A New Ransomware Gang on the Rise
NightSpire surfaced in early 2025 as a financially motivated cyberextortion group. At first the group focused on stealing sensitive data and demanding payment without encryption, but it soon adopted a full double-extortion model.
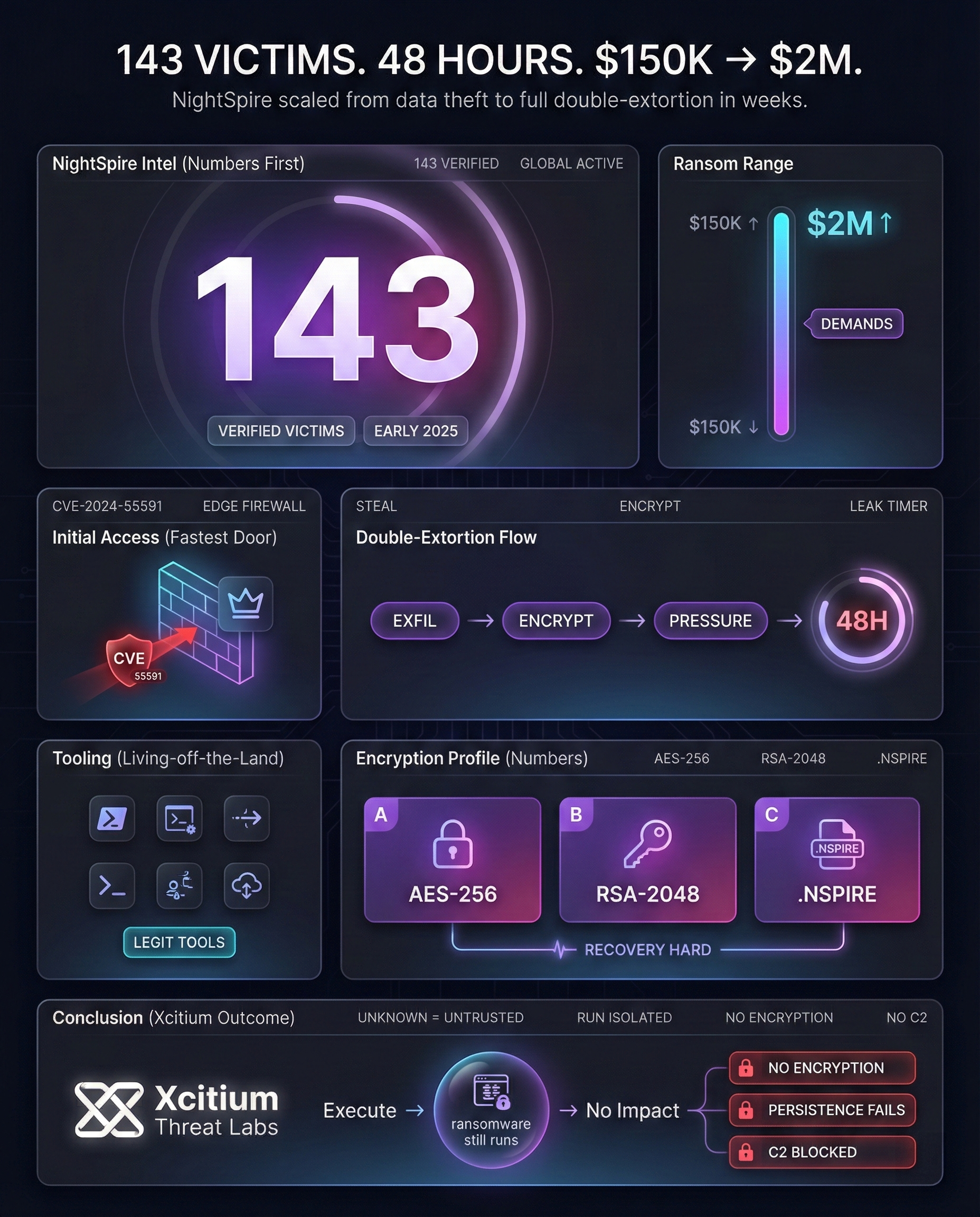
Within weeks of launching its Tor data-leak site (March 2025), NightSpire began encrypting victims’ files while continuing to threaten public disclosure of stolen data. Reported ransom demands have ranged from roughly $150,000 up to $2 million, reflecting a rapid capability expansion.
