The cybersecurity world has been significantly impacted over the past Friday. The US Cybersecurity and Infrastructure Security Agency has issued a critical directive. The Federal agencies need to secure their BeyondTrust Remote Support and Privileged Remote Access. The directive has been issued to counter an actively exploited vulnerability.
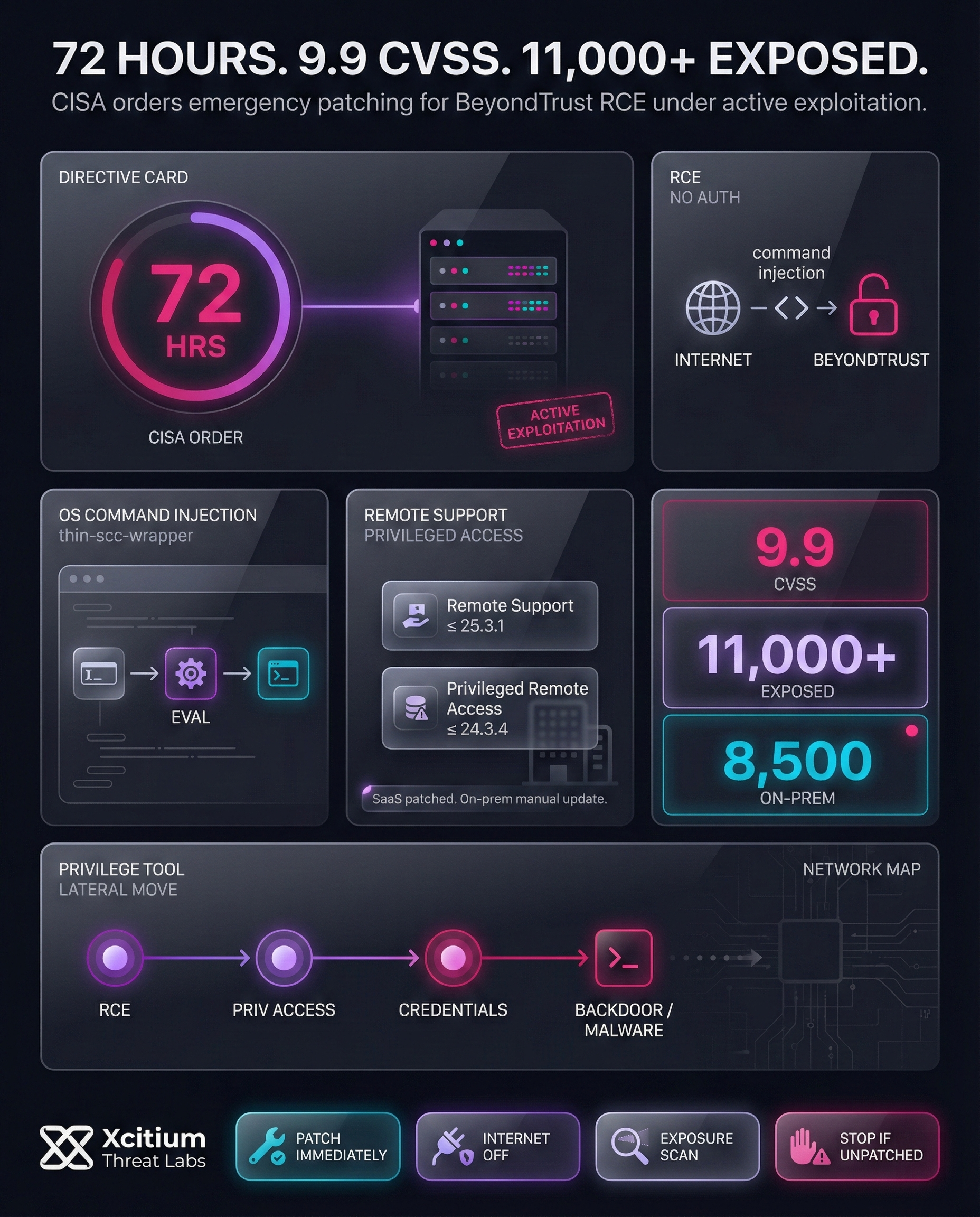
The identified vulnerability is CVE-2026-1731. The severity of this vulnerability is indicated by its CVSS score of 9.9. The CISA has issued a critical directive to all Federal Civilian Executive Branch (FCEB) entities to patch this vulnerability within a strict window of three days. The severity of this threat is such that BeyondTrust services are critical to over 20,000 global customers.
Understanding the Critical BeyondTrust Security Flaw
CVE-2026-1731 is a remote code execution vulnerability. This vulnerability is classified as an operating system command injection vulnerability.
In this case, the operating system command injection vulnerability is in the thin-scc-wrapper shell script, which does not sanitize input correctly and allows for dangerous Bash arithmetic evaluation. This allows an unauthenticated remote attacker to execute arbitrary operating system commands, without needing to interact with the system in any way.
