
A Chinese threat actor codenamed “Silver Fox” has been tricking users with a fake Microsoft Teams download to spread the ValleyRAT malware.
Apparently, recent studies also identified a hidden cybercampaign wherein the Silver Fox group, imitating a Russian threat actor, injected a remote access Trojan on targeted Chinese entities. This particular cyberactivity used search engine optimization (SEO) poisoning for the propagation of a fake Microsoft Teams installer, which helped facilitate the download of the ValleyRAT malware, also known as Winos 4.0. The ValleyRAT malware, a Gh0st RAT variant, provides attackers with the fullest possible control of the target computer, hence suitable for espionage and malicious purposes. It is reported that over a third of social engineering attacks of 2025 used non-phishing methods, including the use of SEO poisoning.
Silver Fox APT and Its Deception Tactics
Silver Fox is the alias of a sophisticated threat actor, or group of actors, native to the Chinese threat landscape that combines espionage and financial crimes. In this particular campaign, the group used false-flag tactics for the purposes of deceiving analysts, and these include the use of characters of the Cyrillic script, meaning the malware loader simulated Russian origin. While ruse and masquerading as other hackers, regardless of their location, are not that common, it works effectively. According to security experts, Silver Fox sets out to achieve twofold goals: the exfiltration of valuable data and the monetization of those efforts, hence the use of fraud. The group even goes a step further and modifies the toolkit they use, for example, ValleyRAT, a remote access Trojan that, until the recent past, targeted the efforts of various Chinese hacking crews, for the purposes of facilitating deep infections.

Fake Teams & SEO-Poisoning Scheme
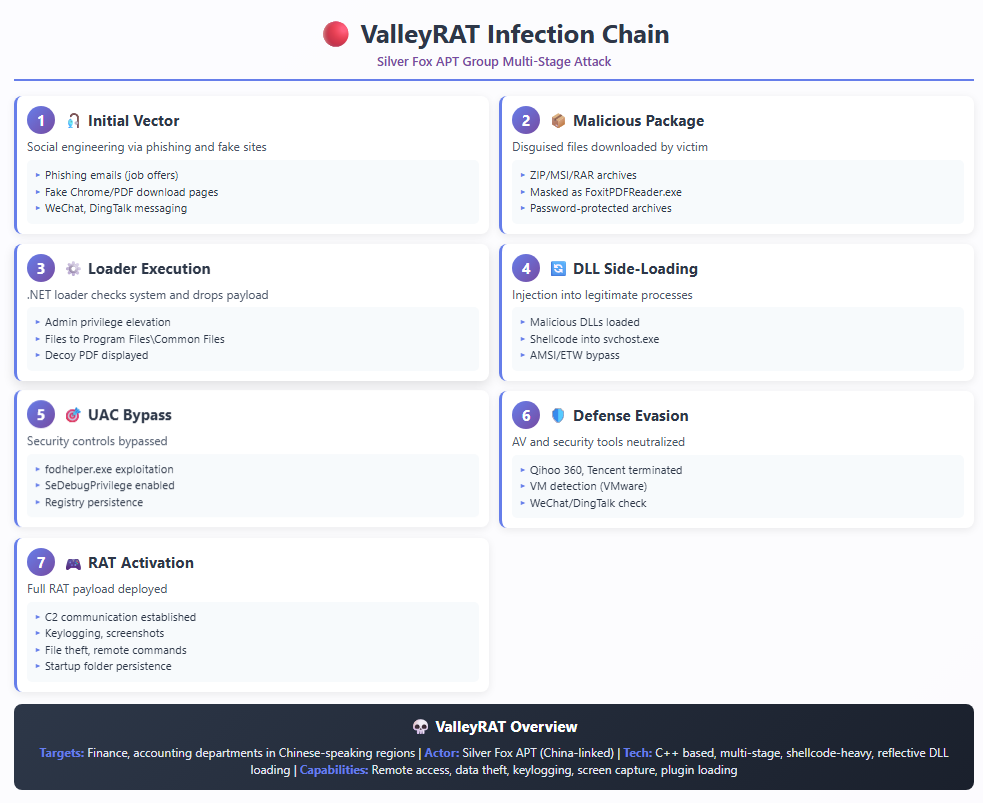
However, instead of using the phishing email technique, Silver Fox used manipulated search engine results. This was whereby the attackers created a fake download page that mimicked Microsoft Teams. According to Fortinet researchers, attackers often use fake software pages and search engine optimization. This fake Microsoft Teams page provided a download link named “MSTчamsSetup.zip,” where the second letter “T” was replaced with a letter from the Cyrillic alphabet.
