
ShinySp1d3r: The Rising Ransomware-Service An emerging ransomware-service, ShinySp1d3r has been developed by the infamous hacking groups ShinyHunters and Scattered Spider.
ShinySp1d3r is the new RaaS platform being developed by hackers linked to ShinyHunters and Scattered Spider groups. A pre-release version of this ransomware has been found on the VirusTotal recently, which gives a glimpse of the looming cyber extortion campaign. This development becomes crucial because this group of hackers has been depending on the ransomware provided by rival groups like ALPHV before. They are developing their RaaS platform which would be exclusively used by them and their partners. ShinySp1d3r also signifies the coming together of the primary cyber gangs.
In this article, we will examine who ShinyHunters and Scattered Spider are. Finally, we will also provide insight regarding the uniqueness of ShinySp1d3r and ways that an organization can protect themselves from this rising threat.
ShinyHunters: From Data Breaches to Ransomware
ShinyHunters is a financially driven cyber hacking group that originated in approximately 2020. The group first gained prominence as a result of numerous company hacks where they managed to obtain the credentials of hundreds of millions of users. To cite an example, ShinyHunters hacked the Tokopedia platform in the year 2020 and managed to obtain the credentials of 91 million users and also claimed to obtain 500GB of Microsoft’s internal source code. The hackers would then extort the targeted company and threaten them that the data will be sold in the dark web.
ShinyHunters has been evolving from simple data breaches to attacking big corporations and cloud services over the past few years. In the year 2025, they employed vishing attacks to break into the Salesforce portals of various companies to steal over a billion customer records. They also created a victim shaming blog to threaten dozens of Fortune 500 companies to release their own stolen data. The growth of ShinyHunters from breaching websites to planning the complete extortion of businesses reveals their level of ambition and level of sophistication. Currently, ShinyHunters seem to be upgrading from stealing data to encryption-based extortions through the development of the ShinySp1d3r ransomware.
Scattered Spider: Social Engineering and Big-Game Hacks
Scattered Spider (also known as UNC3944) is another sophisticated hacking group that has been operating since about 2022. This group has been recognized for their sophisticated social engineering attacks such as SIM swap and phishing. They employ these attacks to create initial access to large firms. Members of Scattered Spider reportedly are teenagers and young individuals from the US and UK. They gained popularity due to their attacks against prominent firms in various sectors.
In the year 2023, they perpetrated extortion attacks against Caesars Entertainment and MGM Resorts. In the course of the attacks, they collaborated with the ALPHV (BlackCat) ransomware group. They also attacked firms like Visa, Twilio, and Jaguar Land Rover.
Scattered Spider: This group can be considered hazardous because their targets are large and valuable enterprises. They are known for deceiving the help desk and exploiting identity services. In the MGM hack, they pretended to be an employee when engaging the help desk. This enabled them to enter the network and cause significant outages. Their brazen tactics result in enormous payouts, which Caesars has reportedly paid $15 million.
By the year 2025, Scattered Spider and ShinyHunters were closely affiliated. There are reports of them being combined under a single entity. This sets the stage for the combined RaaS effort known as ShinySp1d3r.
ShinySp1d3r RaaS: A New Alliance in Action
ShinySp1d3r is the combined effort of ShinyHunters and Scattered Spider groups operating under the same banner of “Scattered LAPSUS$ Hunters.” The group name itself combines the two groups’ efforts. The group’s telegram message about their extortion of the Salesforce breach victims indicates possible contributions from the ranks of the infamous group “Lapsus$.” ShinySp1d3r reflects the consolidation of various prominent cyber-criminal groups coming together to create a single RaaS platform.
Unlike many new ransomware strains that rely on leaked code, ShinySp1d3r’s encryptor was built entirely from scratch. A Windows sample analyzed by researchers highlights several advanced capabilities:
- Stealth & Evasion: Suppresses Windows event logs (EtwEventWrite), employs anti-analysis tricks, and wipes memory buffers to hinder forensics.
- Aggressive File Locking: Terminates processes that keep files open and can leverage Restart Manager to close stubborn applications.
- Data Destruction: Overwrites free disk space with large wipe-*.tmp files, making deleted data nearly unrecoverable.
- Lateral Movement: Spreads through Windows services, WMI, or GPO startup scripts, enabling rapid enterprise-wide compromise.
- Targeted Disruption: Kills specific processes (e.g., databases, security tools) and deletes Volume Shadow Copies to block easy recovery.
- Strong Encryption: Uses ChaCha20 with RSA-2048 key protection, unique per-file extensions, and custom headers containing encrypted metadata.
