WPvivid Backup Plugin Hit by CVSS 9.8 RCE
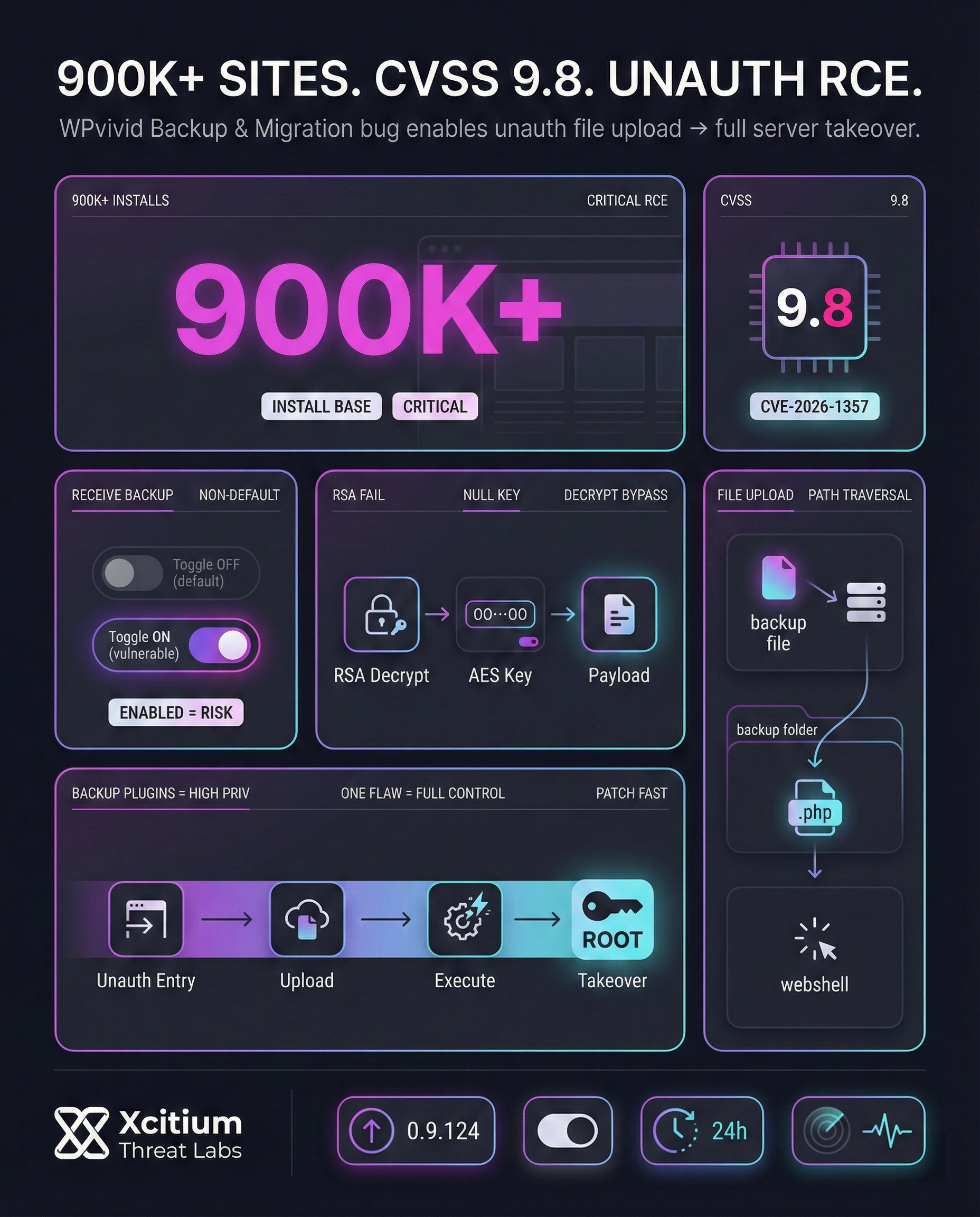
A new security vulnerability has been discovered in the WPvivid Backup & Migration plugin, which has 900,000+ installations. The security issue allows an attacker to perform unauthenticated file uploads on the vulnerable website, leading to RCE. The security issue has been rated 9.8 on the CVSS scale and has been assigned CVE-2026-1357. All versions of the plugin are vulnerable except for version 0.9.124. However, only sites that are running the non-default “receive backup” feature are vulnerable.