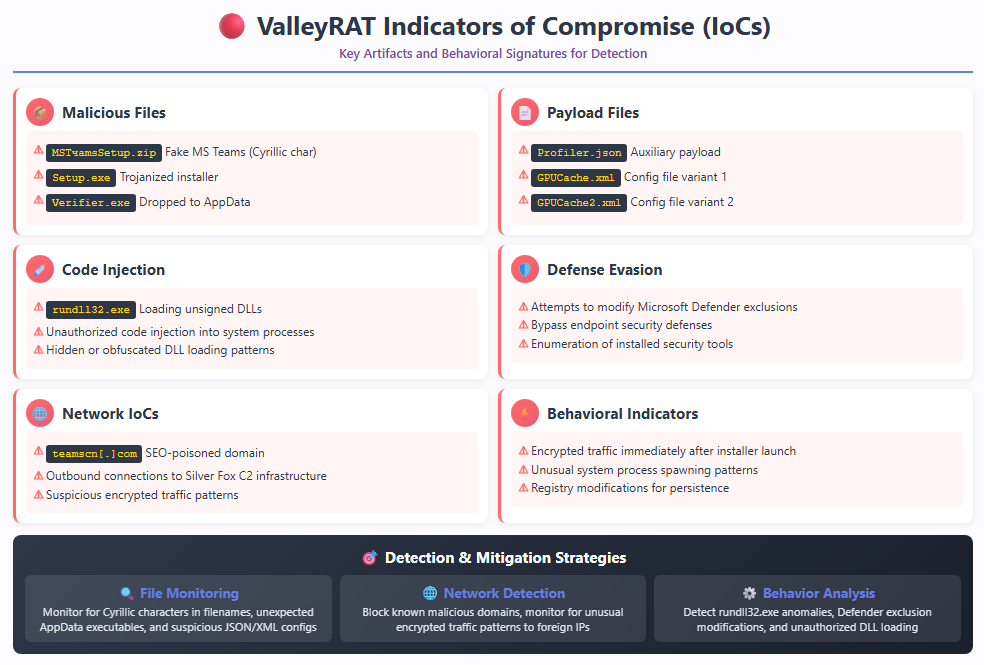
After the execution of the “Setup.exe” present inside the zip file, the process moved on to the next phase. The malware allegedly carried out the Teams installation process, but instead, it was a trojanized version. It started searching for the security software installed on the computer, including 360 Total Security, and subsequently avoided system defenses by adding exceptions in the Microsoft Defender. This made it less likely for it to be blocked. The malware also dropped a hacked version of the genuine Windows installer, “Verifier.exe,” into the AppData folder of the user. Additionally, it dropped innocuous files, including “Profiler.json” and the GPUCache XML files, into the user profile.
- The attacker’s code places these auxiliary files (Profiler.json, GPUCache.xml, and so on) into the user’s profile.
- It then uses the genuine rundll32.exe process, which loads the hidden malicious DLL into the computer’s memory, thus avoiding detection.
- Finally, the malware will communicate with the server, downloading the final payload, the ValleyRAT, a backdoor that provides complete control of the infected computer.
To conclude, the user will go through the typical process of installing Teams, but the malware will disable defenses, load the malware, and install the ValleyRAT malware into the computer’s memory, so that by the time the warning messages happen, the backdoor will already have control of the computer.
ValleyRAT: A Potent Remote Access Trojan
- ValleyRAT (Winos 4.0) is a RAT that grants attackers extensive control over compromised hosts.
- After infection, it can execute commands, steal data, and remain hidden.
- It can create hidden backdoors, such as new accounts or services, to maintain persistence.
- Compromised machines can be turned into beacons for the attacker’s botnet.
- Researchers note that ValleyRAT enables remote operation, data exfiltration, and arbitrary command execution.
- The malware continuously compromises the workstation and leaks business data until detected.
- Its fake Microsoft Teams installer helps it evade many traditional antivirus scanners.
