Discover the tactics, victims, and statistics of Lynx Ransomware. Learn how this double-extortion threat evolved from INC Ransomware and how to protect your business.
Overview of Lynx Ransomware
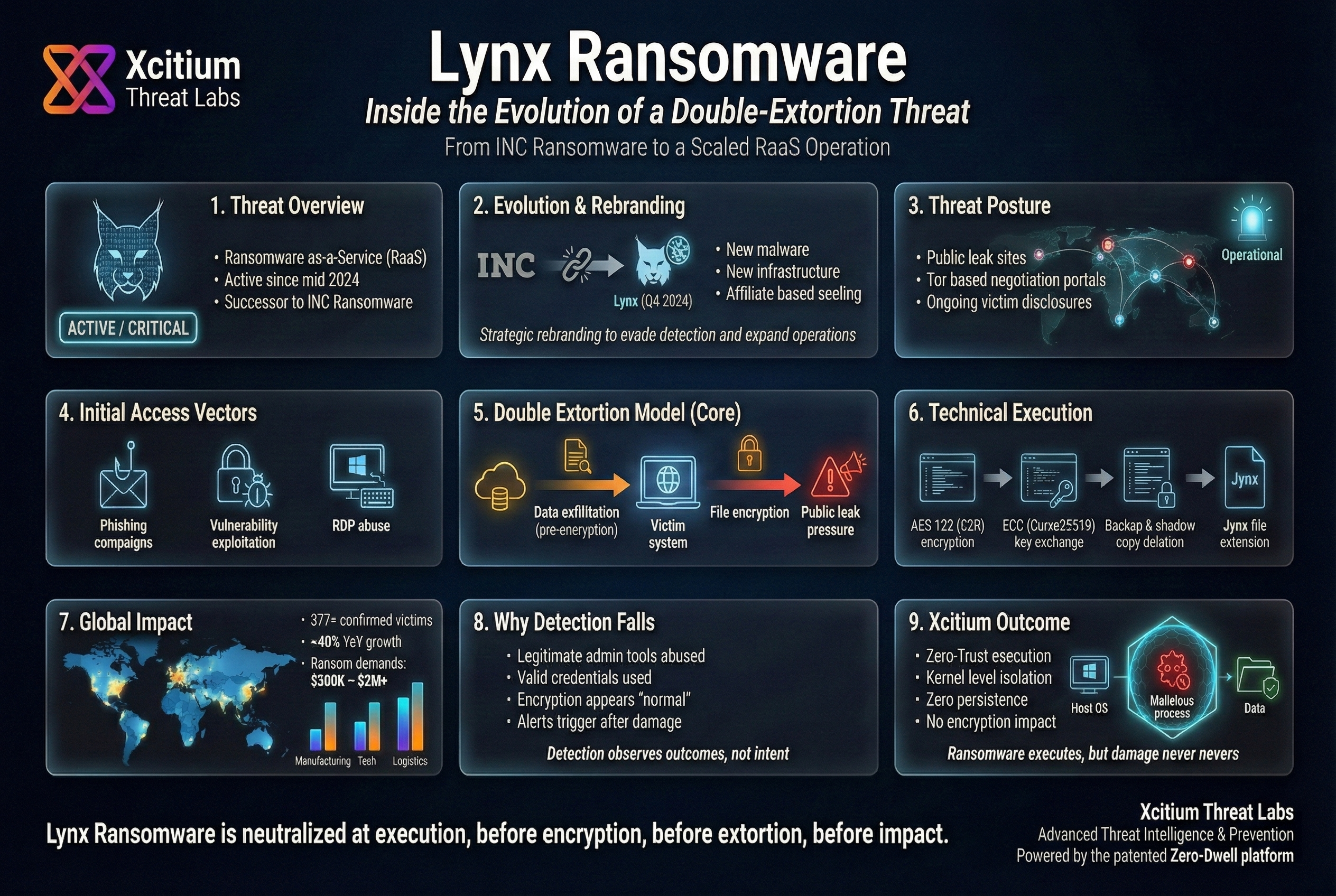
Lynx is a relatively new Ransomware-as-a-Service (RaaS) identified in July 2024. It seems to be the successor to the “INC” ransomware, and it has a complex encryption algorithm with a public leak site, and it seems to have launched with ethical guidelines in July 2024, excluding hospitals, non-profit, and government targets.
