Lotus Blossom infiltrated internal update servers and injected malicious code into the system.
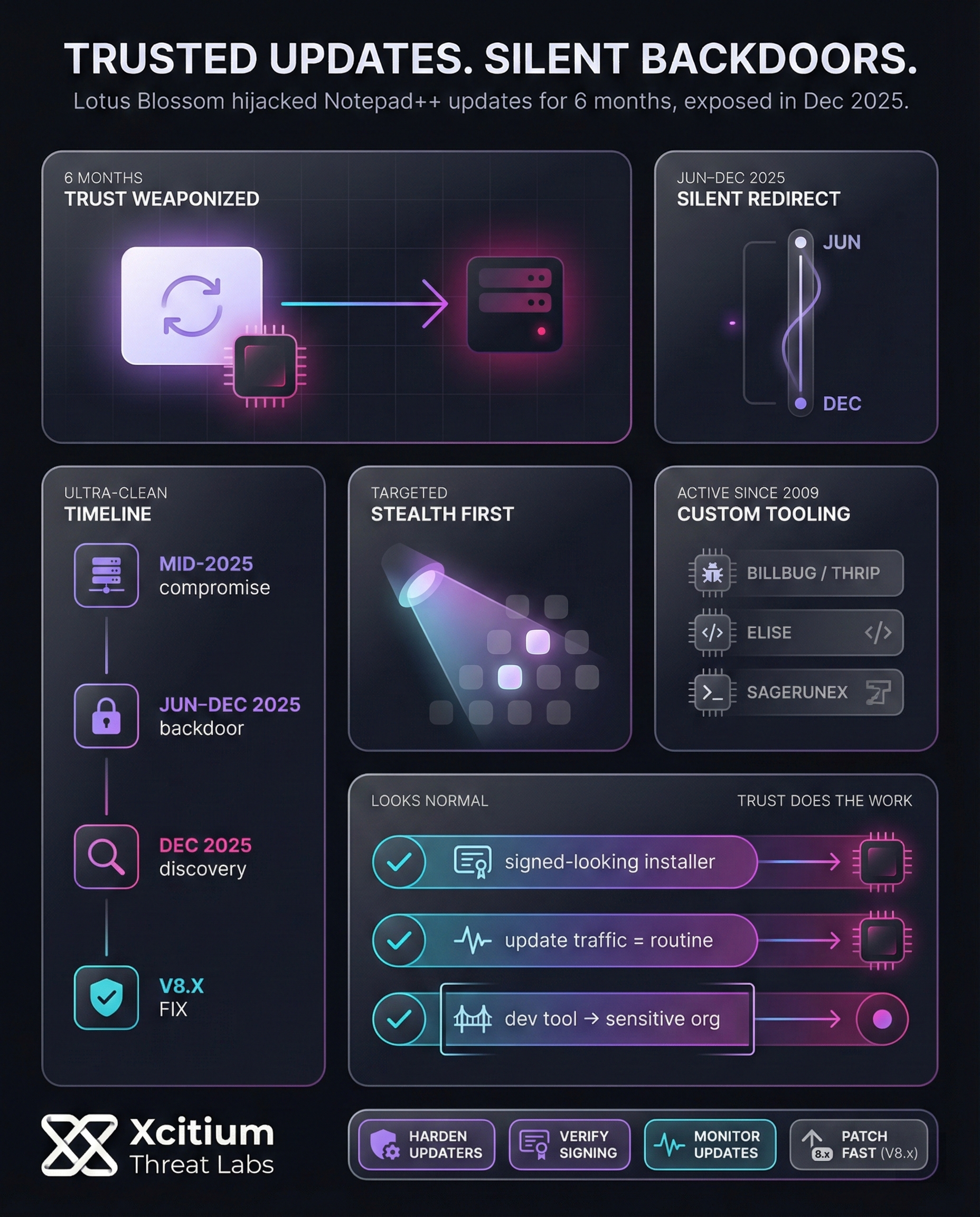
The popular code editor Notepad++ was recently at the center of a stealth cyber-espionage incident. A Chinese state-sponsored hacking group known as Lotus Blossom quietly compromised Notepad++’s update process for half a year. Some users unknowingly downloaded tainted software updates that allowed the attackers to spy on their activities. The breach did not affect every user; however, it shows how determined threat actors can weaponize trusted software to target specific victims.
Users were redirected to attacker-controlled servers for 6 months, leading to silent backdoor deployment.
The operation was finally detected, exposing tampered updates and unauthorized remote access.
Infrastructure moved to secure hosting; the exploit was patched and attacker access was severed.
Lotus Blossom Infiltrates Notepad++ Updater for Six Months
Lotus Blossom gained access to Notepad++’s internal servers and injected malicious code into their update process. For six months, users who checked for updates would be redirected to malicious servers without their knowledge.
The hackers also created a custom backdoor through Notepad++ updates, allowing them remote access to affected computers. The operation continued undetected until December 2025.
