
NanoRemote is a Windows backdoor that uses Google Drive as a covert command-and-control channel, allowing attackers to steal data and control systems.
Recent findings by researchers in the field of cybersecurity detail a complex Windows backdoor, known as NanoRemote, that utilizes the Google Drive API in order to perform stealthy C2 communications. This type of complex malware will allow those behind the attack to exfiltrate information, as well as spread further malware through the utilization of Google’s cloud storage service in order to conceal malicious communications among normal network traffic.
Abusing Google Drive for Stealthy C2
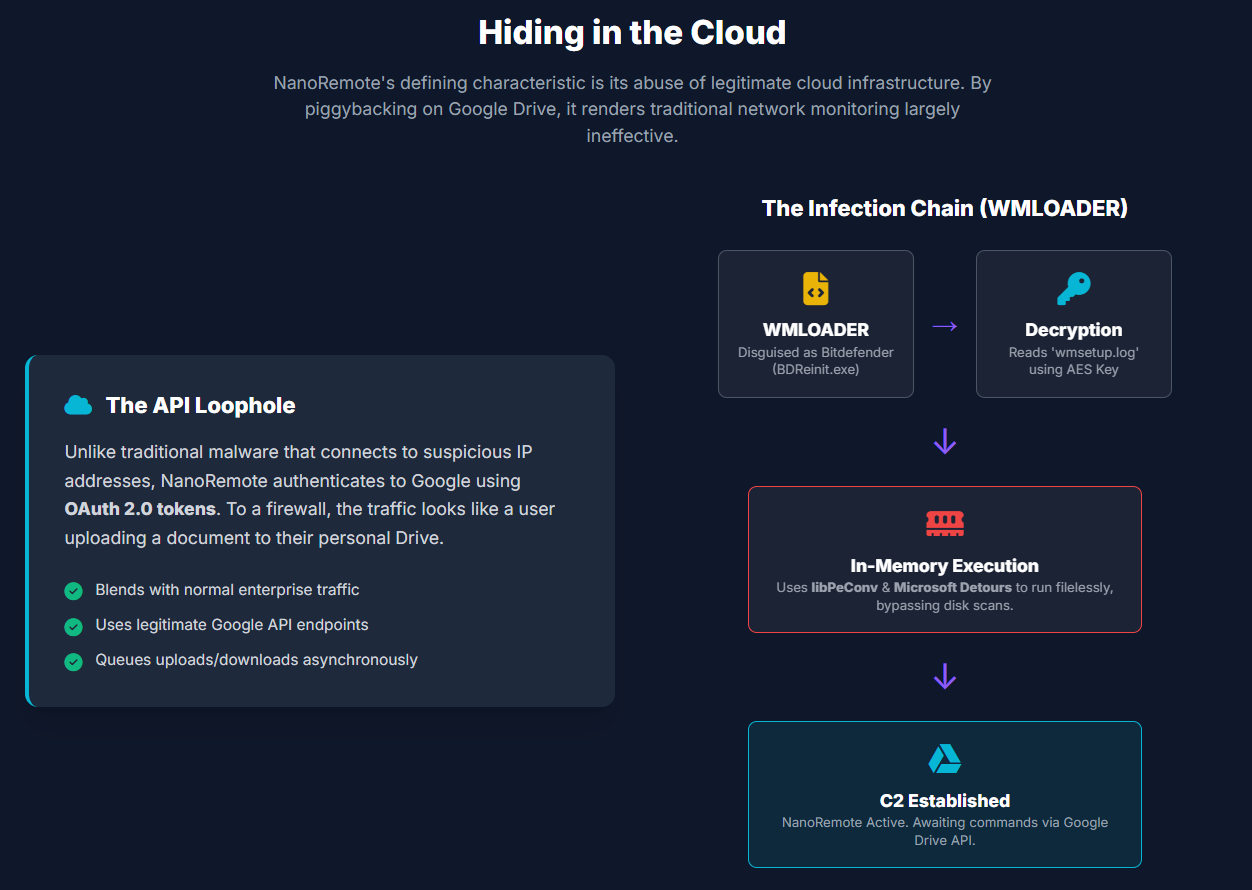
Another important aspect of NanoRemote is the use of Google Drive as the channel for C2 communication. NanoRemote malware communicates with Google through OAuth 2.0 tokens, making the data transfer a legitimate Google Drive API communication. This means that such data transfer may not be detected by typical network monitoring systems, as it is akin to usual operations performed by organizations in the cloud.
