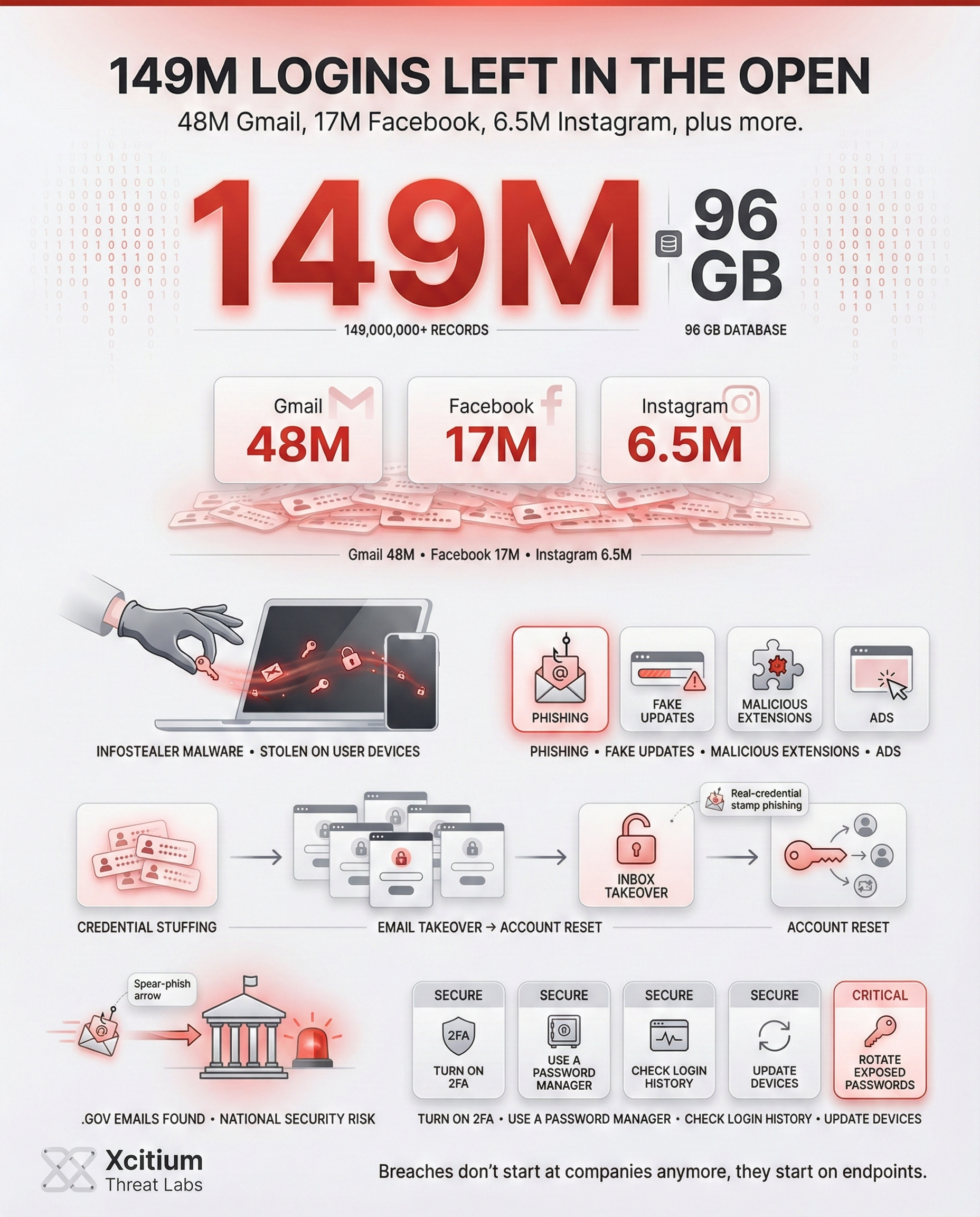
An unprotected database exposed 149 million stolen logins including 48M Gmail and 6.5M Instagram accounts highlighting risks of infostealer malware.
