Cybercriminals have launched a sophisticated phishing campaign themed around Pride, targeting employees of organizations. The phishing campaign, which has been launched in two phases (Dec 2025 & Jan 2026), has targeted thousands of organizations worldwide.
What’s interesting to note is that the losses have been substantial for organizations in the US and the UK, with various sectors, including finance, tech, and retail, being targeted. The diversity-themed phishing campaign is a clear example of how cybercriminals use social values for their illicit purposes.
Attackers leverage compromised SendGrid accounts to bypass spam filters. They target HR/Internal comms personas to increase trust.
Exploiting Pride Month themes, attackers use “Opt-out” choices. This creates a false sense of control while redirecting to malicious infrastructure.
A CAPTCHA layer prevents automated sandbox analysis from scanning the final phishing page, ensuring only humans see the login portal.
The final destination is a cloned corporate SSO page. This wave has heavily impacted IT, SaaS, and financial sectors globally.
Once credentials are stolen, attackers access sensitive internal systems. Mimecast reports heavy volume in UK and US organizations.
We are updating corporate email signatures. Click to preview the new Pride Month decorations.
Learn MoreIf you wish to opt-out of the mandatory branding update, please confirm your choice below.
Confirm Opt-Out> Target confirmed: UK_RETAIL_SECTOR
> Credential bypass complete…
> Session cookie: [CACHED]
> LATERAL MOVEMENT: ACTIVE
> ACCESS GRANTED: INTERNAL_DOCS
Pride-Month Scam: How the Campaign Works
It has been observed that the attackers sent emails to the employees, informing them of a plan by the company to include Pride-themed email decorations. Each email contained a link for “opt out” for employees who did not wish to have this new header/footer added.
However, this link actually leads to a false login page, meant for password theft. This is a social engineering attack, as it will deceive employees who wish to support Pride events as well as those who do not wish to support it, as clicking on “opt out” will still lead to the false login link.
The attackers have, of late, upgraded their attack by adding persona-based subjects, as well as requiring a CAPTCHA to be entered before redirecting the employees to the false login pages.
