20,000 WordPress sites are vulnerable due to a backdoor in an Elementor add-on plugin, allowing attackers to create admin accounts and hijack those sites.
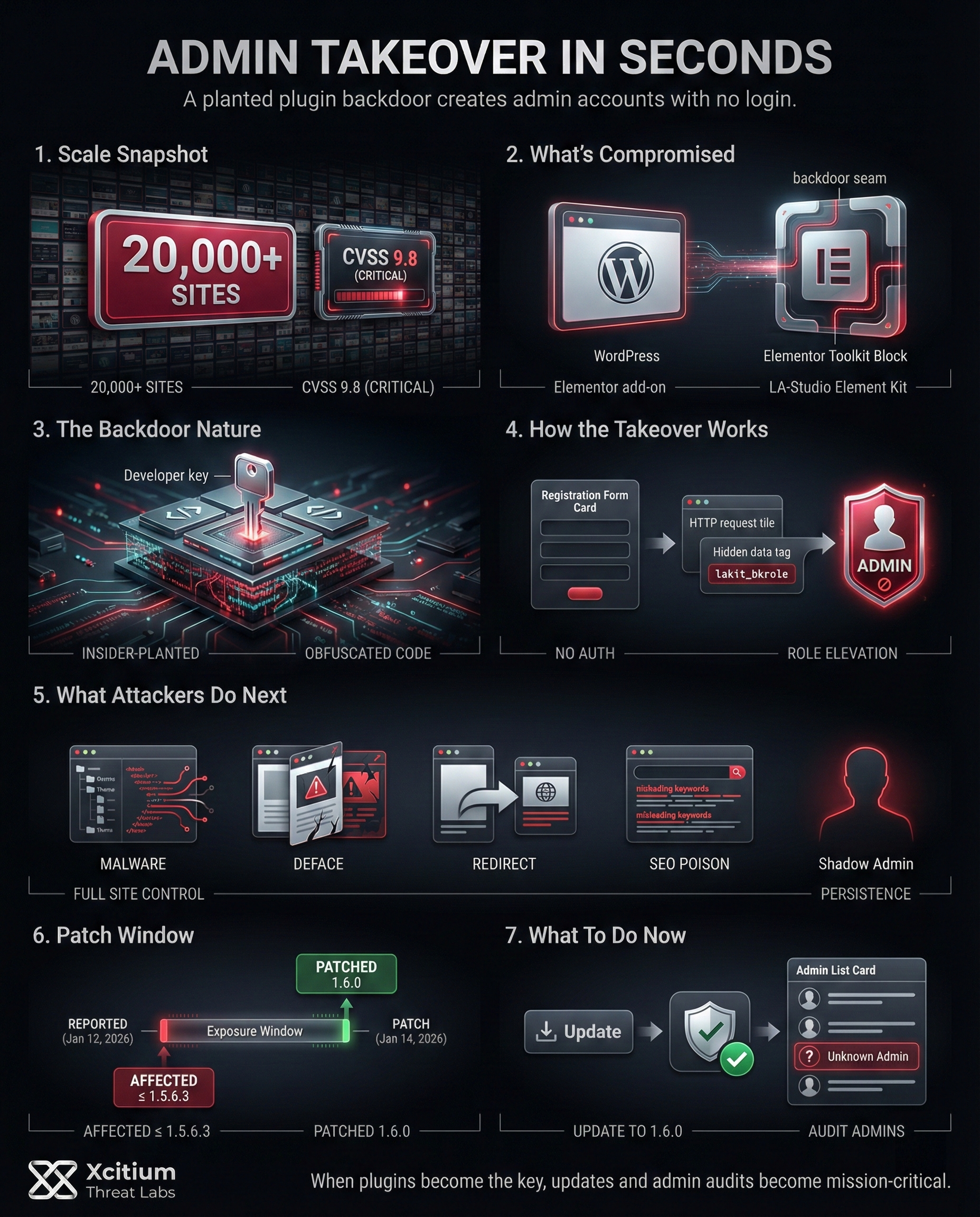
The discovery of a hidden backdoor in a popular WordPress plugin has put over 20,000 websites at serious risk. This critical vulnerability allows attackers to create administrator accounts without any login, essentially handing them the keys to affected sites.