In reality, the operations of Lynx follow the conventional double extortion framework, which steals data and locks files. The victims receive a README. txt with links for negotiations via Tor, and the leaked data is released if a ransom is not paid. Lynx has been growing rapidly owing to its business model based on affiliates.
As of 2026, Lynx has established itself as one of the RaaS operations that have been spreading rapidly and have been scaling with a rising number of affiliates. Additionally, it has been attacking on a large scale due to its ability to use effective attack infrastructure.
The Evolution: From INC to Lynx A Strategic Rebranding
INC Ransomware to Lynx saw more than just rebranding. It was a tactical measure to enhance operations while avoiding being detected. INC Ransomware had been actively operating since at least 2021. The actors rebranded as Lynx in October 2024 used new malware, ransom notes, as well as infrastructure. There was a tactical objective to enhance TTP set by INC.
Lynx Operations 2026
Strategic Data Manipulation Framework
Active locking of operational data using AES-128 algorithms.
Pre-encryption data theft to leverage public leak threats.
• Vulnerability Research
• RDP Exploitation
• Mimikatz Auth Theft
• Privilege Escalation
• Affiliate Management
• Tor Infrastructure
Double Extortion: The Core Evil of Lynx Attacks
Lynx Ransomware has been noticed to be using the Ransomware-as-a-Service (RaaS) business model that enables affiliates to distribute its malware. Its major target is double extortion attacks that involve stealing valuable data as well as encrypting files owned by the victim. If the payment is not made, the stolen data is liable to be published on the internet.
Furthermore, this technique maximizes the impact on organizations, putting them in a tight spot where both data access and data privacy are in jeopardy.
The group uses various advanced TTPs in order to reach its goals. Initial access might include:
- Phishing campaigns: These are deceptive emails that try to trick workers to reveal their credentials or install malicious software.
- Exploiting vulnerabilities: Targeting unpatched software or system weaknesses.
- Compromised Remote Desktop Protocol (RDP) sessions: Gaining unauthorized access via inadequately secured RDP sessions.
Upon entering the network, the operators of the Lantern Bird malware rely on tools such as Cobalt Strike and Mimikatz for lateral movement and privilege escalation. Carefully exfiltrating the sensitive data prior to the encryption payload deployment ensures that the attackers gain the greatest leverage over their victims as a result.
Lynx Intelligence Report 2026
Real-time Intelligence: Geographic & Industrial Analysis
🌐 Geographic Hotspots
Targeted Industries and Regions
Lynx has targeted many sectors, including businesses that deal with valuable data and are capable of paying the ransom. The manufacturing sector has the highest number of affected businesses, followed by the business services sector, technology sector, and transportation/logistics sector.
Also affected are businesses that deal with sectors such as agriculture, energy, finance, and healthcare. The sectors affected geographically include both North America and Europe. For instance, by late 2025:
- Countries: The United States leads in these incidents with well over 150 victims; the UK, Canada, Germany, and Australia also appear regularly. More incidents have been reported in the Asia/Pacific and other countries.
- Examples: Recent victims include a U.S. railroad company, a Japanese creative firm, and a European machinery business. High profile victims include the Hartford French retail company January 2026.
Such patterns illustrate that Lynx tends to target mature markets, industries, or sectors that are considered essential to operations and possess vast amounts of data. In a sense, a professional assessment states that Lynx “does not target” the healthcare or government sector, yet it was seen that many companies participating in the financial sector have already been attacked. It appears that the “ethical” exemption excludes very few domains.
Analyzing the Numbers: Statistics Behind Lynx Ransomware Attacks
- Lynx Ransomware is an active and growing threat, with a rapidly expanding victim base.
- ~377 confirmed victims have been publicly attributed to Lynx so far the real number is likely much higher due to undisclosed incidents.
- Attack activity increased by ~40% in the past year, showing a sharp escalation in operations.
- Ransom demands typically range from $500,000 to over $2 million USD, depending on victim size and data sensitivity.
- High-value organizations are the primary targets, maximizing financial returns for the group.
- Strong financial incentives are driving Lynx’s continued evolution and persistence in attacking vulnerable enterprises.