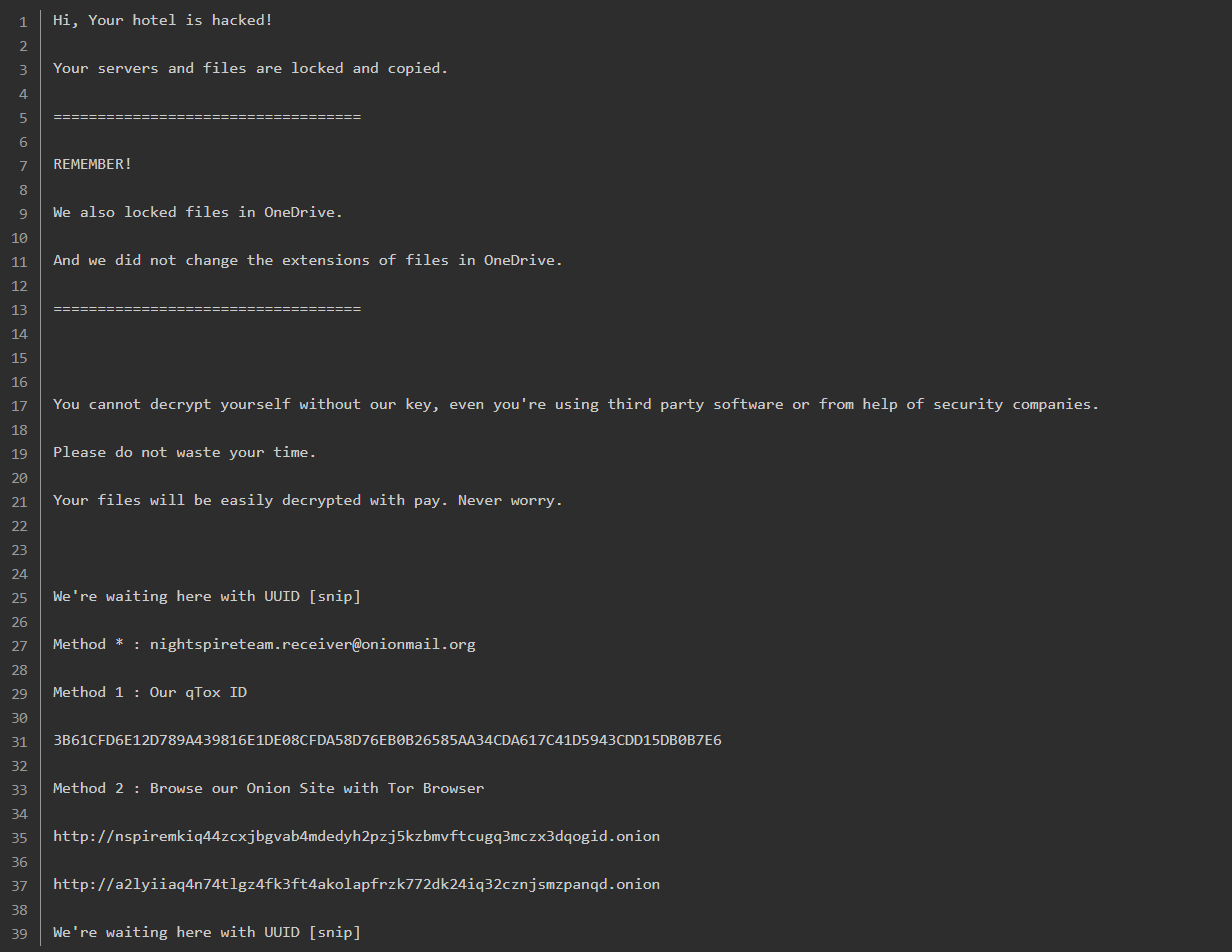
Unlike more polished ransomware syndicates, NightSpire’s operators have shown amateurish tradecraft for example, they even used a Gmail address (instead of an anonymous account) to communicate with victims. In short, this is a newly formed group with broad goals: steal data, encrypt it, and pressure victims to pay.