This vulnerability allows an attacker to execute remote code on the remote host. It is confirmed to exist in various versions of the BeyondTrust product. This affects the remote support version 25.3.1 and earlier, as well as the privileged remote access version 24.3.4 and earlier. The vendor has also updated its SaaS product to address this vulnerability, although users need to do this manually in the on-premises environment.
Additionally, researchers have identified 11,000 instances of this vulnerability, which are exposed online. Out of the identified instances, 8,500 are for the on-premises environment, which is particularly dangerous for the overall global IT infrastructure.
Why CISA Mandated a Three-Day Patch Deadline
CVE-2026-1731, was included in the Known Exploited Vulnerabilities (KEV) catalog maintained by the CISA on the 13th of February 2026. This triggered the activation of the Binding Operational Directive (BOD) 22-01, which demanded remediation on the spot. However, considering the fact that the vulnerability is currently being exploited, the CISA issued the deadline on the 16th of February.
Deadlines issued earlier for vulnerabilities requiring such quick turnarounds were only for vulnerabilities that threatened the very survival of the federal networks.
The warning issued by the CISA on the vulnerabilities indicates the fact that the vulnerabilities are being used frequently. The fact that authentication is not required for the exploitation of the vulnerability makes it a target for hackers. Once they get access, they can steal important information or cause harm. For such reasons, the CISA has recommended the agencies to stop using the products if they cannot remediate them.
BeyondTrust Remote Support and Privileged Remote Access instances are under active exploitation.
Remote Code Execution (RCE) via OS command injection in thin-scc-wrapper. Enables unauthenticated attackers to execute arbitrary system commands without user interaction.
CISA added this flaw to the KEV catalog, mandating federal agencies to patch by February 16, 2026. This urgency signals an existential threat to network security.
Over 11,000 instances are exposed online globally, with 8,500 being on-premises deployments. Automated exploitation attempts have been detected globally.
- Remote Support: 25.3.1 or earlier
- Privileged Remote Access: 24.3.4 or earlier
Note: SaaS instances were patched by early February. On-premises customers must initiate manual updates immediately.
Analyzing the Technical Impact of CVE-2026-1731
The successful exploitation of the vulnerability gives an attacker access to the same level of privileges as the user on the site. As BeyondTrust products manage privileged access, the scope for moving laterally within a network is considerable. There is also the capability to install malware, set up backdoors, or collect credentials. Further, the vulnerability does not require user interaction, which means that exploitation can happen silently. As such, an unpatched device is likely to be compromised.
- The use of automated tools to scan for BeyondTrust products that are left unpatched.
- The use of malicious payloads, which are delivered through specially crafted network requests.
- The use of command injection to set up backdoors.
- The use of data exfiltration, which is used to set up backdoors. After reconnaissance, exploitation can occur, which means that the time to effectively patch the vulnerability is quickly running out.
Historical Context of BeyondTrust Targeted Attacks
Products from BeyondTrust have been exploited by sophisticated attackers in the past. Two years ago, the U.S. Treasury Department was breached due to this same vulnerability. In this case, the attackers were the Chinese state-sponsored group known as Silk Typhoon. The attackers used zero-day exploits to breach 17 instances of the Remote Support SaaS product. The attackers were particularly interested in high-profile targets such as the Office of Foreign Assets Control (OFAC). As such, this vulnerability is currently of utmost priority for attackers of this nature.
This is further evidence that remote support tools are key targets for nation-state attackers due to their level of access to the internal network and the potential for surveillance. Furthermore, this attack also shows that attackers can utilize stolen API keys to compromise many systems. As such, CVE-2026-1731 is a key opportunity for attackers to replicate previous successes.
Conclusion: A 72-Hour Deadline That Signals Real Danger
CISA’s 72-hour mandate for CVE-2026-1731 is not routine patch guidance. It is an alarm that unauthenticated remote code execution in a privileged access tool can become full network compromise fast. With 11,000+ exposed instances and a CVSS 9.9, the window between scanning and takeover is measured in hours, not days.
Why This Threat Matters
BeyondTrust Remote Support and Privileged Remote Access sit on the most sensitive path in the environment, privileged access. When an internet-exposed instance is vulnerable, attackers can execute system commands without user interaction, then pivot to credentials, backdoors, and lateral movement.
Why Most Organizations Are Exposed
This is the failure pattern defenders keep repeating.
- On-premises deployments require manual updates, and patch lag is common
- Exposed management tools expand the blast radius immediately
- Versions impacted include Remote Support 25.3.1 and earlier, and Privileged Remote Access 24.3.4 and earlier
- Automated scanning and exploitation are already active
Patch immediately, reduce exposure, and enforce execution-time control across the estate.