The attacker also has to use the one-time key that is valid for 24 hours. The security issue occurs due to the failure of the plugin to handle errors during RSA decryption and also the absence of filename sanitization. The issue has been fixed in version 0.9.124, released on January 28, 2026.
How the Vulnerability Works
The WPvivid flaw arises in the plugin’s backup transfer feature. When one site sends a backup to another, WPvivid uses RSA to encrypt/decrypt a session key. A decryption failure (e.g. wrong key) returns false, but the plugin fails to stop processing. Instead, it passes that boolean to an AES routine, which treats “false” as a null-byte key. This predictable key lets attackers craft a malicious backup payload that decrypts successfully despite an invalid key.
- Cryptographic error: If
openssl_private_decrypt()fails, the plugin does not abort; it feedsfalseinto AES, which becomes a known zeroed key. - File upload bypass: The attacker’s payload decrypts with this null key, carrying an arbitrary filename. The plugin does not sanitize this name, allowing directory traversal (e.g. “../”).
- Remote code execution: By traversing directories, the attacker can drop a
.phpwebshell or script outside the intended backup folder. When accessed, this executes on the server, giving full control.
Scope and Impact
- Wide install base: There are over 900,000 sites using the WPvivid Backup plugin. However, sites which have the “receive backup from another site” option enabled (it is disabled by default) are the ones which are immediately vulnerable. This option is likely to be used for migration operations, and thus the plugin may be enabled at least for a period of time.
- Exploit window: The keys for transferring the backups are valid for at most 24 hours. This limits the exposure to attacks. However, an attacker who gains access to the one-time key for a site can upload malicious files to the site during the 24-hour period.
- Real-world risk: Arbitrary file upload is a serious vulnerability in a site’s backup/migration plugin. If exploited, the site can be taken over by the attacker. There are chances for ransomware attacks, stealing data from the site, and using the site as a launchpad. Previous cases involving other WordPress plugins for site backups indicate that RCE vulnerabilities lead to site takeover.
Patch and Mitigation
A security update (version 0.9.124, released Jan. 28, 2026) addresses this issue. The fix adds proper error checking and limits file handling:
- Check RSA decryption: The plugin now halts if
openssl_private_decrypt()fails, preventing use of a null key. - Filename sanitization: Uploaded filenames are validated and cleansed to block directory traversal.
- Restricted file types: Only allowed backup file extensions (ZIP, GZ, TAR, SQL, etc.) can be uploaded.
Users should immediately update to v0.9.124 or later. Until patched, mitigation steps include:
- Disable “receive backup” feature: If not needed, turn off the cross-site backup option.
- Shorten key validity: If possible, set the key to expire sooner than 24h.
- Monitor and filter traffic: Use a web application firewall to detect unusual
wpvivid_action=send_to_siterequests. - Regular updates: Keep WordPress core and all plugins current, and audit backups for unfamiliar files.
Conclusion: A Backup Plugin Turned Into a Website Takeover Path
CVE-2026-1357 is a high impact flaw in WPvivid Backup and Migration, a plugin with 900,000+ installations. Under the right conditions, an attacker can upload files without authentication, traverse directories, and drop a PHP webshell, which leads to full remote code execution on the server.
Why This Matters Now
This is not a minor bug, it is a full compromise scenario.
- CVSS 9.8, with a direct path to code execution.
- Only sites with the non default Receive Backup feature enabled are exposed, but those sites are often in migration mode, which is when operational pressure is highest.
- The one time transfer key is valid for up to 24 hours, creating a short but dangerous window if the key is obtained.
Why Every Organization Is Vulnerable
Websites are now operational infrastructure, and plugin risk is supply chain risk.
- Backup and migration tooling is trusted by design, and often granted broad file system access.
- A single feature toggle can quietly create an internet facing upload surface.
- When attackers can place server side scripts, the website becomes the launchpad, not just the victim.
Where Xcitium Changes the Outcome
If you have Xcitium, this attack would NOT succeed.
- Vulnerability Assessment: This exposure should have been visible, vulnerable plugin versions and risky configurations like Receive Backup should be flagged before they become an incident.
- Advanced EDR: Even if a malicious file is dropped, code can run without being able to cause damage, because untrusted server side execution is intercepted at runtime before it can take over the host or deploy follow on payloads.
Patch Immediately, Then Close the Takeover Path
Upgrade WPvivid to 0.9.124 or later, and disable Receive Backup if you do not need it. Then enforce controls that prevent a file upload from becoming full server control.