
Global-e data breach exposed personal info of Ledger customers. Learn what was leaked, why your crypto is still safe, and how to protect yourself against scams.
Third-Party Breach Hits Ledger’s Checkout
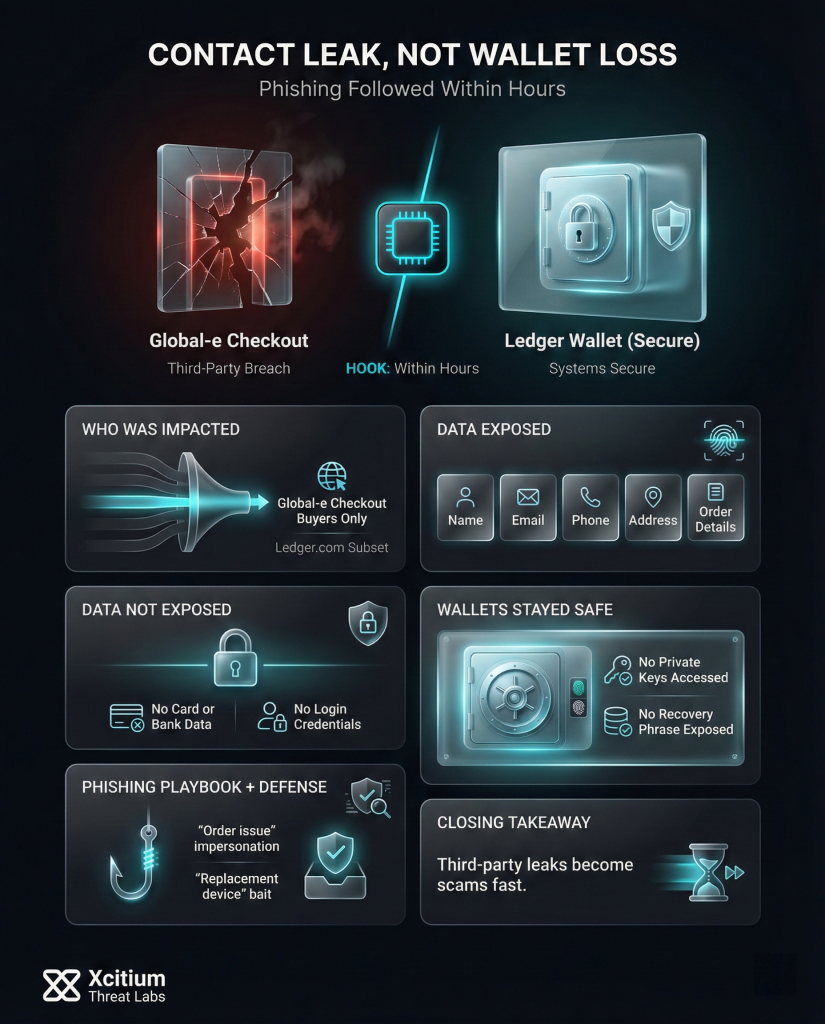
Recently, hackers breached Global-e’s systems, the payment platform used by Ledger for online orders. As a result, personal order information for some Ledger.com customers may have been exposed. However, Ledger confirms that its own network, hardware wallets, and software remain secure.
In fact, only customers who bought directly through Global-e’s checkout service were impacted. Exposed data consisted of names and contact details for those customers not any financial or wallet secrets. Global-e, which handles checkout for many retailers, immediately isolated its affected systems and is notifying the users and regulators involved.
Exposed Data and Impact on Customers
Affected customers should note which data fields were taken. The breach exposed typical order records, including:
- Names and contact info: Customer full names, email addresses, and phone numbers.
- Shipping addresses: Postal addresses used for deliveries.
- Order details: What was purchased, order numbers, dates and prices.
Ledger explicitly stated that no payment card or bank account data was exposed. Equally important, the attackers never obtained any customer wallet secrets. Global-e never had customers’ 24-word recovery phrases or private keys, so those remain safe.