The key aspects of this phishing attack include:
- Social-engineering hook: The attackers sent out emails informing employees of a plan by the company to include Pride-themed email decorations, with a link for “opt out” for employees who did not wish to have this added.
- Scale via trusted channels: The attackers sent out these emails using legitimate email delivery services, which enabled them to bypass filters.
- Multi-stage lure: When the link is clicked, it leads to a CAPTCHA, which is required to be entered before the false login site is opened.
- Realistic: In wave 2 the team appended plausible sender names to boost credibility.
Together these tactics made the scam unusually convincing and difficult to spot.
Scope and Impact of the Campaign
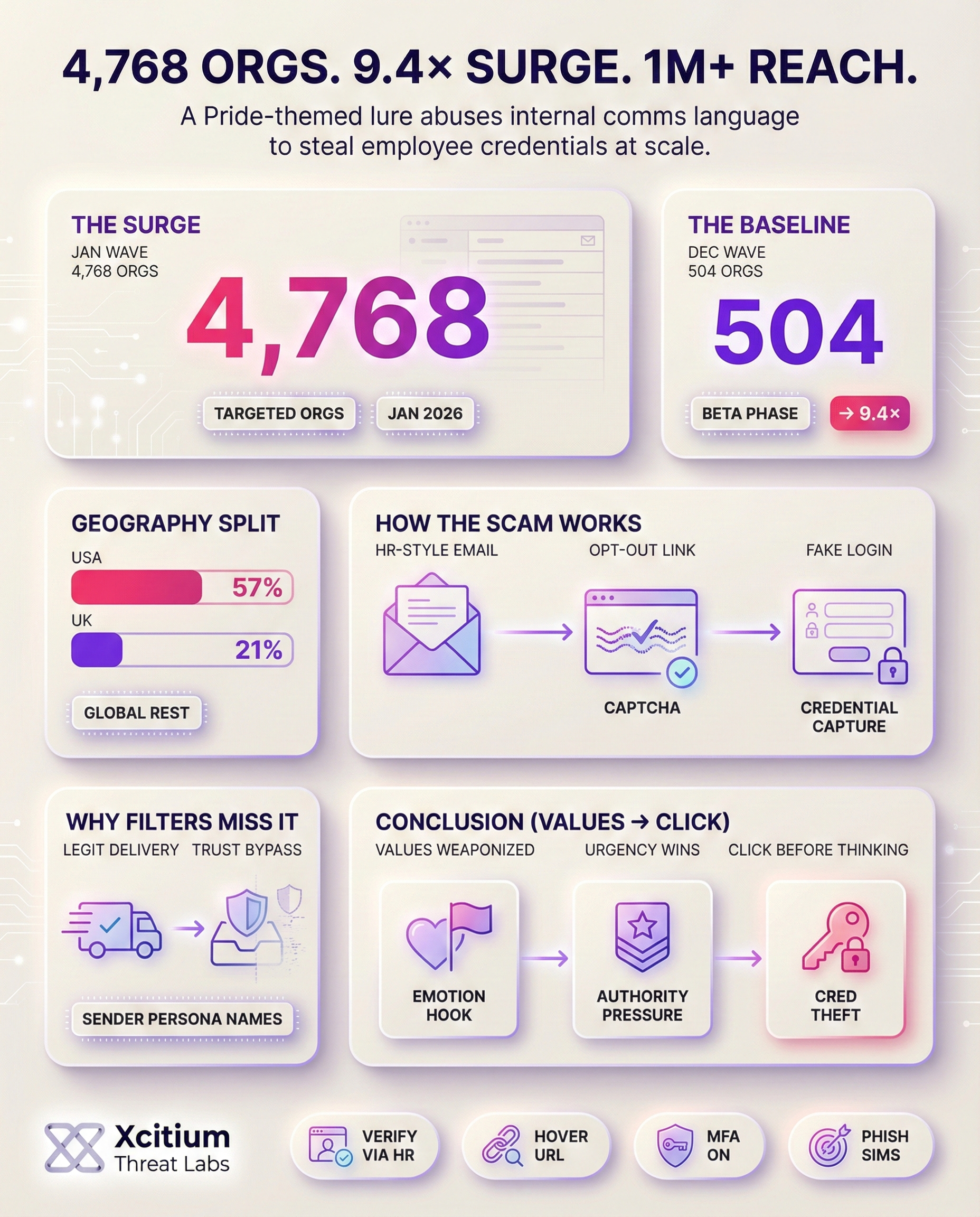
This phishing attack was also unusually large in scale. In the first wave of the attack, which occurred in Dec 2025, around 504 organizations were targeted (approximately 62% from the US and 20% from the UK).
A month later, nearly 4,768 organizations received similar emails. The sectors targeted in the initial attack included financial services and consulting, but the sectors targeted in the second attack included IT, SaaS, retail, and more.
It has also been mentioned that around 57% of the targeted organizations were from the US, followed by another 21% from the UK, and the remainder from other countries such as Germany, Australia, South Africa, Canada, and more.
The scale of the attack also implies that the attackers were constantly refining their attack strategy and list of targets, as the number of targets increased more than 9 times in the second attack compared to the first attack.
Phishing Surge Report
// INTEL: DEC 2025 – JAN 2026
-
USA57%
-
UK21%
Why Diversity-Themed Scams Are Effective
- Attackers deliberately exploit social causes like Pride Month and Diversity initiatives to trigger emotions and bypass normal skepticism.
- These themes align with genuine organizational values, making the messages appear legitimate and trustworthy.
- Employees who support these values may eagerly engage with the message.
- Employees who are skeptical or resistant may still click to opt out or react negatively.
- In both cases, the attacker wins the message captures attention and drives a click before critical thinking kicks in.
- The campaign framed the change as “per management direction,” adding pressure and urgency.