Millions of Gmail and Instagram Credentials Found Exposed Online
A cybersecurity researcher recently uncovered a massive data leak with over 149 million stolen login credentials sitting in a publicly accessible database. The trove was left unprotected no password or encryption essentially open for anyone to view. Moreover, this 96 GB database contained account data from users worldwide, spanning popular services like Gmail, Instagram, Facebook, Netflix, and many others. In a sample of the records, researchers found staggering numbers of compromised accounts across major platforms. The leak exposed:
| TARGETED_ENTITY | VICTIM_COUNT |
|---|---|
| Gmail | 48.0M |
| 17.0M | |
| 6.5M | |
| Netflix | 3.4M |
| Educational (.edu) | 1.4M |
| Binance | 420K |
The database even contained 420,000 Binance crypto-wallet logins and 100,000 OnlyFans accounts, showing the breadth of services affected. Particularly alarming was the presence of numerous government (.gov) emails from multiple countries. This means that even some public sector accounts were caught up in the breach, raising concerns about national security implications.
Infostealer Malware: How the Data Was Stolen
However, the massive password leak was not due to the breach of a particular website, but due to the infostealer malware entering users’ devices without their knowledge. Once the infostealer malware infects a particular device, it works like a pickpocket, stealing users’ keystrokes, passwords, cookies, and even the content of the clipboard without the users’ knowledge. It usually infects users’ devices via phishing emails, fake software updates, malicious browser extensions, and misleading ads, which enables the attacker to access thousands of users’ credentials on various platforms.
In the current case, the criminals used a cloud database to store the compromised data, but due to their own oversight, the database remained unsecured and accessible to the public. Jeremiah Fowler, a cybersecurity researcher, found the database and reported the issue, although it remained unsecured and accessible to the public for almost a month.
During this time, the database continued to accumulate new compromised credentials, suggesting that the malware was functioning and collecting new data. One of the harsh realities that this case reveals is that infostealers have become ubiquitous, and even the criminals’ own unsecured infrastructure can lead to a large-scale data breach.
Stolen Logins Pose Serious Security Risks
- Credential Stuffing Attack: With the availability of a vast collection of email and password combinations, attackers often resort to the credential stuffing attack to leverage the tendency of users to reuse the same password on multiple platforms.
- Access to an email account: Criminals can change the password for other accounts by gaining access to an email account.
- Identity Theft/Fraudulent Financial Activities: Stolen identity can be exploited to withdraw money from bank accounts, make illegal transactions, or even misuse saved money.
- More effective phishing: The knowledge of the actual login credentials of the victim helps in more effective phishing attacks.
- Government account exposure: Compromised .gov email accounts can be used to launch spear phishing attacks or as a gateway into these government organizations.
- Wider security impact: While this breach transcends an individual’s right to privacy, it also affects corporate and governmental security.
Protecting Your Accounts After a Data Leak
In the wake of such a massive leak, staying safe online requires immediate action. Therefore, its recommended that users take the following steps to protect their accounts and personal information:
By following these precautions, users can dramatically reduce the chance of hackers turning a data leak into personal catastrophe. Cyber threats are ever-evolving, but proactive security habits make you a much harder target.
Conclusion: When Stolen Credentials Sit in the Open
This leak is a stark reminder that breaches do not always start with a hacked company, they often start with a compromised user device. A publicly exposed 96 GB database held 149 million stolen logins, including 48 million Gmail accounts and 6.5 million Instagram accounts. Left unprotected for weeks, it kept accumulating new credentials, proving how nonstop infostealer collection has become.
Why This Threat Matters
Once credentials are harvested at scale, attackers can move fast and cheaply:
- Credential stuffing across multiple services
- Email takeover used to reset other accounts
- More convincing phishing using real usernames and passwords
- Elevated risk when government and corporate emails are included
Why Everyone Is Vulnerable
This incident reflects common, repeatable failure points:
- Infostealers delivered through phishing, fake updates, malicious extensions, and misleading ads
- Password reuse across platforms
- Limited visibility into early device compromise, until accounts are already abused
- Criminal infrastructure that is messy, but still deadly at scale
Where Xcitium Changes the Outcome
For organizations using Xcitium Cyber Awareness Education and Phishing Simulation, infostealer-driven leaks lose their momentum.
- Employees learn to recognize credential theft lures before they click.
- Simulated campaigns build pause and verify behavior under real pressure.
- Risky prompts and fake updates get questioned before any password is entered.
- Code can run without being able to cause damage, when the user never completes the attack path.
With Xcitium in place, this type of credential harvesting operation is far less likely to succeed, because the attacker’s advantage disappears at the human decision point.
Protect Accounts Before the Leak Finds You
Assume credentials are being targeted every day, then train, test, and reduce the click rate that fuels infostealers. Choose Xcitium Cyber Awareness Education and Phishing Simulation.