Origins and Evolution of NightSpire
It started with stealing data and shifted its focus to encrypting files in April 2025. In just a matter of weeks, the group started encrypting files using AES-256/RSA-2048 and exploited the critical Fortinet firewall vulnerability CVE-2024-55591 as its primary point of access. This allows attackers without authentication to acquire super-admin privileges on FortiGate devices.
The rapid change from data extortion to encryption in just under a month is unusual for malware like NightSpire.
As the malware group continued to grow in popularity and notoriety, they continued to evolve and improve their tools and methods. Their methods are almost entirely based on legitimate tools instead of malware, such as using WinSCP and MEGAcmd for exfiltrating stolen data and PowerShell, PsExec, and WMI for moving laterally.
It is also interesting to note that unlike other malware of this kind, NightSpire does not delete volume shadow copies on infected Windows systems and instead relies on rapid encryption of files rather than deleting shadow copies.
The leak site also features countdown timers and has a ‘name and shame’ page that features non-paying victims of the malware and sometimes even offers free downloads of stolen data once the deadline expires.
Targeted Industries and Sectors
Unlike some ransomware gangs that specialize by sector, NightSpire operates opportunistically across many industries. In fact, security trackers report breaches in everything from small tech firms to hospitals and manufacturers. For example, analysis of dozens of victims finds the most common targets include:
- Technology and IT Services: Several small software and IT companies have been hit.
- Manufacturing: Over a third of identified victims are in manufacturing (e.g. industrial firms).
- Financial and Insurance: Banks, finance and insurance firms appear on NightSpire’s victim lists.
- Healthcare: Hospitals and medical research groups have been breached.
- Consumer Services: Retailers and logistics companies (and even a hotel chain breach) are among targets.
- Government / Construction / Education: A few public agencies, construction companies, and schools are also reported victims.
In other words, NightSpire has no strong vertical preference it simply goes after organizations with exposed systems. Most of these victims are small or mid-size businesses (often under 1,000 employees). This “soft target” focus makes sense: smaller companies often lack robust security, making them easier to compromise.
Geographical Spread and Recent Incidents
Nightspire Intel
Recent Confirmed Operations
| Target Entity | Actor | Timeline |
|---|---|---|
| Wilson Workflow Solutions Global Operations | Nightspire |
Disc: 2026-02-17 Est: 2026-02-01 |
| *m**i**n ***i*g & *o**e* Co Natural Resources | Nightspire |
Disc: 2026-02-16 Est: 2026-02-14 |
| *e**a*c, F**t**i, *il**o Industrial Services | Nightspire |
Disc: 2026-02-14 Est: 2026-01-17 |
| *F* *a**e G**H & Co. *G European Manufacturing | Nightspire |
Disc: 2026-02-14 Est: 2026-02-02 |
By late 2025 the group had claimed roughly 143 victims worldwide. In terms of geography, the United States has seen the most incidents, accounting for about 28 known victims. Close behind is India (10 victims), and East Asia also ranks high: Hong Kong (~8 victims), Taiwan (~7 victims) and Japan (~6 victims) are significant targets.
Other countries with reported NightSpire breaches include Egypt, Mexico, Nigeria, South Africa, Peru, Vietnam and several in Europe. This wide spread North America, Asia-Pacific, Africa, Latin America and Europe shows that NightSpire attacks are driven by opportunity rather than politics.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
Nightspire TTPs
Before encrypting, NightSpire steals data to use in extortion. It exfiltrates files using known utilities (e.g. WinSCP, MEGAcmd, Rclone) to attacker servers.