- By misusing legitimate organizational values, attackers create the urgency needed for successful credential theft.
Themed Phishing is a Growing Trend
This Pride-based attack is part of a larger pattern where cybercriminals exploit timely themes.
In one study, newly registered vacation-themed domains jumped 55% year-over-year, and about one in 21 of those domains was flagged as malicious.
Another report showed a 620% spike in Black-Friday-related phishing emails within a single November, with phishers impersonating retailers to steal shopper credentials. These incidents illustrate that attackers treat any popular theme (travel, holidays, social causes) as a lure for phishing.
In practice, employees should assume that any major event or seasonal buzz could be weaponized. Charity drives, cultural months, or sales seasons have all seen spikes in scams. The Pride-themed email attack mirrors how holiday sales and travel booking scams work: it leverages predictable timing and widely discussed topics to sneak malicious links into inboxes.
Protecting Employees: Best Practices
The way to protect yourself from these social engineering attacks is to be aware of the situation. It is important to be aware of unusual or unexpected emails, regardless of whether they contain familiar wording or look “official.” Some important tips for protection include:
- Verify through official channels. Avoid clicking on “opt-out” or policy update links sent unsolicited. Instead, verify any new program or branding changes by contacting HR or IT directly.
- Watch for urgency and emotion. Be wary of emails centered on values or emotions (e.g., Pride, diversity, or other hot-button issues). Remember, legitimate internal announcements usually occur through standard company portals or mailing lists.
- Check the URL before clicking. Hover over any link to see where it will take you. Malicious links may use lookalike domains (e.g., slight misspellings or extra words). Some may require a CAPTCHA before sending you to a malicious site. If it looks suspicious, report it.
- Use multi-factor authentication (MFA). With MFA enabled, attackers cannot access accounts even if they have stolen your password. This is a simple way to prevent account takeover, even if your password is phished.
- Keep security systems updated. Email filters and browsers should be set to prevent known phishing sites. At least, make sure your browser or email client asks you to sign in after a CAPTCHA.
- Run simulated phishing tests. Simulate a phishing attack with social cause-related themes to test employees’ awareness. This will improve their vigilance over time.
In this particular case, anything that would deflect suspicion, such as sounding like an internal memo, would have likely led to a breach. It is important to be aware of unusual or unexpected emails, regardless of whether they contain familiar wording or look “official.” This way, organizations can prevent attacks like the Pride-themed scam.
Conclusion: When Social Values Become the Attack Vector
The Pride themed phishing campaign proves how quickly attackers can turn legitimate internal culture into a credential theft operation. Two waves, Dec 2025 and Jan 2026, used trusted email delivery infrastructure, realistic HR style messaging, and an opt out hook that redirected employees to a fake login flow after a CAPTCHA step.
Why This Threat Scales So Fast
This was not a small campaign. The first wave targeted about 504 organizations, then expanded to nearly 4,768 organizations the next month, a 9.4x jump as attackers refined lures and target lists. Most targets were in the US and the UK, with additional victims across multiple regions.
Why Every Organization Is Vulnerable
Attackers win by exploiting predictable human reactions, not technical gaps.
- Messages look like standard internal announcements, often tied to HR or branding updates.
- Both supporters and skeptics are pulled into the same click path through the opt out mechanic.
- Legitimate sending services and a CAPTCHA step reduce suspicion and bypass basic filters.
If a user reaches the fake login page, the hardest part of the attack is already done.
Where Xcitium Changes the Outcome
With Xcitium Cyber Awareness Education and Phishing Simulation, this campaign would not succeed because the attacker’s advantage collapses at the human decision point.
- Employees learn to spot value themed urgency and verify through official channels before clicking.
- Simulated campaigns build muscle memory for pause and verify behavior under realistic lures.
- Suspicious links, CAPTCHA gates, and login prompts are questioned before credentials are entered.
Reduce Credential Theft Before It Starts
Attackers will keep weaponizing timely themes. The winning defense is training that prevents the click, and rehearsal that prevents the login.