Other ValleyRAT Campaigns and Trends
The Teams phishing campaign is merely one example of the evolution of attacks on the scene. There is also the campaign that used the trojanized Telegram installer, which installed the ValleyRAT by loading a vulnerable driver (the BYOVD Bring Your Own Vulnerable Driver method) that neutralized the security software.
Variants also targeted individuals looking for jobs, phishing messages that contained a fake Foxit PDF Reader. In this case, the malware, FoxitEXE, sideloaded the fake DLL named “msimg32.dll,” which ran a script that installed the Python payload, eventually executing the ValleyRAT. Effectively, the attackers targeted individuals seeking jobs by hiding the malware within a PDF reader.
Such trends demonstrate that the underlying truth is that attackers will use trusted applications as a cover. Attacker creativity allows for innovative ways of camouflaging their malware. Over the year 2025, over a third of social-engineering attacks used either new approaches, including SEO poisoning and fake prompts, indicating that users who installed genuine apps are also not safe.
Defending Against SEO-Poisoning Attacks
- Employees should stay alert to unexpected downloads.
- Always verify download URLs and digital signatures.
- Use multi-layered security (endpoint protection, web filtering, patching).
- Enable PowerShell and rundll32.exe logging.
- Check for unusual outgoing connections on the network.
- Run new or unverified programs in isolation until confirmed safe.
- Kernel virtualization helps stop threats that bypass detection.
- Silver Fox shows the need for user training, modern endpoints, and strict software installation policies.
Case Study: Xcitium vs. Silver Fox ValleyRAT
The following demonstration shows how Xcitium neutralizes the malicious MSTчamsSetup.zip file used in the latest Silver Fox APT campaign. This file masquerades as a legitimate Microsoft Teams installer, leveraging SEO-poisoned download pages to lure victims into executing a trojanized setup package.
Once launched, the loader attempts to modify system defenses, add exclusions to Microsoft Defender, and ultimately deploy the ValleyRAT backdoor a remote access Trojan capable of full system control, data exfiltration, and long-term persistence. In our test environment, Xcitium’s ZeroDwell technology intercepted the file the moment it attempted to execute, isolating the unknown process before it could disable protections or load the hidden DLL. The threat is isolated instantly, preventing the payload from ever reaching memory.
This real-world scenario highlights why modern attacks require more than traditional detection: they require proactive isolation that stops threats before they act. This video illustrates exactly how Xcitium disrupts sophisticated, deceptive malware like ValleyRAT at the very first touchpoint.
A New Era of Deception-Driven Malware
Silver Fox’s ValleyRAT campaign demonstrates how modern APTs no longer rely on phishing alone.
They exploit trust.
They exploit search engines.
They exploit the everyday software users believe is safe.
By turning a fake Microsoft Teams installer into a fully weaponized delivery system, Silver Fox bypassed traditional defenses, disabled protections, and deployed a highly capable RAT directly into memory long before most security tools could even react. It’s a reminder that attackers no longer need complexity when they can simply mimic the tools workers use daily.
Why Every Organization Is Vulnerable
SEO poisoning, fake installers, and trojanized software downloads are now core APT tactics. Any user searching for a legitimate tool can unknowingly download malware. Trusted applications become attack vectors; familiar interfaces become traps.
Organizations relying on detection-based security face the same blind spot: if an installer looks legitimate, users will run it and malware will execute before alarms ever sound. ValleyRAT proves how quickly that window can be exploited for espionage, data theft, and persistent access.
How Xcitium Prevents This Attack From Ever Succeeding
In every scenario where ValleyRAT succeeds, Xcitium Advanced EDR changes the outcome entirely.
Xcitium isolates unknown installers the moment they attempt to execute before they disable protections, before they load malicious DLLs, and before they embed backdoors into the system.
Fake Teams installers?
Trojanized Telegram packages?
Compromised PDF readers?
All become harmless inside Zero-Dwell isolation, unable to touch the real operating system or exfiltrate data.
Silver Fox’s deception fails because the malware never reaches the operating system in the first place.
Strengthen Your Defense Against Modern Social Engineering
Attackers now weaponize trusted brands, trusted downloads, and trusted search results.
To defend against deception at this scale, organizations need security that stops unknown processes before they act not after the damage is done.
Protect your users from the malware they cannot see coming.
Choose Xcitium Advanced EDR.




