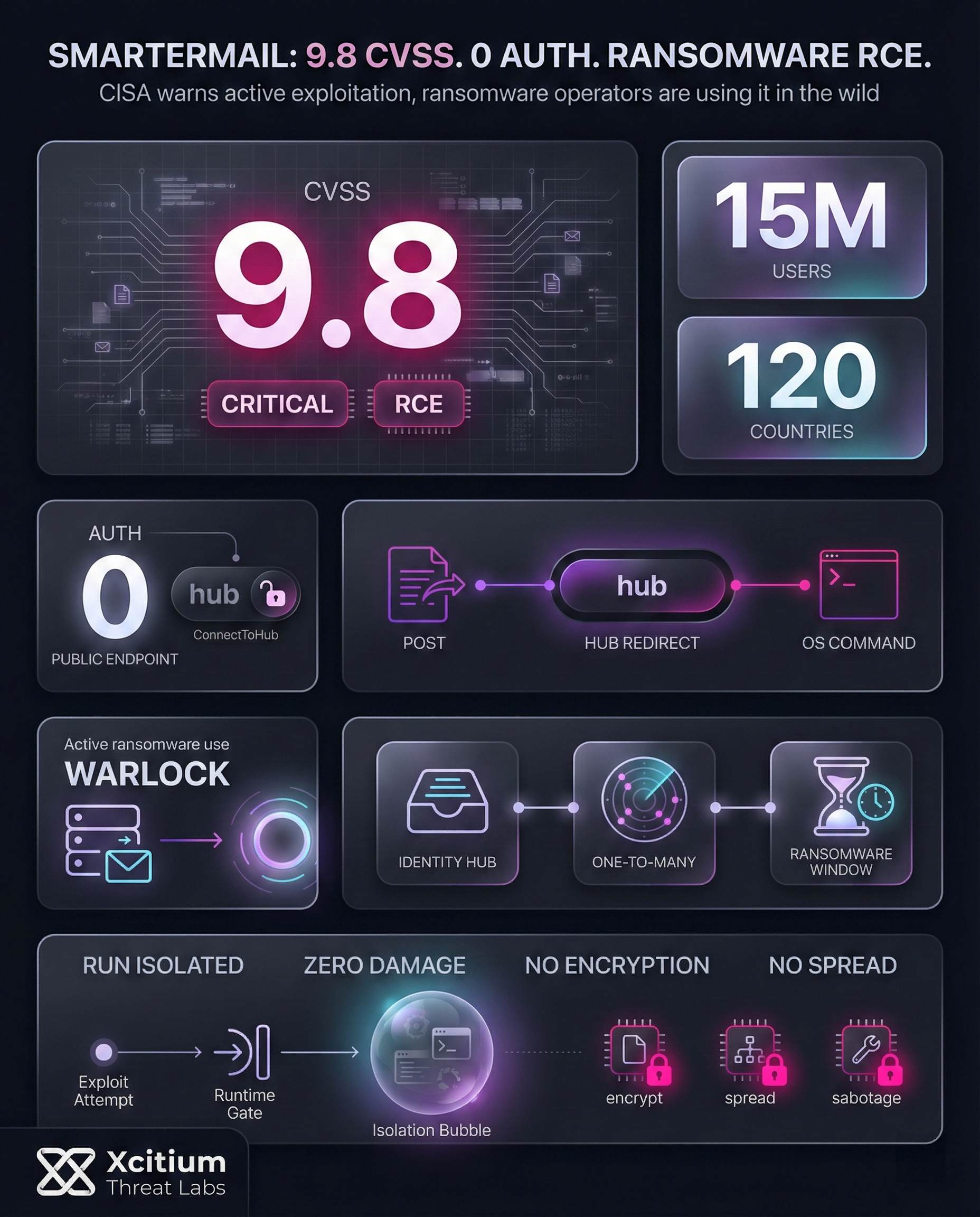
In early 2026, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) flagged a critical unauthenticated remote code execution flaw (CVE-2026-24423) in SmarterTools’ SmarterMail platform.
This bug affects all SmarterMail installations before version 100.0.9511, allowing anyone on the internet to execute arbitrary OS commands on the email server via the “ConnectToHub” API. With roughly 15 million users in 120 countries relying on SmarterMail, unpatched systems are at grave risk. CISA has even mandated that federal agencies patch or discontinue affected servers by Feb. 26, 2026.
Why SmarterMail’s RCE Flaw Matters
- Widespread Use: SmarterMail is used by managed services providers, small to midsize businesses, and hosting companies across the world. This application has 15 million users in 120 countries.