Technical Execution Flow
Automated Post-Compromise Procedures
How Lynx Ransomware Operates
It uses strong encryption and various methods to maximize damage. Like most advanced strains, it uses a hybrid encryption algorithm, which involves AES-128 in Counter mode with ECC (curve25519) for key exchange. It appends ‘.lynx’ to the name of each encrypted file. Threat actors usually launch the ‘Lynx’ ransomware using command-line arguments for customized attacks (selecting target files and directories, encryption modes, and much more). Some of its key features include:
- Process & Service Termination: Lynx forcefully terminates the processes and services that can act as an obstacle for the encryption process or data stealing. It focuses on the backup and database tools with keywords like SQL, Veeam, Exchange, Java, and many more. It identifies the process or service with these words and terminates them forcibly.
- Shadow Copy and Backup Removal: This malware removes the Windows Volume Shadow Copies and the backup partition. It will delete the Recycle Bin and destroy the local backup snapshots.
- Selective Encryption: The lynx encrypts files of the users (doc, database, code files) without encrypting the important system directories (e.g., “Windows,” “Program Files”), executables (.exe, .dll). It can also encrypt the hidden drives, network shares to cause maximum destruction.
- Ransom Note Delivery: Once the encryption process is complete, the malware releases a ransom note with the title “README.txt” in each of the compromised folders and may also change the desktop background to display payment details. This note leads the victim to a Tor-based negotiation service with a unique id assigned to them. Some variants include features that automatically print the ransom note through OneNote so that unattended printers are also targeted.
Such processes are usually handled by the ransomware. In addition, by incorporating the Windows Restart Manager, the Lynx malware can also encrypt any file that is running. The overall effect is that infected computers lock all their data with new files replacing the originals, which were saved as files with the “.lynx” format.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique | Description |
|---|---|---|
| Initial Access (TA0001) | T1133 T1078 |
External Remote Services: Adversaries gain access by abusing exposed services like RDP using brute-force or stolen credentials. Valid Accounts: Attackers use stolen or compromised credentials to access systems and networks. |
| Execution (TA0002) | T1059.001 T1059.003 |
PowerShell: Attackers run malicious commands and scripts through PowerShell. Windows Command Shell: Adversaries use cmd.exe to execute commands, scripts, or binaries on target systems. |
| Persistence (TA0003) | T1543.003 T1136.002 |
Windows Service: Attackers create or modify services to gain persistence and run malicious code at startup. Domain Account: Threat actors create or compromise domain accounts to maintain access in Active Directory. |
| Privilege Escalation (TA0004) | T1098.007 | Additional Local or Domain Groups: Adversaries add compromised accounts to privileged local or domain groups to elevate their access rights within the network. |
| Defense Evasion (TA0005) | T1078 | Valid Accounts: By using legitimate credentials, attackers can bypass security controls that might detect unauthorized access attempts. |
| Credential Access (TA0006) | T1003 | OS Credential Dumping: Adversaries attempt to steal credentials, such as hashes or plaintext passwords, from the operating system’s memory or storage, often using tools like Mimikatz. |
| Discovery (TA0007) | T1046 T1135 T1018 T1082 T1016 T1012 T1087.001 |
System & Network Discovery: Attackers scan ports, enumerate network shares, identify remote systems, and collect system and network configuration details. Query Registry: Adversaries query the Windows Registry to gather system and software information. Local Account: Threat actors enumerate local user accounts to support credential theft or privilege escalation. |
| Lateral Movement (TA0008) | T1021.001 | Remote Desktop Protocol: Adversaries use RDP to move between systems within a network, often leveraging compromised credentials to gain access. |
| Collection (TA0009) | T1560.001 | Archive via Utility: Attackers use legitimate archiving utilities, such as 7-Zip, to compress collected data before exfiltration. |
| Command and Control (TA0011) | T1219 | Remote Access Software: Adversaries utilize remote access software to maintain persistent control over compromised systems and execute commands remotely. |
| Exfiltration (TA0010) | T1567 | Exfiltration Over Web Service: Threat actors transfer stolen data out of the compromised network using web services, often to temporary file-sharing sites. |
| Impact (TA0040) | T1486 T1490 |
Data Encrypted for Impact: Adversaries encrypt data to make systems unusable and force ransom payment. Inhibit System Recovery: Attackers remove or disable backups to prevent recovery without paying. |
Case Study: Xcitium vs. Lynx Ransomware
This demonstration illustrates how Xcitium defends systems against ransomware in real time. 60 Lynx ransomware samples are executed to replicate a large-scale, real-world attack scenario. Rather than depending on signatures or cloud-based detection, Xcitium’s Zero-Dwell technology automatically flags every untrusted process and places it into isolation the moment it appears.