In short, this breach exposed personal contact info from purchase records which can be misused for scams but it did not compromise any financial or blockchain account data.
Ledger Wallets Are Safe
It must be noted that this attack did not in any manner influence the safety of the crypto assets of the users. Ledger has confirmed that the hackers did not access any hardware, Ledger Live accounts, or cryptocurrency balances. Since the Global-e payment service provider only processed orders, the hackers gained zero access to the users’ private keys and recovery phrases.
As a result, hackers cannot access any of their wallets directly or steal money from them. In addition to this, Global-e also confirmed that there were no login credentials and payment information stolen. Thus, despite the leakage of personal information, their cryptocurrencies are securely locked away in their hardware wallets.
Protect Yourself: Phishing Risks and Next Steps
Risks of Phishing and What to Do Next With your name and address in plain sight, it’s phishing that you should worry about. Scammers tend to use leaked information in creating spam messages. To be precise, it was reported that within hours of news about the breach, customers of Ledger received phishing messages that claimed to come from Ledger or Global-e. Scammers might say there’s an issue regarding your purchase or that you should “verify” your account information.
It’s important that you are not lulled into complacency by these scams. According to Ledger, you should never, under any circumstances, share your 24-word recovery word.
Common Scam Tactics Already Being Observed
Attackers are sending emails and text messages pretending to be Ledger or Global-e, claiming that there is a “problem with your order,” a “security issue with your wallet,” or that a “replacement device” is required. Some messages even include your real name or address to appear legitimate. These messages always aim to trick users into revealing their recovery phrase or installing fake software.
Follow these safety steps:
Essential Safety Checklist
Protect Your Recovery Phrase
Never share your seed phrase or passwords. Ledger will never ask for your recovery words or login info.
Verify Contacts & Links
Treat unsolicited emails/calls with suspicion. Always check sender details and avoid clicking unfamiliar links.
Use Official Channels Only
Visit the official site and use Ledger Live for all updates. Never enter sensitive info on sites reached via email.
Enable Strong Security
Use unique passwords and 2FA (Two-Factor Authentication) for all email and crypto-related accounts.
For example, after a 2020 data leak of about 270,000 Ledger users, scammers mailed fake “replacement” Ledger devices to victims. That incident underlines why extra caution is needed: always verify hardware sources and be skeptical of any unsolicited offers. Global-e will contact potentially impacted customers via email check your inbox for a message from them, and read it carefully.
In addition, stay updated with official Ledger communications and ignore any pressure tactics. By remaining vigilant and following these recommendations, you can minimize the risk that attackers will succeed in tricking you.
Conclusion: A Data Leak That Turns Into a Phishing Attack
The Global-e breach shows how third-party incidents create immediate real-world risk for customers, even when core systems remain secure. Ledger confirmed its network, hardware wallets, and wallet secrets were not accessed. The exposed data was purchase and contact information, which is exactly what scammers need to run convincing follow-up scams.
Why This Still Matters
This is the pattern organizations keep underestimating.
- Names, emails, phone numbers, shipping addresses, and order details enable high-conversion impersonation
- “Order problem” and “security verification” messages become believable when attackers know what you bought
- The goal is not account takeover first, it is recovery phrase theft and fake software installs
- The breach impact escalates after disclosure, when attackers weaponize attention and urgency
Where Xcitium Changes the Outcome
For organizations using Xcitium Cyber Awareness Education and Phishing Simulation, scams like these lose their power.
- Employees learn to identify impersonation patterns and pressure tactics
- Simulated attacks build pause and verify behavior before any sensitive action
- Suspicious links, forms, and “urgent wallet warnings” get challenged, not followed
- Code can run without being able to cause damage when the user never completes the attack
If you have Xcitium in place, this attack fails at the human decision point, before any recovery phrase or credential is ever exposed.
Protect Customers After the Breach, Not Only During It
Third-party leaks are inevitable. What matters is whether social engineering succeeds afterward. Train users to resist the exact tactics attackers deploy next. Choose Xcitium Cyber Awareness Education and Phishing Simulation.