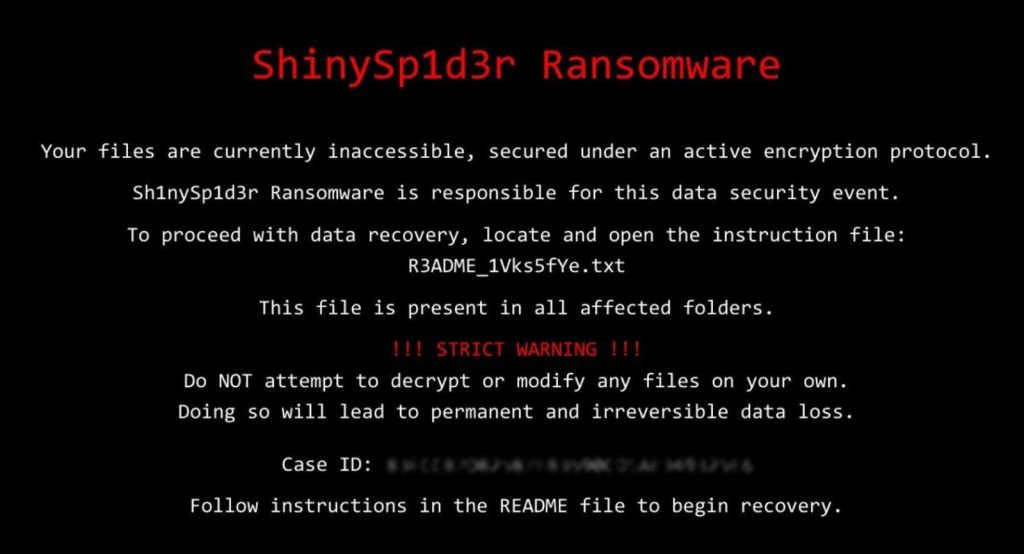
Source: BleepingComputer
ShinySp1d3r’s Extortion Model and Cross-Platform RaaS Capabilities
Once ShinySp1d3r has finished the encryption process, it leaves a ransom notice in each folder and changes the desktop wallpaper. The notice adopts a professional and almost polite tone—it refers to the event as a “critical encryption event” and presents a “confidential opportunity” to solve the situation—but at the same time states that the leaked data will be posted online if negotiations do not begin in the next three days. The victims are asked to communicate through TOX and then through the Tor leak website, which confirms the standard double-extortion scheme.
ShinySp1d3r also has the functionality to work across various environments. In addition to its locker available on Windows, the actors have completed work on the Linux CLI version and are close to finishing the ESXi version of the tool, enabling it to target the affected server and virtualization environment. ShinyHunters also hinted at its lightning version written purely in the Assembly code. Being a RaaS itself, ShinySp1d3r will be run by ShinyHunters through its identity as the Scattered LAPSUS$ Hunters affiliate network, who will then wage the attacks and split the earnings. The group also has rules about what they target, which mostly include the exclusion of CIS and healthcare targets. However, this itself has become disregarded at this point in time. Ransomware development has been entirely in-house thanks to the release of ShinySp1d3r.
Ransomware Trends and ShinySp1d3r’s Significance
The emergence of ShinySp1d3r shows major changes in the ransomware landscape. Ransomware attacks continue to rise worldwide, increasing 73% this year. RaaS platforms fuel this growth and make attacks easier. The strong financial rewards push groups like ShinyHunters to shift from data theft to encryption-based attacks. By running their own RaaS, they avoid relying on gangs like BlackCat. This lets them earn more and develop custom malware with better evasion.
Another trend is the merging of threat groups. ShinySp1d3r demonstrates how different specialists now combine skills. Scattered Spider brings social engineering expertise, while ShinyHunters contribute large-scale attack experience. Actors linked to Lapsus$ add further capabilities. This mix enables attacks that steal data, deploy ransomware, and mimic insider behavior. Evidence suggests Scattered Spider and ShinyHunters now operate as one team.
Finally, ShinySp1d3r’s tooling highlights modern ransomware capabilities. Its custom malware spreads across networks and removes logs. It also blocks recovery efforts and targets Windows, Linux, and ESXi. As cybercriminals create code that avoids signature detection, security strategies must evolve as well.
Conclusion
Ransomware like ShinySp1d3r moves faster than traditional defenses can react. By the time alerts fire, data is already encrypted, stolen, or leveraged for extortion. Modern organizations need protection that assumes compromise and stops attacks the moment they execute.
Xcitium’s patented Zero-Dwell platform does exactly that. Every unknown file is isolated instantly in a secure virtual layer, unable to encrypt data, move laterally, or damage systems. Even never-before-seen ransomware variants are neutralized in real time.
Zero dwell time. Zero impact. Zero chance for attackers to succeed.
While others scramble to detect threats, Xcitium = No Ransomware. Your endpoints stay fully protected silently in the background, keeping users productive and threats harmless. Against sophisticated RaaS operations like ShinySp1d3r, this proactive approach is the difference between compromise and complete security.
Stop ransomware before it strikes—upgrade to Xcitium’s Advanced EDR today.




