The Shai-Hulud worm targeted the npm packages quite aggressively and led to the compromise of 400,000 developer credentials.
This threat actor’s actions are attributed to the self-propagating worm Shai-Hulud’s recent supply-chain attack in the npm software repositories. The worm launched its second wave lately and managed to compromise various npm packages while revealing 400,000 secrets in about 30,000 GitHub repositories. Despite some noise, over 60% of stolen npm supply-chain tokens remained valid in early December 2025, per Wiz Labs.
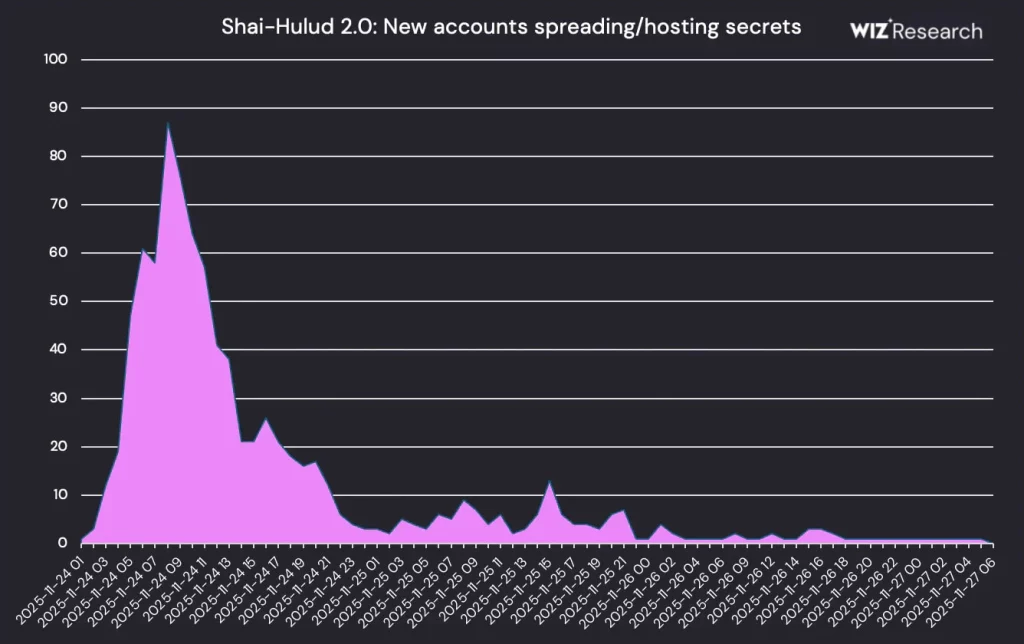
Source: Wiz
What Was Exposed: Developer Secrets at Risk
- Valid secrets: The data leak contained a considerable number of valid secrets, including cloud accounts, NPM tokens, and version control secrets.
- Extent of data leak: The leaked data included credentials and other sensitive information from developers.
- GitHub usernames and tokens: About 70% of the GitHub repositories with harmful usages had contents.json files that contained GitHub handles and tokens.
- Environment and CI/CD info: About 80% of the repositories contained information in the environment.json file regarding operating systems and other credentials.
- GitHub Actions secrets: Hundreds of repos contained
actionsSecrets.jsonfiles with GitHub Actions secrets. - The harvested sensitive data: The attackers harvested authentication tokens from npm, cloud API keys, and other developer credentials.
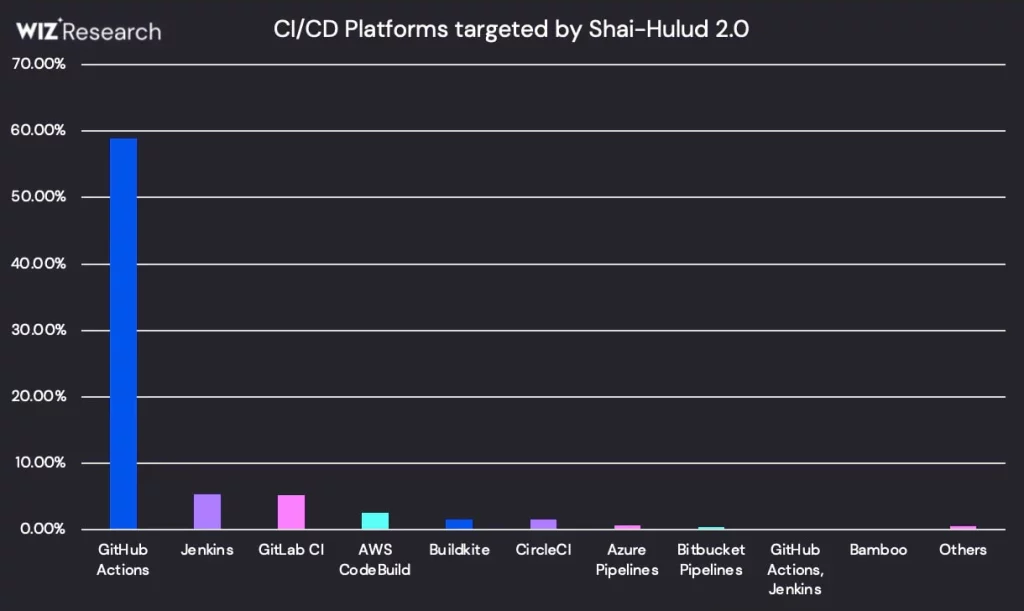
Source: Wiz
Who Is Affected: Developers, Organizations, and Build Pipelines
- Scope of impact: The breach affected the entire npm ecosystem, including major libraries and tools.
