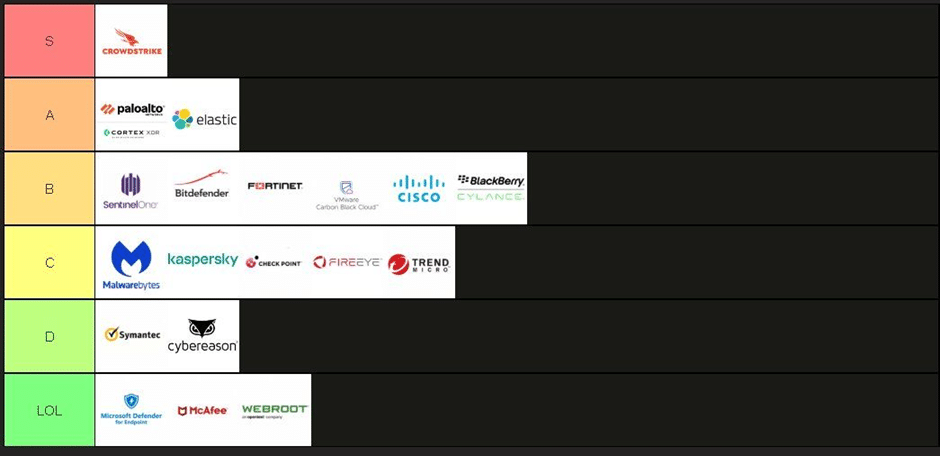
The Conti ransomware gang recently leaked an internal “EDR Tier List” on their Twitter (X) account, ranking popular endpoint protection products from “S Tier” (hardest to bypass) down to “LOL Tier”. This rare glimpse into attacker research shows how Conti’s operators judge EDR tools by how often and how easily they can evade them in real-world breaches. The tier list notably put Microsoft Defender for Endpoint (MDE) in the lowest “LOL” rank, sparking debate. The researchers note this likely reflects how often Conti sees poorly configured Defender installations: “Defender isn’t a bad product. But… it’s only as strong as its configuration. Too many organizations just run it out of the box… never enabling advanced protections”. In other words, a top‐tier tool can perform like a bottom-tier one if left at default settings.
Conti’s post even claims they can bypass every EDR on the list, noting only that “some require more work than others”. In plain terms, no EDR is foolproof against a patient, sophisticated adversary. As one analyst observed, “[Conti] claims they can bypass every EDR on the list… The message is clear: tools alone won’t save you. How you use them matters just as much—maybe more”. Another takeaway emphasizes that configuration and coverage count as much as the product itself: “Strong tools can become weak if left in their default state”. In fact, attackers joked that they’ll see if your “S Tier” product is really running in “LOL Tier mode because of poor setup or missing logs”. The leaky tier list thus validates what security professionals know: advanced EDRs can and will be evaded unless carefully deployed, tuned, and monitored.
What the Rankings Reveal: Vendors and Evasion
Although Conti’s published chart (and commentary) doesn’t list every product, it indicates how different vendors measure up to this gang’s red-team tactics. For example, CrowdStrike was singled out as “S Tier” – the toughest for Conti to bypass – while the lowest “LOL Tier” included Microsoft Defender for Endpoint, McAfee, and Webroot. Mid-range (“B Tier”) tools included the likes of SentinelOne, Bitdefender, VMware Carbon Black, and Cisco’s EDR, suggesting these products put up a respectable fight. Weaker products (C/D Tier) were deemed trivial obstacles. These placements aren’t an objective ranking of product quality, but rather a reflection of Conti’s own experiences with them. It’s telling that even leading EDR/XDR vendors know sophisticated ransomware teams repeatedly test ways around their defenses.
In effect, the leak documents mirror real-world attacker tactics. Conti’s notes confirm that they actively research each target’s security stack and exploit known gaps. Public reporting shows ransomware operators now often carry specialized “EDR killer” tools – for example, abusing vulnerable kernel drivers to disable or delete endpoint agents before deploying ransomware. As one analysis explains, attackers “abuse vulnerable drivers because they have kernel access… enabling [them] to kill processes for security products like EDR before they can detect malicious activity”. Tools like “EDRKillShifter” (developed by ransomware groups) are designed precisely to terminate EDR software at the driver level, ensuring the payload can run unobserved. Because most EDRs are built to detect malicious behavior (file encryption, unusual code injection, etc.), attackers invert the playbook by turning off those sensors altogether. Conti’s tier list simply catalogues which products have repeatedly been shut off or evaded during their breaches.
