DevMan Ransomware is rapidly emerging as a highly active threat. Explore its Conti roots, evolving attack tactics, targeted industries, and critical IOCs to detect and defend against ongoing campaigns.
The Emergence of DevMan Ransomware: A New RaaS Player
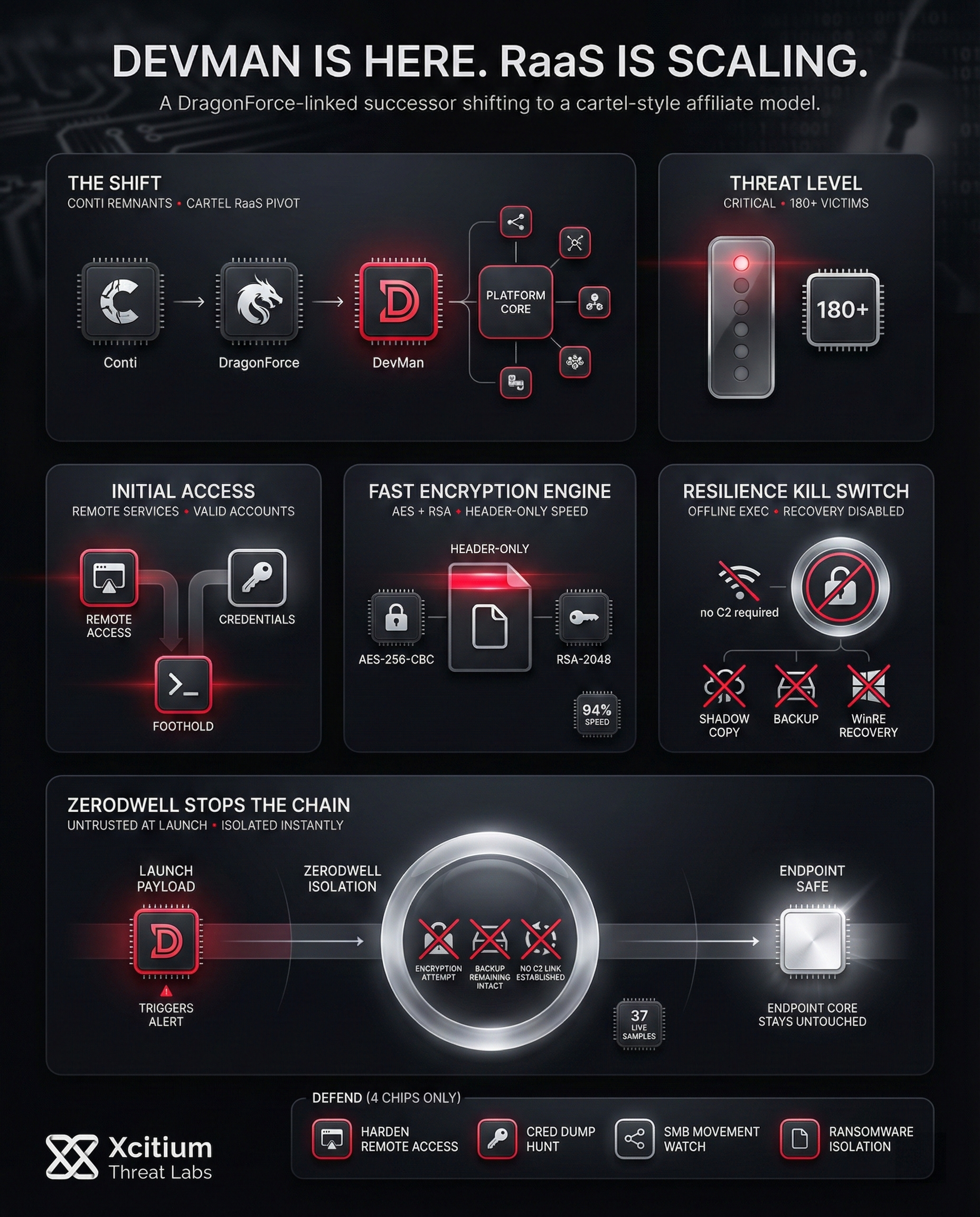
DevMan Ransomware is one of the most prominent rising threats of 2026. This operation is one of the fastest-growing ransomware operations that has quickly become one of the biggest players in the Ransomware as a Service (RaaS) field. The group first appeared in April 2025 but soon changed its model from a closed operation to a full-fledged RaaS with many different affiliates joining the operation.