- Examples of compromised packages: Over 186 packages were infected, including vetted tools for Zapier, Ethereum Name Service, PostHog, and Postman.
- npm ecosystem scale: With 800,000+ packages and millions of daily downloads, virtually any Node.js project could unknowingly depend on a trojanized component.
- Pipeline risk: The vulnerability of one flawed library can put the entire pipeline or program in jeopardy.
- Vulnerable environments: Both individual developer machines and CI/CD pipelines were at risk.
- Source of leaked environments: About 23% of leaked environments came from personal developer workstations, the rest from automated build servers.
- Operating systems and platforms: Linux systems made up 87% of infected machines, with GitHub Actions as the primary CI platform.
- Practical implication: Installing a compromised npm package on a developer’s laptop or in a build container could silently infect that environment.
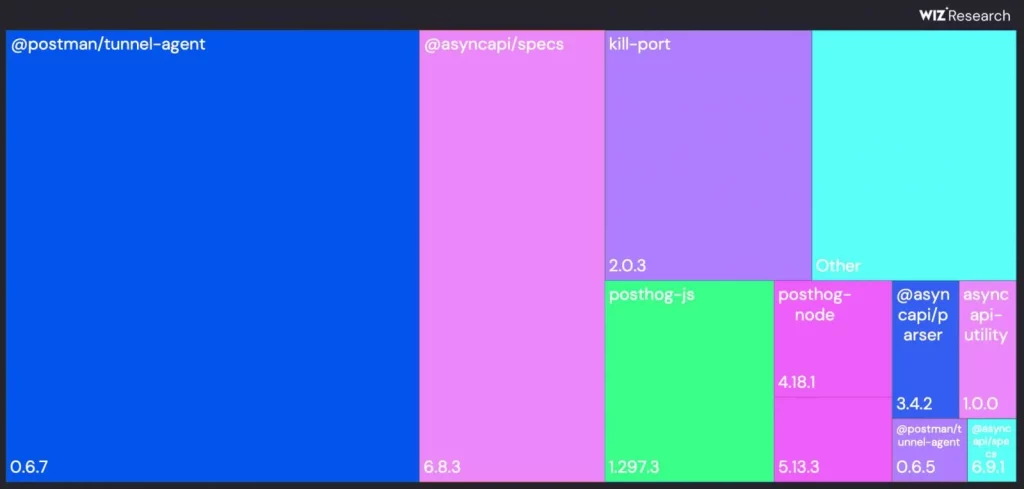
@postman/tunnel-agent@0.6.7 and @asyncapi/specs@6.8.3 as the top infected packages, together accounting for over 60% of all infections.Source: Wiz
Systemic Supply-Chain Risks and Lessons
The Shai-Hulud incident highlights the vulnerability of the open-source supply chain. The worm added code to common packages, turning routine npm install commands into attack vectors.” According to GitHub’s cautionary remarks regarding supply-chain breaches: “These types of breaches erode trust in the open source ecosystem and put the integrity and security of the entire software supply chain at risk.”
However, security analysts point out that this provides what can be considered a sector-wide problem. According to analysts, “software supply chain security is now a boardroom issue,” not only because one faulty library can create a company-wide problem but because today’s trusted dependency may become tomorrow’s backdoor if the developer token or the signing key gets leaked.
Conclusion: A Supply-Chain Breach With Global Impact
The Shai-Hulud attack exposed a painful truth: the modern software ecosystem is only as strong as its weakest dependency. A single self-propagating npm worm managed to steal 400,000 developer secrets, infect 186+ packages, and silently compromise CI/CD environments worldwide. No zero-day was needed just leaked tokens, poisoned packages, and automated pipelines executing code by default.
One compromised library became thousands of compromised environments.
Why Every Engineering Team Is at Risk
Today’s developers unknowingly inherit enormous attack surface area. Trusted packages, automated installs, and interconnected build systems create perfect conditions for supply-chain abuse:
- Unverified dependencies
- Secrets exposed in configs and pipelines
- Build servers running untrusted code
- CI automations executing malicious scripts instantly
- Developer workstations with broad access
If one maintainer or token falls, entire pipelines fall with it. That’s why supply-chain breaches spread so fast—and why no organization is exempt.
Where Xcitium Stops the Attack Chain
With Xcitium Advanced EDR, trojanized packages, rogue scripts, and modified installers are isolated the moment they execute before they can access secrets, infect pipelines, or spread across developer systems.
Supply-chain malware loses its ability to propagate.
Your software supply chain deserves Zero-Dwell security. Choose Xcitium Advanced EDR.