As a result, an attacker could take over a vulnerable WordPress site in seconds installing malware, defacing pages, or stealing data at will. Given that WordPress powers over 40% of all websites, a flaw in a widely used plugin can have far-reaching consequences. In this case, the threat is especially alarming because the backdoor wasn’t an accident; it was intentionally inserted by an insider.
Backdoor in Popular Elementor Add-On Threatens Thousands of Sites
A critical flaw (tracked as CVE-2026-0920) was uncovered in the LA-Studio Element Kit for Elementor, a design toolkit add-on for the popular Elementor page builder. The plugin is installed on more than 20,000 WordPress sites. Moreover, the vulnerability earned a CVSS score of 9.8/10, reflecting its severity. It enables an attacker to register a new user account with administrator privileges without any authentication or admin invitation.
CVE-2026-0920
In other words, just by sending a specially crafted request, a hacker can silently make themselves an admin on someone else’s website. This kind of unauthenticated privilege escalation is extremely dangerous. Consequently, an attacker gaining admin access can wreak havoc across the site. The plugin’s developers urge all users to update to the patched version (1.6.0) immediately, as older versions (up to 1.5.6.3) are all vulnerable.
Insider Attack: Rogue Developer Planted the Malicious Code
- Deliberate backdoor insertion: Unlike the case of the accidental vulnerability, the backdoor was intentionally inserted by the former employee before leaving the company towards the end of 2025.
- Obfuscated malicious code: The backdoor was concealed using an obfuscation technique, which helped prevent it from being detected during code reviews.
- Insider threat risk: In this incident, it is evident that a serious risk is posed by trustworthy application developers who might intentionally add malicious code to an application.
- Need for stronger code audits: Developers are reminded to ensure strict codes are reviewed, particularly during transitions, to ensure no changes were made.
- Not an isolated case: WordPress plugins have previously contained intentional backdoors, such as the 2017 Display Widgets plugin incident that impacted over 200,000 websites.
- Broader security lesson: Both cases highlight the ongoing risks of inside threats, particularly those involving plugin ecosystems.
Unauthenticated Exploit Allows Full Site Takeover
The attack exploiting this backdoor is worryingly simple. By sending a specially crafted HTTP request during the normal user registration process, an attacker can include a hidden parameter (lakit_bkrole). The vulnerable plugin fails to restrict roles properly and interprets this secret parameter as a signal to elevate the new account to administrator. In addition, the malicious code was designed to blend into legitimate plugin functionality, so site owners would have no clue this was happening. Once an attacker has admin access, they effectively own the website. For example, a hijacker could:
Potential Impact of Compromise
These actions could get the site blacklisted by search engines and harm the business and visitors. Moreover, an admin backdoor lets attackers create additional hidden admin accounts or persist in other ways, making removal difficult. It’s a nightmare scenario for any website owner.
Rapid Response: Patch Released and Protection Measures
The good news is that this backdoor was quickly spotted by security researchers and the response has been swift. In fact, this bug was reported through a bug bounty program on the 12th of January, 2026. Within just two days of this discovery, on the 14th of January, 2026, a patch has already come out to address this issue and remove this backdoor code version 1.6.0. Thus, if you are using WordPress, it is imperative you check if you are using this plugin and update it right away. Also, you must check for unknown administrators who might have crept in.
The above scenario shows an example of what can happen when a plugin backdoor exists. This backdoor compromises tens of thousands of websites. Keeping plugins updated, verifying code integrity, and utilizing security tools can help significantly reduce the chances of such an attack. This is important since 90% of WordPress security issues are due to plugins.
Conclusion: When a Plugin Becomes the Admin Key
This incident is not a typical bug, it is a deliberately planted backdoor in a widely deployed WordPress plugin. With one crafted request, attackers can create an administrator account with no login, no invitation, and no warning, then take full control of the site in seconds.
Why This Threat Matters
A single admin takeover can quickly become business damage:
- Malware injection into themes and pages
- Defacement and reputation loss
- Traffic redirection to scams and phishing
- SEO poisoning that can trigger blacklisting
Why So Many Sites Are Exposed
This backdoor targets the reality of the WordPress ecosystem:
- Affected plugin versions up to 1.5.6.3 were installed at scale, 20,000+ sites are in the risk zone
- The exploit is unauthenticated, it elevates a new user to admin through a hidden role parameter
- The code was obfuscated, designed to survive casual review
- Patch speed matters, even short delays create a wide exploitation window