The ransomware is not new but comes from a very infamous background. The code of the DevMan ransomware is directly linked to the infamous DragonForce and Conti ransomware groups. This indicates that the group is likely very powerful and comes from the ranks of very experienced cybercriminals. The first version of the malware was unusual in that it encrypted its own ransom notes. This did not stop the group from achieving great success in the future.
From Affiliate to Cartel: The Evolution of a Threat
History & Evolutionary Roots
Operational Structure
Core developers concentrate strictly on malware refinement, leaving execution to specialized affiliates.
Allows affiliates to “white-label” the payload, leading to unique variants that bypass standard defenses.
Unique variants and distinct deployment methods make unified defense and global tracking highly complex.
“The transition to a RaaS model marked a significant turning point, shifting from direct operations to a high-volume platform structure.”
The foundation of this group can be attributed to the remnants of the Conti operation, which, despite its fragmentation, continued with the code and affiliates in new forms. Among the most prominent forms was the DragonForce, and DevMan was one of the direct variants of this code. As such, this group has the advantage of years of development and refinement in attacks.
The shift to the RaaS in late 2025 was a major turning point in the evolution of this operation. This allows the core developers to focus on developing the malware and infrastructure, leaving the actual attacks and victim handling to the affiliates.
As such, the number and frequency of attacks have been greatly amplified. This RaaS operates on a “cartel” concept, allowing affiliates to create their own unique variants of the payload.
Who is at Risk? Targeted Industries and Global Reach
Organizations in these fields must heighten their defensive posture immediately. The group has claimed over 180 victims since its inception, showcasing its operational scale.