Moreover, this specific case is representative of the larger trend in which threat actors abuse cloud applications for the purpose of evasion. For example, the DarkHydrus APT group’s trojan, named RogueRobin, was observed utilizing Google Drive for its C2 component in campaigns that took place in the past. Using legitimate applications like Google Drive allows the threat actor to remain undetected while conducting espionage.
Why Cloud-Based C2 Is So Hard to Detect
- Uses trusted cloud services like Google Drive that are commonly whitelisted
- Communicates via legitimate APIs, blending into normal cloud activity
- Relies on OAuth tokens, making access appear authorized
- Uses HTTPS/TLS encryption, limiting traffic inspection
- Hides within high volumes of cloud traffic
- Avoids blocking due to shared and dynamic cloud infrastructure
- Shifts detection from network controls to endpoint-based monitoring
Feature-Rich Backdoor Capabilities
- Fully featured backdoor with post-compromise capabilities.
- Built with C++ as a 64-bit Windows executable.
- Supports handling 22 different commands.
- Allows attackers almost limitless access and control over compromised machines.
- Facilitates Reconnaissance, File manipulation, and Arbitrary Command Execution.
- Also has a task manager for file transfer operations.
- Support multiple upload/download jobs in the same queue.
- Facilitates pausing and resuming of file transfer operations.
- Able to Refresh Cloud Connectivity with a New Access Token.
- Communicates With Operators Over HTTP.
- “C2 traffic is compressed and AES encrypted.”
- Has a custom User-Agent string (“NanoRemote/1.
- It relies on a particular API path to handle command and control communication.
- Utilizes a double-channel C2 structure.
- Combines functionality of the Google Drive API with standard HTTP POST Requests.
- Supports stealthy data exfiltration or payload extraction.
- Capable of avoiding traditional network-based filtering tools.
NanoRemote Key Capabilities
Disguised as Bitdefender: NanoRemote Delivery & Evasion
- The initial infection vector of NanoRemote is still unknown, but observed activity starts with a custom loader named WMLOADER.
- WMLOADER disguises itself as a legitimate Bitdefender component (BDReinit.exe) using an invalid digital signature.
- The loader decrypts an encrypted payload from wmsetup.log using a secret AES key and executes NanoRemote directly in memory.
- By impersonating trusted security software and operating filelessly, the malware minimizes disk artifacts and evades antivirus detection.
- NanoRemote leverages open-source tools such as Microsoft Detours for API hooking and libPeConv for memory-based execution.
- These techniques allow the malware to bypass standard Windows loading mechanisms and remain stealthy, complicating forensic analysis and remediation.
Threat Actor Attribution and Connections
Interestingly, a great degree of code-sharing has been found to exist within NanoRemote and another antecedent malware backdoor named Finaldraft (also referred to as Squidoor). Like NanoRemote, Finaldraft also utilized another cloud interface the Microsoft Graph API for C2 communication and has also been linked to the same threat actor behind NanoRemote. In fact, both NanoRemote and Finaldraft were found to use the same encryption key and also other distinct signs left behind by their developers, leaving little doubt that both belong to the same threat actor toolkit. Furthermore, both backdoors have been linked to a threat community with the name REF7707.