Because of this, Lynx cannot begin encrypting files, create persistence, or reach its command-and-control servers. Even brand-new, never-seen variants are isolated before any damage can occur.
By removing the exposure window entirely, Xcitium delivers continuous protection, ensuring systems remain operational and data stays secure. This video shows how advanced threats like Lynx ransomware are stopped instantly through Xcitium’s proactive, prevention-first security model.
Indicators of Compromise (IOCs)
Network Indicators (Domains, IPs)
- Public domains: The group runs a publicly accessible leak/blog site at lynxblog[.]net. (This domain hosts stolen data and ransom-related announcements.)
- Tor C2/leak URLs: Numerous Tor
.onionaddresses have been used for victim communications. Notable examples include the Lynx chat negotiation portals (lynxchatly4z…onion,lynxchatfw4r…onion,lynxchatohm…onion), and Lynx data-leak sites (lynxblogco7r…onion,lynxblogijy4j…onion,lynxblogmx3rb…onion,lynxblogtwatf…onion, etc.). These .onion URLs appear in ransom notes and on Tor sites. (All “lynxchat…” and “lynxblog…” .onion addresses should be treated as malicious infrastructure.) - IP addresses: In at least one incident, threat actors connected via RDP from Internet IPs which can serve as IOCs. For example, it observed 195.211.190.189 (initial RDP) and 77.90.153.30 (subsequent RDP) during a Lynx deployment. Monitoring for unusual RDP connections from external IPs may detect activity.
File Hashes
- SHA-256: Multiple Lynx ransomware binaries have been identified. Representative examples include
31de5a766dca4eaae7b69f807ec06ae14d2ac48100e06a30e17cc9acccfd5193,571f5de9dd0d509ed7e5242b9b7473c2b2cbb36ba64d38b32122a0a337d6cf8b,589ff3a5741336fa7c98dbcef4e8aecea347ea0f349b9949c6a5f6cd9d821a23,eaa0e773eb593b0046452f420b6db8a47178c09e6db0fa68f6a2d42c3f48e3bc, etc.. These hashes come from observed Windows samples of Lynx. - MD5: Lynx samples also appear under various MD5 hashes. For example, following MD5s such as
b1d81e8bbecccc547645d17395538a2dand30656c737338818bee8cc3591e3f3dccamong others.
Lynx Ransomware SHA-1 Samples & Zero‑Dwell Threat Intelligence Reports
Conclusion: Double Extortion Is the New Baseline
Lynx ransomware represents the next phase of professionalized extortion. This is not opportunistic malware. It is a mature RaaS operation built to steal data, encrypt systems, destroy backups, and apply pressure through public leak sites. With hundreds of confirmed victims and rapidly increasing activity, Lynx shows how fast modern ransomware groups can scale once initial access is achieved.
Why This Threat Puts Every Organization at Risk
Lynx succeeds because it exploits common operational gaps that still exist across enterprises:
- Phishing, exposed RDP, and unpatched services provide reliable entry points
- Stolen credentials allow attackers to blend in as valid users
- Backup and database services are terminated before encryption begins
- Data is exfiltrated first, making recovery alone insufficient
- Detection-based tools react only after damage is already underway
Once execution is allowed, the outcome becomes a race the defender cannot win.
Where Xcitium Changes the Outcome
For organizations using Xcitium Advanced EDR, Lynx attacks fail at execution.
- Untrusted ransomware processes are isolated immediately
- Encryption routines cannot touch real files or network shares
- Data exfiltration attempts are blocked before transfer begins
- Lateral movement and persistence never establish
- Code can run without being able to cause damage to the real system
By eliminating dwell time entirely, Xcitium removes the attacker’s leverage from the first moment of execution.
Stop Ransomware Before Extortion Begins
Ransomware groups like Lynx rely on speed, automation, and delayed detection. Prevention must operate faster than the attack chain.
Protect your endpoints.
Protect your data.
Choose Xcitium Advanced EDR, powered by the patented Zero-Dwell platform.




