Explore Nova ransomware (formerly RALord) its recent attacks, evolution, and key indicators. Learn how this RaaS group operates, stats on victims, and MITRE-based tactics.
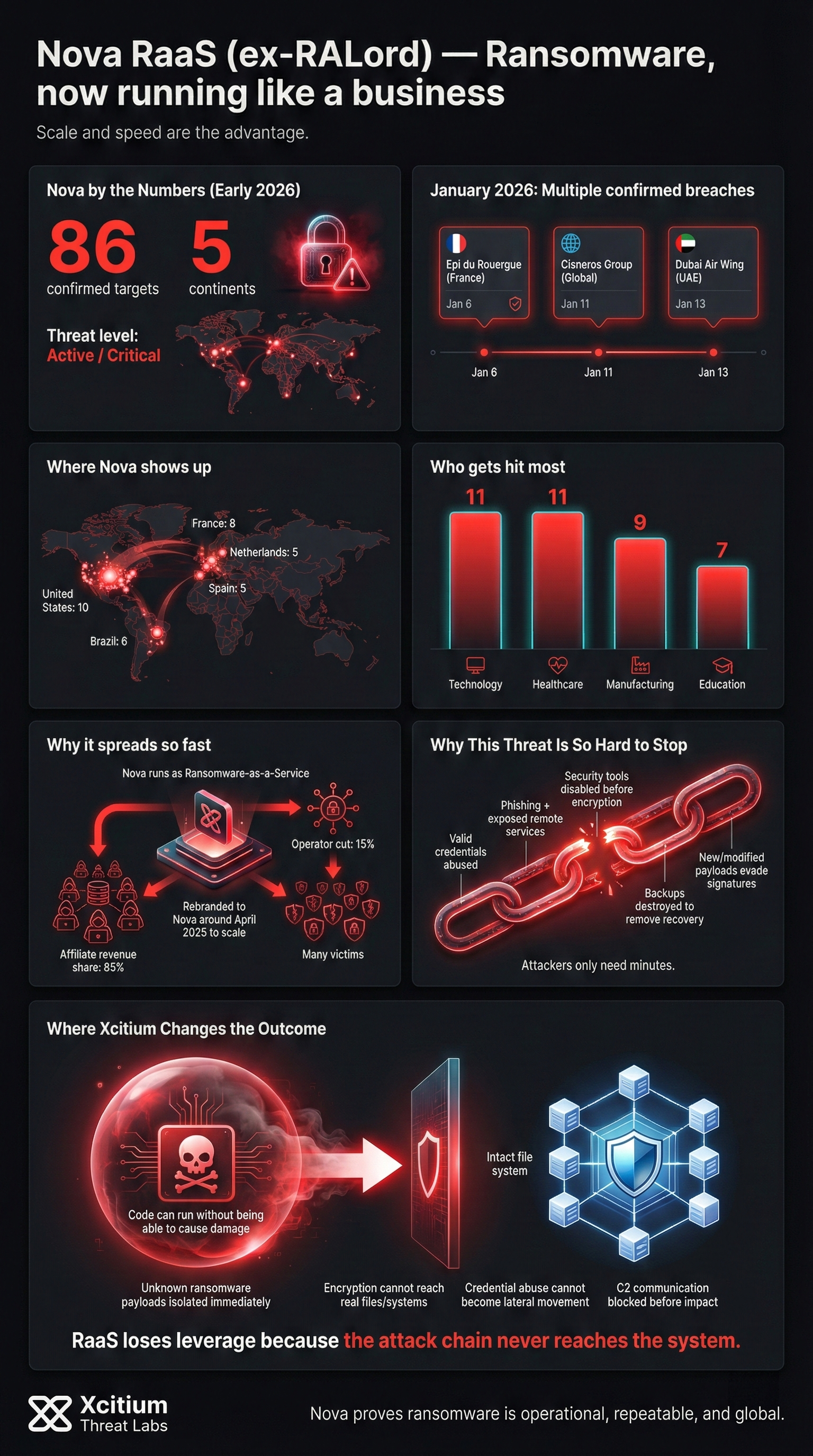
This group, which was previously known by the name RALord, rebranded in approximately April 2025. Therefore, it did not take them long to become a force to be reckoned with in the ransomware-as-a-service (RaaS) market. The fact is that the number of victims they have targeted stands at over 86, spread across five continents by early 2026.