Key point: Conti’s evaluation isn’t academic – it’s battle-tested. Their operators share tips among themselves, breeding familiarity with how each EDR behaves in different environments. If an EDR has a known flaw or default weakness, attackers exploit it until it’s fixed. The public tier list, chat logs, and leaked manuals collectively show Conti runs its operation like a cybercrime “business”, with an “onboarding” process and tools, including guidelines on which defenses each operator should target or neutralize. In short, these leaked documents demonstrate the typical TTPs (tactics, techniques, and procedures) of a top-tier ransomware group: reconnaissance of defenses, disabling of protections (via misconfig or direct attack), and then lateral movement and encryption with minimal detection.
Implications for Security Programs
For organizations that rely heavily on EDR/XDR as the first (or sole) line of defense, Conti’s leak is a stark warning. It reiterates that no single vendor’s product is an impenetrable shield. A few implications stand out:
- Configuration is Critical: A poorly configured EDR can perform worse than a lesser product. As the leaked posts and experts note, an “S Tier” tool can effectively be in “LOL Tier” mode if its advanced features aren’t enabled or logs aren’t monitored. Organizations must go beyond default settings: enable all sensors, keep signatures and AI engines updated, whitelist-approved workloads, and tailor detection policies to the environment. This also means regularly auditing the EDR deployment to ensure agents are active on all endpoints and not disabled by faulty updates or insider actions.
- Defense-in-Depth: Relying solely on an endpoint agent is risky. Conti’s message – “tools alone won’t save you” – underscores that EDR should be one layer among many. Logging, network segmentation, multifactor authentication, vulnerability management, and user training all contribute to overall resilience. For example, even if malware bypasses or disables EDR, strong network segmentation can prevent it from spreading, while robust backups mitigate data loss. Similarly, a mature SOC will correlate events across sources (network logs, identity logs, etc.) so that even if the endpoint doesn’t flag an alert, other indicators (anomalous account behavior, suspicious traffic) can raise the alarm.
- Regular Red Teaming and Purple Teaming: The Damovo analysis emphasizes “Purple Teaming” – collaborative offense-defense exercises – as a crucial practice. Simulating real-world attacks (including EDR evasion techniques) helps validate that an organization’s combination of tools, processes, and people can actually stop today’s threats. For instance, ethical hackers on the blue team might see how far their EDR can detect a mimic of a Conti-style attack, then adjust. They will likely find that an untested EDR, left in default “ready to out-of-the-box” mode, may be blindsided by even simple evasion. The leaked tier list suggests defenders should assume adversaries will test all their defenses; thus, proactive testing is the only way to uncover blind spots ahead of an actual breach.
Guidance for Security and Incident Response Teams
For security operations centers (SOC), red teams, and incident responders, the Conti documents offer both threats and lessons:
- SOC/Detection Teams: Expect attackers to try disabling your EDR. Monitor for signs of tampering (disabled agent services, killed processes, unexplained agent gaps). Log and alert on any tampering events. Don’t ignore alerts from less prominent security tools either. As one commentator put it, “100% of EDR solutions can be bypassed”, so plan for it. Layer detection – e.g. use network IDS/IPS, logs from firewalls, application whitelisting – so that something still catches malicious behavior even if EDR is down. Also ensure that your incident response plans account for a “dark” host: have forensic tools and live response techniques ready to investigate a machine where EDR didn’t sound an alarm.
- Red Teams: Incorporate Conti’s techniques in your playbooks. Practice using “EDR killer” tools, credential theft, process injection, and exploiting Windows Defender’s known bypass paths. If your organization’s production environment looks like the average Conti target (e.g. mostly Windows, Office documents, some public-facing servers), try the same public tools (Meterpreter, Cobalt Strike, etc.) and see what bypasses the installed EDR. After each exercise, report on which tactics evaded detection and feed that back to the blue team for remediation. In short, use the leaked ranking as a tip sheet for which defenses to challenge first.