DevMan Intel Dashboard
Latest Attacks
| Target Entity | Threat Actor | Intelligence Metadata | Breach Summary |
|---|---|---|---|
| consultaegis.com | Devman |
Disc: 2026-01-29 Est: 2026-01-26 |
National security materials including BIO laboratory blueprints, facility details… |
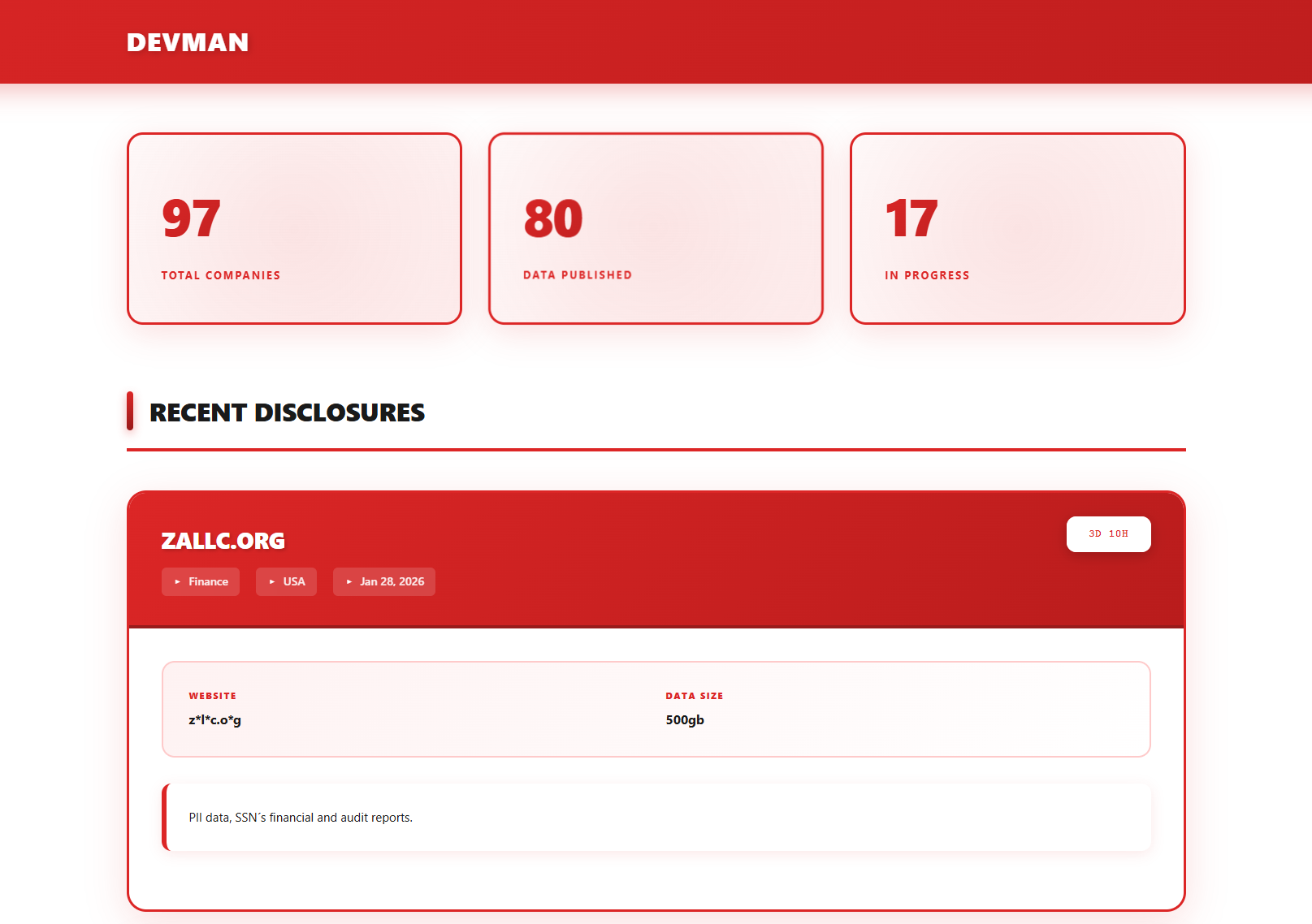
| zallc.org | Devman |
Disc: 2026-01-29 Est: 2026-01-28 |
PII data, SSN’s financial and audit reports…. |
| ***vandenberg.com | Devman |
Disc: 2026-01-28 Est: 2026-01-26 |
Client data, HR records, internal communications… |
| **ps.net | Devman | Disc: 2026-01-28 | N/A – Preliminary discovery phase. |
| tiw-group.com | Devman | Disc: 2026-01-28 | Specialist software firm with 30+ years experience. Source code and proprietary dev logs compromised. |
| z*l*c.o*g | Devman | Disc: 2026-01-28 | PII data, SSN’s financial and audit reports…. |
Technical Breakdown: Encryption and Behavior
Devman employs the highly secure AES-256 encryption algorithm in CBC mode to encrypt the victim files. Additionally, the malware employs RSA-2048 asymmetric encryption to encrypt the AES keys. This is the standard practice for contemporary ransomware.
DevMan has also employed sophisticated techniques to ensure maximum speed and evasiveness. For example, the malware variants employ header-only encryption. In this form of encryption, the malware encrypts only the header of the file. This form of encryption ensures the malware’s speed and allows it to compromise massive amounts of data within a short time.
Technical Schematics
DevMan Malware Execution & Cryptography
Prioritizes file start encryption to compromise large storage volumes in minimal time.
It has also been developed with an offline execution model. This means that the ransomware does not need an internet connection to the C2 server to initiate the encryption process. This makes the ransomware difficult to detect and prevent while it is in the process of attacking the system.