For instance, in January 2026, Nova launched several confirmed attacks, including the breach of Epi du Rouergue, which is a food production company, on January 6, followed by an attack on the Cisneros Group, a global conglomerate in the media and entertainment sectors, on January 11, and an attack on Dubai Air Wing on January 13, in which the group claimed to have breached systems and stolen internal data.
Nova Ransomware by the Numbers 2026
d=Day
Major Nova Attacks and Targets
Some notable Nova incidents include:
- Dubai Air Wing (UAE, January 13, 2026): This is another organization in the UAE that was listed on the leak site by Nova for having its internal information stolen.
- Cisneros Group (Global, January 11, 2026): The attackers focused on this large media and entertainment conglomerate, boasting that they had gained access to the company’s systems and stolen important business information.
- Epi du Rouergue (France, January 6, 2026): Nova launched an attack on this company that produces food, encrypting their internal systems and including it in their leak list.
- Novabio Laboratories (France, December 10, 2025): The attacker, named Nova, announced that they had encrypted approximately 500GB of data from this lab, which was a healthcare facility, and asked for payment in return for the decryptor.
- ANG BROTHERS (Singapore, December 2025): The syndicate announced a breach on this plumbing & HVAC company, warning of a data dump of 2.5TB of stolen corporate data if a ransom wasn’t paid.
- Clinical Diagnostics (Netherlands, July 2025): This was the cancer screening lab that Nova targeted, encrypting the systems and taking valuable patient information. After the first ransom payment, the gang unexpectedly doubled the ransom, reflecting the unpredictability of the extortion practices of Nova.
Nova Operational Profile
The group aims for rapid growth by attracting more attackers with a lower operational cut.
Rebranding and RaaS Model
Initially, Nova operated as RALord in March of 2025, following the conventional RaaS affiliate business model. The affiliates received approximately 85% of any ransom payment, while the operators received the remaining amount. Towards the end of April 2025, the group renamed its leak site “Nova.” However, it continued to offer similar services.
Moreover, the new portal brought with it functionalities such as the “Nova Chat” channel and the affiliate registration form. Security researchers point out that the tactics used by Nova resemble those used by ransomware attackers, where the attackers enter the system (either through phishing attacks or exposed services) and proceed to shut down the backups and security solutions before stealing and/or encrypting the data. Thus, the progression of Nova indicates efficiency, where the attackers quickly rebrand and use the affiliate program to deliver the payload.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique | Description |
|---|---|---|
| Initial Access (TA0001) | T1078 T1566 T1133 |
Valid Accounts: Attackers use stolen or compromised credentials, often obtained via infostealer malware, to gain initial access. Phishing: Nova affiliates deliver the initial payload via phishing emails with malicious attachments or links. External Remote Services: Exposed RDP and VPN services are abused using stolen credentials to access internal networks. |
| Execution (TA0002) | T1059 T1204 |
Command and Scripting Interpreter: Nova executes commands using PowerShell, CMD, and its Rust-based ransomware payload. User Execution: The victim is tricked into running a malicious file, often delivered through phishing. |
| Persistence (TA0003) | T1547 T1133 |
Boot or Logon Autostart Execution: Registry run keys or startup folders are used to maintain persistence. External Remote Services: Previously compromised RDP or VPN access is reused to keep access. |
| Privilege Escalation (TA0004) | T1078 T1068 |
Valid Accounts: Stolen administrator or domain credentials are used to gain elevated privileges. Exploitation for Privilege Escalation: Local vulnerabilities are exploited to gain higher-level access. |
| Defense Evasion (TA0005) | T1027 T1497 T1070 |
Obfuscated Files or Information: Nova’s Rust-based payload provides inherent obfuscation. Virtualization/Sandbox Evasion: Delayed execution and environment checks evade analysis. Indicator Removal on Host: Logs and forensic artifacts are deleted. |
| Discovery (TA0007) | T1083 T1082 T1012 |
File and Directory Discovery: Nova scans systems to identify files for encryption. System Information Discovery: OS and configuration details are collected. Query Registry: Registry keys are queried to detect security software. |
| Lateral Movement (TA0008) | T1021 T1550 |
Remote Services: RDP and SMB are used for lateral movement. Use Alternate Authentication Material: Pass-the-hash and similar techniques enable movement without passwords. |
| Collection (TA0009) | T1005 T1074 |
Data from Local System: Sensitive data is collected from compromised hosts. Data Staged: Data is staged locally before exfiltration. |
| Exfiltration (TA0010) | T1048 | Exfiltration Over Alternative Protocol: Stolen data is transferred to attacker-controlled infrastructure using cloud services or custom protocols. |
| Impact (TA0040) | T1486 T1490 T1491 |
Data Encrypted for Impact: Files are encrypted and the .ralord extension is added.Inhibit System Recovery: Backups and Shadow Copies are deleted. Defacement: Ransom notes and desktop changes are used to intimidate victims. |
Case Study: Xcitium vs. Nova Ransomware
This demo illustrates how Xcitium protects against the Nova ransomware in real-time during a live attack simulation. A number of Nova variants are deployed to simulate a sophisticated attack attempt on a large scale. Contrary to other security tools that wait for cloud responses or signature patterns to identify threats, the Zero-Dwell functionality in Xcitium considers all unknown processes as malicious and isolates them upon execution.