The Notepad++ developer took swift action once they discovered the hacking attempt by transferring their site to a safer server. They also released a patch to fix the security hole that was exploited by the hackers. This meant that hackers lost their connection. Users were therefore encouraged to update Notepad++ as soon as possible.
Targeted Espionage Tactics, Not Mass Surveillance
Unlike the mass attack, the operation of Lotus Blossom was very targeted. The attackers did not target a wide range of systems, and therefore the majority of Notepad++ users did not experience the attack. The modus operandi of the group is based on stealth and persistence.
Once they gain access to a network, they conduct a quiet reconnaissance and attempt to access information using remote commands. There is no indication that they engaged in mass data theft or damage. The modus operandi of the group is based on the quality of the intelligence gathered rather than the quantity of victims.
It is clear that the operation flew under the radar, and the majority of users did not experience the attack. The operation is based on spying, and the data access is selective.
Lotus Blossom’s Decade-Long Espionage History
This APT group has been operational for at least 2009, attacking entities all over the world. Other names for the APT are Billbug and Thrip. From the previous attacks attributed to the Lotus Blossom APT, the motivations behind the APT’s attack vectors are as follows:
Active since 2015. Operation Lotus Blossom targeted SEA military assets with surgical precision.
Uses Spear Phishing with military rosters to deploy stealthy spyware via social engineering.
Proprietary arsenal featuring Elise and Sagerunex for persistent network access.
Uses PowerShell and native OS binaries to remain undetected by traditional defense layers.
- Southeast Asian Targets: This APT has been involved in the compromise of government entities, including military institutions, in the Southeast Asian region. It was first identified as the actor behind the 2015 Operation Lotus Blossom campaign, which compromised numerous entities within the Southeast Asian region.
- Spear Phishing & Decoy Documents: From the previous attacks attributed to the Lotus Blossom APT, the APT has been using spear-phishing emails containing decoy documents, such as military rosters, which contain the APT’s malware. When the unsuspecting target opens the document, the target unknowingly executes the APT’s spyware.
- Custom Malware Toolkits: Lotus Blossom creates custom malware toolkits for use in the operation. It has been using a backdoor trojan named Elise in the early days of operation. However, the APT has been using other malware, such as the Hannotog and Sagerunex backdoors, in the later years of operation. Also, it uses the malware toolkits for the purpose of maintaining stealthy surveillance of the compromised target.
- “Living off the Land” Stealth: Lotus Blossom has been using the “living off the land” tactic, using legitimate system tools such as PowerShell scripts. This tactic has enabled the APT to evade detection by anti-virus software for an extensive period.
From these operations, it is clear that Lotus Blossom has been engaged in espionage for a long time. However, it is also clear that state-sponsored hackers, such as Lotus Blossom, change their tactics from using emails to compromise systems, as seen in its initial operations, to using more sophisticated tactics, such as the Notepad++ supply chain attack.
A critical vulnerability that transforms official update channels into covert distribution systems for cyberattacks.
The capacity for a single leak to instantly spread across thousands of corporate and government networks through a trusted gateway.
The ability for attackers to hide behind signed files, evading traditional security systems for months on end.
Software Supply Chain Attacks: A Growing Threat
The Notepad++ breach highlights a troubling trend: software supply chain attacks. In such attacks, hackers infiltrate a trusted software source to distribute malicious code to many victims at once. In this case, a popular developer tool’s updater was turned into a Trojan horse. Notepad++ is used by developers, IT staff, and even government workers, so compromising its updates offered a potential gateway into sensitive organizations.
Furthermore, supply chain attacks are notoriously hard to detect. Users generally trust official software updates and don’t expect their tools to be secretly hijacked. Attackers like Lotus Blossom can quietly monitor and collect intelligence for months before anyone notices. This incident echoes other high-profile supply-chain hacks and is a wake-up call for the industry.
Software makers must harden their update mechanisms (for example, by using robust authentication and code signing), and users should stay vigilant even when installing updates from legitimate sources.
Conclusion: When a Trusted Update Becomes an Espionage Weapon
Lotus Blossom turned a routine Notepad++ update into a stealth access path, running quietly for six months before it was exposed in December 2025. Users were redirected to attacker controlled servers, received tampered updates, and unknowingly installed a custom backdoor designed for long term surveillance, not loud disruption.
Why This Threat Still Matters
This was not a mass spray attack, it was selective, persistent, and built on one advantage, trust. When official update channels are compromised, even cautious users can install the threat for you.
Why Most Organizations Are Vulnerable
Supply chain abuse scales because it hides in normal behavior:
- Teams trust signed looking installers and updater prompts
- Monitoring often treats update traffic as routine
- A single poisoned tool can become a gateway into sensitive environments, especially when developers and IT staff are the users
Where Xcitium Changes the Outcome
If you have Xcitium Advanced EDR, this attack would not succeed.
- The trojanized updater can start, but code can run without being able to cause damage
- The backdoor cannot turn execution into system access, persistence, or surveillance value
- The attacker loses the ability to weaponize trust into control
Final Takeaway
Nation state tradecraft is increasingly delivered through the software you already trust. Defend the update path like production, because attackers already do.