Moreover, it’s been developed with the anti-recovery mechanism. For instance, the malware executes commands that prevent the system from being restored. It achieves this by deleting the shadow copy and the backup files. This forces the victims to pay the ransom because the anti-recovery mechanism disables the system’s normal recovery processes.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique | Description |
|---|---|---|
| Initial Access (TA0001) | T1210 T1078 |
Exploitation of Remote Services: Exposed remote services such as RDP or management interfaces are abused to gain an initial foothold inside the environment without physical access. Valid Accounts: Compromised or reused credentials enable access through legitimate authentication mechanisms, allowing entry without triggering exploit-based alerts. |
| Execution (TA0002) | T1059.001 T1203 |
PowerShell: Native PowerShell functionality is used to run commands, deploy payloads, and automate actions while blending in with normal administrative activity. Exploitation for Client Execution: Vulnerabilities in client-side applications are leveraged to execute arbitrary code on the target system. |
| Persistence (TA0003) | T1078 | Valid Accounts: Continued access is maintained by reusing legitimate credentials, ensuring the ability to reconnect even after system restarts or partial cleanup. |
| Privilege Escalation (TA0004) | T1068 | Exploitation for Privilege Escalation: Local software flaws or misconfigurations are exploited to elevate access from a standard user to administrative or system-level privileges. |
| Defense Evasion (TA0005) | T1036 T1562 |
Masquerading: Files, processes, or services are deliberately named or structured to resemble legitimate components, reducing the chance of raising suspicion. Impair Defenses: Security controls such as endpoint protection, logging, or monitoring features are disabled or altered to limit visibility into malicious activity. |
| Credential Access (TA0006) | T1003 | OS Credential Dumping: Authentication material is extracted from memory or system credential stores, enabling account takeover and further network access. |
| Discovery (TA0007) | T1018 T1046 T1082 |
Remote System Discovery: Networked systems are identified to map the internal environment and locate potential lateral movement targets. Network Service Scanning: Active services and open ports are enumerated to understand reachable systems and exposed functionality. System Information Discovery: Host-level details such as operating system version, hostname, and hardware attributes are collected to guide next-stage actions. |
| Lateral Movement (TA0008) | T1021.002 | SMB / Windows Admin Shares: Administrative shares are used to move between systems using valid credentials and existing Windows file-sharing mechanisms. |
| Collection (TA0009) | T1005 | Data from Local System: Files and sensitive data are gathered directly from compromised hosts in preparation for exfiltration or encryption. |
| Exfiltration (TA0010) | T1041 | Exfiltration Over C2 Channel: Collected data is transferred out of the environment through an established command-and-control communication path. |
| Impact (TA0040) | T1486 T1490 T1491 |
Data Encrypted for Impact: Data and systems are encrypted to disrupt operations and pressure victims into paying a ransom. Inhibit System Recovery: Backup files and recovery mechanisms are removed or disabled to limit restoration options. Defacement: Visible artifacts such as ransom notes or modified content are introduced to signal compromise and communicate demands. |