- Unauthenticated Access: This vulnerability does not need any authentication. Hackers can send requests directly to the ConnectToHub endpoint. This gives the attacker complete control over the server.
- Critical Severity: This vulnerability has an extremely high rating on the CVSS scale. According to the official sources, the rating is 9.8 out of 10 on the NVD. This is because it is easy to exploit the vulnerability and the impact is severe.
- Patch Availability: A patch has already been released by SmarterTools on January 15, 2026, in SmarterMail Build 9511.
These factors mean that a single exploited server could compromise entire email systems. Many organizations use SmarterMail to handle mission-critical email and calendar data. In practice, attackers would gain admin-level access to the server, endangering sensitive data and system integrity.
Inside CVE-2026-24423: How the Exploit Works
At its core, CVE-2026-24423 results from a missing authentication check in SmarterMail’s API. The ConnectToHub endpoint under /api/v1/settings/sysadmin/ does not require login. In a typical attack, an adversary sends a specially crafted POST request setting the hubAddress to a malicious server. The SmarterMail service then reaches out to that server and retrieves a JSON payload. Crucially, the payload contains a CommandMount parameter, which defines an arbitrary OS command that the server will execute. In effect, the attacker completely controls what code runs on the mail server.
- No Login Required: The “connect-to-hub” API endpoint is publicly accessible with no credentials needed.
- Malicious Redirect: By pointing the endpoint to an attacker-controlled URL, the server fetches and decodes attacker-supplied commands.
- Command Execution: The JSON response’s “CommandMount” can specify any OS command. If valid, SmarterMail executes it on the server.
- High CVSS Rating: NIST/NVD assigns this flaw a 9.8 (Critical) score, indicating that remote attackers can fully compromise the system with minimal effort.
In summary, any SmarterMail server reachable from the Internet is at immediate risk if this API is not secured. Attackers only need to send one crafted request to completely subvert the system.
Ransomware at Work: Real Attacks and Breaches
CISA and security researchers emphasize that this is not just theoretical. Active ransomware campaigns are already leveraging this flaw. For example, reports note that a cybercriminal gang known as “Warlock” exploited CVE-2026-24423 alongside a related SmarterMail flaw (CVE-2026-23760) to breach SmarterTools’ own network.
In that incident, the attackers redirected the mail server to a malicious hub and ran commands to gain control. Both bugs had critical CVSS scores (~9.3 each) and were patched together on Jan. 15. Unfortunately, one unpatched server in SmarterTools’ infrastructure enabled the breach, affecting some customers as well.
These real-world events demonstrate the danger:
- Warlock Ransomware: The “Warlock” group used the RCE bug and an admin-password-reset bug to fully hijack a SmarterMail instance.
- Immediate Impact: Once exploited, attackers can deploy ransomware or steal data. In the SmarterTools case, they turned the organization’s email servers against itself.
- Customer Exposure: Some SmarterMail customers were also impacted until the vendor released patches and mitigations.
These examples show that ransomware actors do not hesitate to weaponize SmarterMail flaws. All organizations running SmarterMail should assume they are targets.
Conclusion: One API Call Can Hand Over Your Mail Server
CVE-2026-24423 turns SmarterMail into an internet-facing takeover point. No credentials are required, and a single crafted request can trigger OS command execution through a exposed API path. CISA has already elevated the urgency, and ransomware groups are actively weaponizing the flaw.
Why This Risk Is So Dangerous
Email servers sit at the center of identity, workflows, and trust, so compromise is rarely isolated.
- Attackers can gain admin-level control and use the server as a launchpad for data theft and disruption
- Exploitation is fast, low-effort, and scalable against exposed instances
- Patch availability does not reduce risk, it increases attacker speed because scanning starts immediately
Where Organizations Stay Exposed
This is the recurring failure pattern behind RCE events.
- Publicly reachable admin or integration endpoints
- Patch lag across distributed deployments
- Assumptions that perimeter controls will absorb application-layer flaws
- Limited visibility into post-exploitation command execution on servers
Where Xcitium Changes the Outcome
If you have Xcitium, this attack would NOT succeed the way ransomware actors need.
- Vulnerability Assessment: This exposure should have been visible, vulnerable builds and risky internet-facing surfaces should be flagged before attackers find them.
- Advanced EDR: Even if exploitation is attempted, code can run without being able to cause damage, because malicious execution is intercepted at runtime before it can encrypt, spread, or sabotage operations.
Patch Fast, Then Remove the Attacker’s Advantage
SmarterMail is widely used, and this flaw is being exploited now. Patch immediately, reduce exposure, and enforce controls that stop ransomware at execution, not after recovery begins.