Because of this automatic isolation, the capabilities that the Nova malware lacks include encrypting files, persisting in the system, and communication with the command and control server, even for new or altered versions that have not been seen before.
With Xcitium, this exposure window is eliminated altogether, providing constant security that keeps your systems up and running and your data protected. This video shows how current ransomware attacks, like Nova, are instantly protected against by Xcitium’s prevention-led, Zero-Dwell strategy.
Indicators of Compromise (IOCs)
Key IOCs associated with Nova include:
- Session token:
054f55ec93aca9bac362b9d91eff36a7ce451e7caba47c0b2e004ba429f9529c79(A unique identifier used in Nova’s ransom negotiations.) - Tox ID:
8E9A6195A769FE7115F087C61D75CF32874C339B3AB0947D07480C9A8A12DA5009151BE6A51F(QtOx encrypted chat ID linked to Nova operators.) - File extension:
.ralord(Extension appended to files encrypted by Nova / former RALord.) - Malware hash (SHA-256):
456B9ADAABAE9F3DCE2207AA71410987F0A571CD8C11F2E7B41468501A863606 - Malware hash (MD5):
be15f62d14d1cbe2aecce8396f4c6289 - Ransom note filename:
README-.txt - Tor leak & negotiation sites (.onion):
novavdivko2zvtrvtllnq45lxhba2rfzp76qigb4nrliklem5au7czqd.onion
pifk3xu3vad6cuxsjll4qjomyaaaoyvnyqppro75pazadzctrrvpdnyd.onion
novadmrkp4vbk2padk5t6pbxolndceuc7hrcq4mjaoyed6nxsqiuzyyd.onion
For example, tracking these signs like the .ralord extension or known QtOx IDs can help defenders spot a Nova breach early. Vigilant monitoring for these IOCs can trigger rapid response to any infection.
Nova Ransomware SHA-1 Samples & Zero‑Dwell Threat Intelligence Reports
Conclusion: RaaS at Scale, Destruction at Speed
Nova’s evolution from RALord into a mature RaaS operation shows how quickly ransomware groups adapt, rebrand, and expand. In less than a year, Nova affiliates compromised dozens of organizations across healthcare, manufacturing, education, and critical services worldwide. The playbook is familiar but devastating, stolen credentials, exposed services, rapid lateral movement, data theft, then encryption and extortion. Scale and speed are now the advantage.
Why This Threat Is So Hard to Stop
Modern RaaS groups like Nova succeed because they exploit common weaknesses that persist across environments:
- Valid credentials abused for initial access
- Phishing and exposed remote services bypassing perimeter defenses
- Security tools disabled before encryption begins
- Backups destroyed to eliminate recovery options
- New or modified payloads evading signature-based detection
When unknown code is allowed to execute freely, attackers gain minutes or hours. That is all ransomware needs.
Where Xcitium Changes the Outcome
For organizations using Xcitium Advanced EDR, Nova ransomware fails at the point of execution.
- Unknown ransomware payloads are isolated immediately
- Encryption routines cannot access real files or systems
- Credential abuse cannot escalate into lateral movement
- Command and control communication is blocked before impact
- Code can run without being able to cause damage
Affiliates lose their leverage because the attack chain never reaches the system.
Stop RaaS Before It Becomes a Business Crisis
Nova proves that ransomware is no longer rare or slow. It is operational, repeatable, and global. Defense must move faster than affiliates can deploy payloads.
Protect your endpoints before encryption begins.
Choose Xcitium Advanced EDR, powered by the patented Zero-Dwell platform.