This stolen data is used to pressure victims: on the leak site they are given short deadlines (sometimes 48 hours) to pay or see data published.
Case Study: Xcitium vs. Nightspire Ransomware
This demonstration highlights how Xcitium protects endpoints from ransomware attacks using a prevention-first security model. In this test, 12 live Nightspire ransomware samples are executed in a controlled environment to simulate a realistic, multi-variant attack scenario.
Instead of relying on signatures, reputation checks, or reactive detection methods, Xcitium’s ZeroDwell isolation technology automatically classifies each Nightspire sample as untrusted at the moment of execution and runs it inside a secure containment environment.
As a result, Nightspire is unable to complete its attack lifecycle. File encryption attempts are confined, persistence mechanisms fail to impact the host, and command-and-control communication does not succeed even though the ransomware samples are fully operational.
By eliminating the exposure window entirely, Xcitium keeps the endpoint fully functional and uncompromised. This video demonstrates how modern ransomware families like Nightspire are neutralized instantly through continuous zero-trust execution and real-time isolation.
Indicators of Compromise (IOCs)
- Contact emails:
night.spire.team@gmail.com,night.spire.team@proton.me, andnight.spire.team@onionmail.org. The group also maintains a Telegram channel (t.me/night_spire_team) for negotiation and publication of leaks. - Leak-site URLs (Tor):
nspireyzmvapgiwgtuoznlafqvlyz7ey6himtgn5bdvdcowfyto3yryd.oniona2lyiiaq4n74tlgz4fk3ft4akolapfrzk772dk24iq32cznjsmzpanqd.onion.
These sites contain information about the victims, stolen data, and sometimes a countdown timer. - File markers: The encrypted files are marked with the extension ‘
.nspire.’ On the victim’s computer, ransomware infection leaves default ransom notes like ‘readme.txt,’ ‘readme_2.txt,’ or ‘nightspire_readme.txt.’ - Infrastructure: The IP address 14.139.185.60 was associated with the WinSCP data server of the NightSpire group. Hostnames like
XDRAGON-SERVER1andWINDOWS-DTX-8GBare known to be associated with the NightSpire group’s computers. Even the operator’s handle ‘xdragon128’ was embedded in a hostname on their network during one of their operations. - Tools and files: NightSpire activity involves common utilities: e.g. Windows binaries like
WinSCP-6.3.7-Setup.exe,7z2408-x64.exe,Everything.exe, and legitimate FTP and compression tools. Logs of these appearing on a server can be red flags. (Note: hashes for some of these files have also been published by security teams.)
Nightspire Ransomware SHA-1 Samples & Zero‑Dwell Threat Intelligence Reports
Conclusion: NightSpire Shows How Fast “New” Ransomware Becomes Real
NightSpire is not a legacy syndicate, it surfaced in early 2025 and escalated fast. Within weeks of launching its Tor leak site in March 2025, it shifted into full double extortion and began encrypting victims in April, with reported demands ranging from roughly $150,000 to $2 million.
Why This Threat Hits So Many Organizations
NightSpire succeeds by taking the shortest path to business impact:
- Initial access via exposed infrastructure, including exploitation of CVE-2024-55591 on Fortinet devices
- Heavy use of built-in tools for execution and spread, including PowerShell, PsExec, and WMI
- Data theft first, then encryption pressure using common utilities like WinSCP, MEGAcmd, and Rclone
- Opportunistic targeting across sectors, with 143 claimed victims worldwide, led by the United States
Where Xcitium Changes the Outcome
For organizations using Xcitium Advanced EDR, NightSpire loses the moment it tries to run.
- Unknown ransomware samples are isolated at execution
- Encryption attempts run, but code can run without being able to cause damage
- Persistence and command activity fail to impact the host
- The endpoint stays usable, even under multi-variant execution tests
Stop ransomware before it can encrypt, steal, and extort.