This cluster is believed to have originated from China and has been operational since 2023 and is known to target government, military, and telecommunications, education, and aviation-related entities in the Southeast Asia and South America regions. It has also been associated with the 2025 intrusion into a Russian information-technology services provider, proving the extent of its spy-related activities to have a truly global impact. Lastly, the discovery of NanoRemote also proves that the REF7707 threat actor is constantly developing its tactics by using the trusted cloud platform, making it a potent challenge for the enterprise security team.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique | Procedure |
|---|---|---|
| Discovery | T1087 | Account Discovery: Retrieves the current username and evaluates administrative privileges to determine user access level. |
| Discovery | T1680 | Local Storage Discovery: Enumerates local drives and collects disk type, free space, and total capacity information. |
| Discovery | T1083 | File and Directory Discovery: Lists files and directories by path to identify and navigate sensitive data locations. |
| Discovery | T1016 | System Network Configuration Discovery: Collects network interface details, including internal and external IP addresses. |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell: Executes arbitrary commands via cmd.exe and returns output to the operator. |
| Defense Evasion | T1036.001 | Masquerading: Invalid Code Signature: Disguises itself as a legitimate Bitdefender component using a deceptive filename and invalid digital signature. |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols: Uses HTTPS and the Google Drive API for encrypted command-and-control communication. |
| Command and Control | T1105 | Ingress Tool Transfer: Downloads additional tools or payloads from attacker-controlled cloud storage. |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Cloud Storage: Uploads stolen data to Google Drive to blend with legitimate cloud traffic. |
Case Study: Xcitium vs. WMLoader
Modern cyber threats no longer rely on known signatures or predictable behaviors. That’s why effective protection must start at the core of the operating system. Xcitium takes a fundamentally different approach by enforcing security directly at the kernel level, where malicious activity can be controlled before it ever reaches critical system resources.
Instead of attempting to detect threats after execution, Xcitium automatically isolates unknown and untrusted files, allowing them to run only within a secure, virtualized environment. This prevents malware from making system-level changes, establishing persistence, or communicating externally without disrupting user productivity or business operations. Known applications continue to operate normally, while unknown processes are safely isolated by default.
By eliminating dependence on signatures, cloud lookups, and delayed behavioral analysis, Xcitium delivers immediate protection against zero-day attacks and advanced malware. The result is a true Zero Trust execution model that provides continuous protection, operational visibility, and peace of mind all without performance penalties, alerts fatigue, or compromise.
Conclusion: When Trusted Cloud Services Become Silent Control Channels
NanoRemote highlights a growing shift in modern cyber espionage. Attackers no longer rely on noisy infrastructure or suspicious domains. They hide in plain sight, using trusted cloud platforms like Google Drive to blend command and control traffic into everyday business activity. By abusing legitimate APIs and OAuth authentication, NanoRemote turns routine cloud communication into a covert control plane.
When malware traffic looks identical to normal cloud usage, network defenses lose visibility fast.
Why NanoRemote Is So Difficult to Detect
NanoRemote succeeds because it exploits assumptions many environments still make:
- Cloud services are implicitly trusted and widely whitelisted
- OAuth based access appears authorized and legitimate
- HTTPS encrypted traffic limits inspection
- Fileless execution leaves minimal forensic artifacts
- Malware masquerades as trusted security software
- Endpoint execution happens before alerts are raised
Once NanoRemote is active, attackers gain persistent control, stealthy data exfiltration, and the ability to deploy additional payloads without drawing attention.
How Xcitium Stops NanoRemote Before Control Is Established
With Xcitium Advanced EDR, the attack chain is broken at execution.
- Malicious loaders impersonating trusted software are blocked immediately
- Fileless payloads executed in memory fail to run
- API hooking and reflective loading attempts are stopped
- Backdoor processes never establish command and control
- Data exfiltration through cloud services never begins
By enforcing execution control at the endpoint, Xcitium prevents cloud based C2 abuse from ever becoming operational.
Cloud Abuse Requires Endpoint Control
NanoRemote proves that attackers will continue to weaponize trusted platforms to evade detection. Defending against this strategy requires stopping unknown code at the moment it executes, not chasing malicious traffic after it blends into the cloud.
Protect your endpoints against stealthy backdoors and cloud based command and control.
Choose Xcitium Advanced EDR, powered by the patented Zero-Dwell platform.