- Incident Responders: Recognize that in a Conti-style breach, the EDR may be deliberately neutered. Don’t assume absence of EDR alerts means absence of malicious activity. Collect other artifacts aggressively – memory dumps, forensic images, network captures – because your endpoint agent logs might be incomplete or tampered with. Develop scripts to check for disabled services and missing log entries. Also remember that Conti has historically dropped tools like Cobalt Strike on endpoints; watch for those fingerprints. The leak suggests attackers value stealth, so forensic timelines can help reconstruct events even if the EDR missed them.
Xcitium Perspective: Containment Over Evasion
From the viewpoint of Xcitium, Conti’s revelations reinforce the need for a fundamentally different approach than traditional EDR. Xcitium’s ZeroDwell technology does not rely solely on detection: it enforces a kernel-level virtualization container around any unknown application before it can touch the real system. As Xcitium explains, “unknown executables… are automatically isolated and allowed to run in a virtual container that does not access the endpoints and the host system’s resources or user data”. In other words, any suspicious or new file operates in a jailed environment by default. This “default-deny” stance means even if malware evades signature-based detection, it cannot do harm to the host while contained.
Practically, ZeroDwell treats every unrecognized process as potentially hostile. It contains threats first, and defers trust until the file is proven safe. As Xcitium puts it, their solution “isolates unknowns to prevent them from damaging endpoints at runtime… a ground-breaking default-deny solution [that] protects first, instantly, and automatically, thereby preventing breaches”. This contrasts sharply with typical EDR, which often allows the code to execute on the host (where it may disable or kill the EDR process). With Xcitium’s approach, even if a ransomware payload runs, it can only ever encrypt a virtual sandbox – never the real filesystem or memory.
In essence, kernel-level virtualization neutralizes the evasion techniques highlighted by Conti’s leak. An EDR killer tool can shut down the kernel driver of a Defender or Carbon Black agent, but it cannot escape or shut down a dedicated hypervisor isolating that process. Any attempts at unauthorized kernel manipulation simply never reach the actual kernel – they hit the containment layer instead. For defenders, this means that Conti’s tier list loses relevance: a “LOL Tier” tool running in Xcitium ZeroDwell mode is just as secure as an “S Tier” tool, because threats are quarantined out of harm’s way. In practice, this can reduce “dwell time” to effectively zero, since malware never sees user data or critical processes.
Conti’s ranking underscores that reactive defenses (even the best EDR) can be outsmarted by determined attackers. The lesson is to architect security so that evasion is meaningless. Xcitium’s kernel-virtualization containment is one response to this challenge: by default, don’t let the attacker interact with the real system at all. Instead of a cat-and-mouse of detection rules, give every unknown execution an immutable safety net. In combination with thorough logging and active monitoring, this model aims to stop ransomware in its tracks – consistent with ThreatLabs’ vision of “pre-emptive, no-dwell” security.
Final Overview
The Conti EDR tier list should be seen as a wake-up call, not as an EDR popularity contest. It reminds us that attackers test defenses relentlessly and will happily rank and exploit any weakness. Even the top products can be bypassed when misconfigured or targeted with novel tools. For defenders, the takeaway is to harden your tools and your processes. Audit and tune your EDRs, don’t rely on default settings, and invest in proactive testing (purple teams) and complementary controls. Meanwhile, consider defense architectures that limit attacker impact even if initial evasion succeeds – for example, executing unknown files in hardware-isolated containers rather than on the live OS.
As one analyst quipped, the real shame is having an “S Tier” solution running in “LOL Tier” mode. Use Conti’s rankings as motivation: test your stack thoroughly, fix any “LOL Tier” behavior, and ensure your EDR isn’t the weak link. Ultimately, in an age where “100% of organizations will suffer a breach” , we must treat every tool as part of a layered defense. EDR remains a powerful detection capability, but it must be part of a holistic strategy – from prevention and containment to vigilant monitoring and response – to stay one step ahead of attackers like Conti.