Case Study: Xcitium vs. DevMan Ransomware
This demonstration illustrates how Xcitium defends systems against ransomware in real time using a prevention-first approach. 37 live Devman ransomware samples are executed in a controlled environment to simulate a realistic multi-payload attack scenario.
Instead of relying on signatures, reputation, or post-execution detection, Xcitium’s ZeroDwell isolation technology automatically identifies each Devman payload as untrusted at launch and immediately places it into isolation.
As a result, Devman is unable to complete its attack chain. File encryption attempts are blocked, backups remain intact, and no command-and-control communication is established even though the samples are fully functional and previously unseen.
By eliminating the exposure window entirely, Xcitium ensures the endpoint remains fully operational and uncompromised. This video demonstrates how modern ransomware threats like Devman are neutralized instantly through continuous, zero-trust execution and real-time isolation.
Indicators of Compromise (IOCs) for Network Defense
Identifying and blocking the infrastructure used by DevMan affiliates is a critical defensive measure. Indicators of Compromise (IOCs) are forensic artifacts that signal a potential breach or ongoing attack. Consequently, organizations should integrate these indicators into their security monitoring tools immediately.
The following IOCs have been associated with DevMan operations :
- 83.217.209.210
- 38.132.122.213
- 38.132.122.214
- TOX ID: 9D97F166730F865F793E2EA07B173C742A6302879DE1B0BBB03817A5A04B572FBD82F984981D
- Website: devmanblggk7ddrtqj3tsocnayow3bwnozab2s4yhv4shpv6ueitjzid.onion
- Twitter/X: @Inifintyink
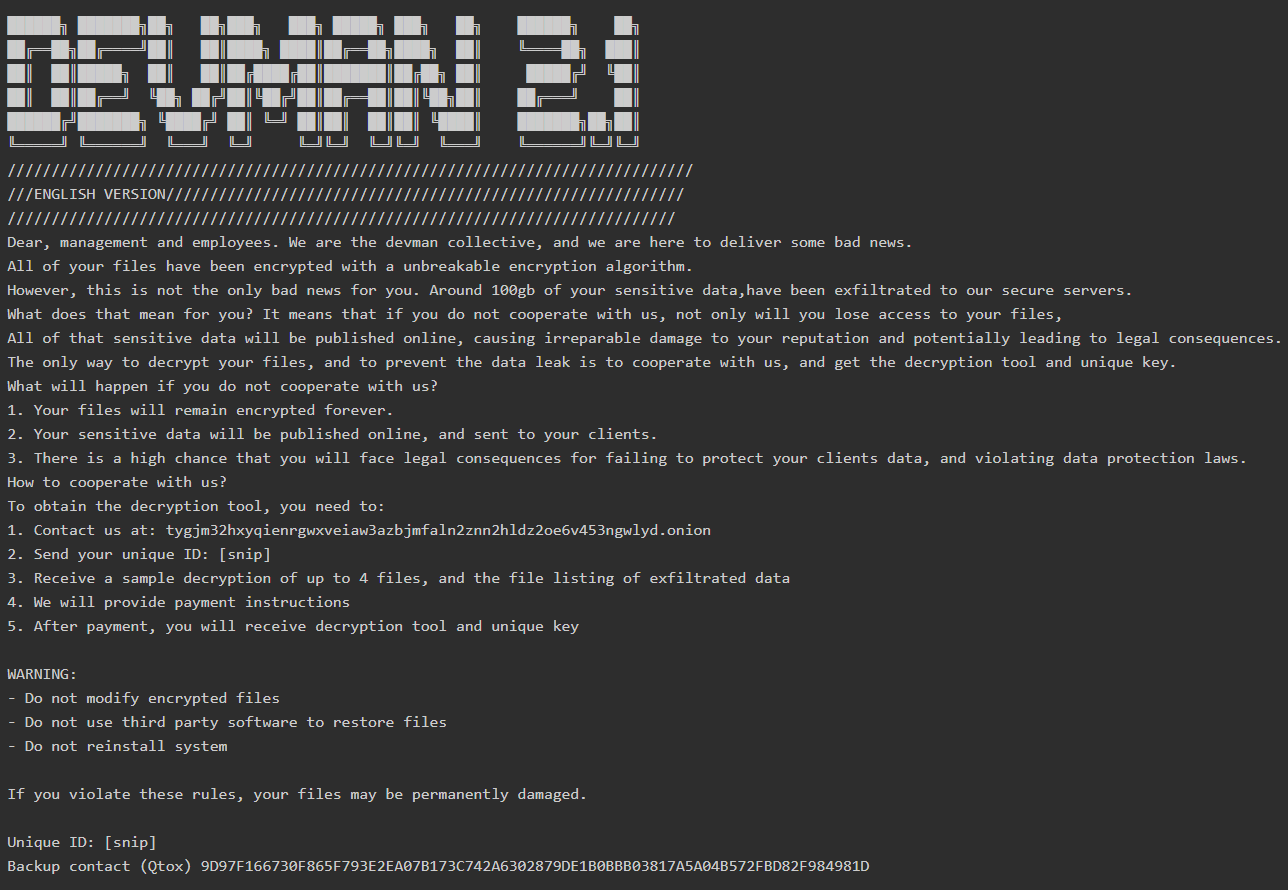
These indicators provide actionable intelligence for network defenders. For example, blocking traffic to these IP addresses can disrupt communication with the attacker’s C2 infrastructure. Therefore, proactive threat hunting using these IOCs can help identify and contain an infection before it spreads.
DevMan Ransomware SHA-1 Samples & Zero‑Dwell Threat Intelligence Reports
Conclusion: DevMan Proves RaaS Is Now Built for Speed and Scale
DevMan is not just another ransomware strain, it is a high-volume RaaS operation built on proven code lineage tied to DragonForce and Conti, then amplified through affiliates and variant white-labeling. With 180+ claimed victims, it reflects a business model engineered for reach, pressure, and repeatable impact.
Why This Threat Hits Hard
- Affiliates drive constant attacks across industries, with Technology as the top target, and Healthcare and the Public Sector as high-pressure follow-ons.
- Strong encryption is paired with tactics that reduce response time, including fast encryption methods and offline execution.
- Recovery is deliberately weakened through shadow copy and backup disruption.
Where Xcitium Changes the Outcome
For organizations protected by Xcitium Advanced EDR, DevMan fails at execution.
- Unknown payloads are isolated the moment they run, even if they are never-before-seen.
- Encryption attempts cannot touch real files, operations remain stable, and recovery stays viable.
- In the demonstrated scenario, 37 live samples could execute, but code can run without being able to cause damage.
Stop the Next Affiliate Before Impact
RaaS groups win when execution is allowed, even briefly. Eliminate that window, stop unknown code at runtime, and keep ransomware irrelevant.




