The Call is Coming from Inside Your Home Network
While cybersecurity previously focused on securing the corporate perimeter, with the rise of working from home, it now focuses on our own homes. Thus, when we are streaming, we are unaware that a silent threat is lurking in the shadows. IoT-based cyberattacks are rising, which bypass traditional firewalls.
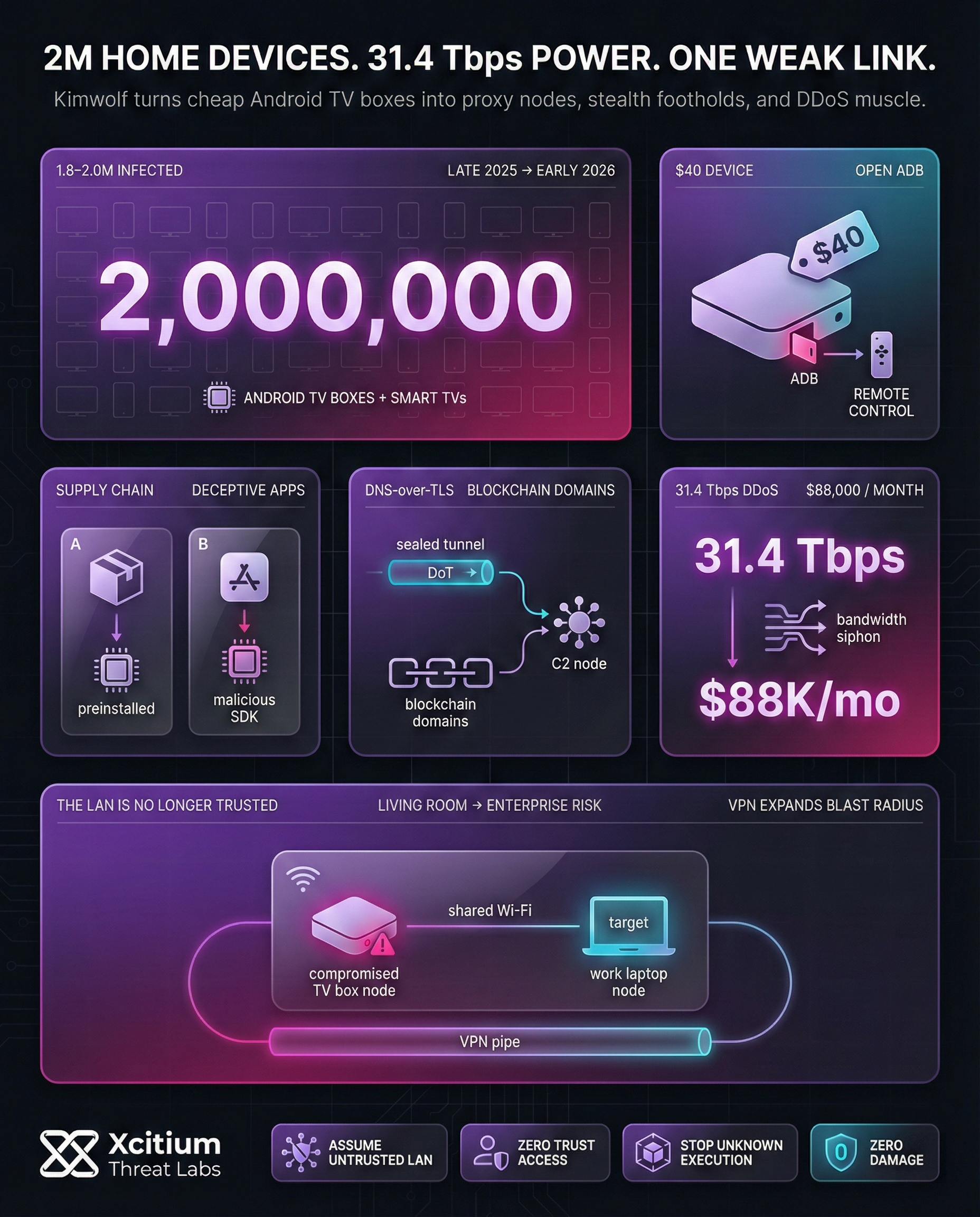
The Kimwolf Botnet is another threat that has risen in early 2026, with over 2 million devices being compromised. That harmless device for streaming, which only costs you $40, could be a gateway for cybercriminals. The devices now share your home WiFi with your work laptops. Thus, your work data security now depends on the weakest link in your home WiFi.
How Cheap Hardware Becomes a High-Tech Trojan Horse
Many users choose to buy off-brand Android TV boxes because they are cheaper. However, it has also been observed that such devices have pre-installed malware or backdoors. Kimwolf botnet targets devices that have poor security oversight. For example, it has been observed that many Android TV boxes have an open Android Debug Bridge (ADB) port, giving hackers full control over the device without their knowledge.
Monetizing this infection is also very efficient. There are two main ways through which Kimwolf botnets infect devices and then sell their services to cybercriminals:
- Supply Chain Poisoning: Here, malware is preinstalled into devices.
- Deceptive Applications: Users are tricked into downloading free apps that have malicious SDKs embedded into them.
- Residential Proxy Nodes: The bandwidth of devices is sold to cybercriminals, who then use it for illicit activities.
Your streaming box now becomes a “clean” exit node for fraud. Kimwolf botnets earn nearly $88,000 monthly from this illicit business.
KIMWOLF transforms your living room into a weapon.
Why Your Current Security Tools Are Failing You
The standard antivirus software and office VPNs may not be effective against Kimwolf. This botnet is developed to be invisible to standard security measures. It uses DNS-over-TLS (DoT) to hide communications within encrypted channels. Traditional firewalls do not allow these communications to be inspected, enabling malicious communications to be transmitted. In addition, this botnet employs blockchain domains, which can never be seized by law enforcement.
The magnitude of this threat is huge. In late 2025, Kimwolf was linked to a 31.4 Tbps DDoS attack. Home devices infected with this malware enabled this huge attack. Therefore, it is possible that your TV box may be part of cyberwarfare while you are streaming. This situation implies that we can no longer trust the local area network (LAN).
Kimwolf Botnet Key Facts (2025–2026)
- The Kimwolf botnet was said to have infected between 1.8 to 2 million Android devices, mainly Android TV boxes and smart TVs, from late 2025 to early 2026.
- The researchers noted that most infected devices had pre-installed malware or had open ADB services, which enabled the widespread compromise.
- The Kimwolf botnet was also associated with internet-scale DDoS attacks that exceeded 31 Tbps. This demonstrates the escalating use of consumer devices.
- Aside from this, infected devices were also used to carry out residential proxy node activities, which enabled cybercriminals to monetize household internet connections.
Transitioning to a Zero Trust Future with SASE
The outdated security model is “Castle and Moat.” This model is no longer viable since it is not possible to police every device at home. Hence, there needs to be a change in this approach. This is where the concepts of SASE and Zero Trust come in. This will mean that the network at home is treated like a public hotel lobby, where every connection will be validated.
The following are some of the major defense elements of SASE:
- Identity-Based Access: This means access will be given on the basis of identity rather than the location of the network.
- Continuous Monitoring: Every packet will be checked to see if there is any malicious activity happening in real time.
- Encrypted Bubbles: Corporate resources will be secured at all costs, irrespective of the LAN.
The VPN model needs to be abandoned altogether since it gives access to everything. Zero Trust Network Access needs to be implemented to ensure that, in case the TV box gets compromised, it doesn’t get access to the corporate laptop.
Protecting the Modern Remote Work Environment
Education and awareness are also essential, and technical solutions must be complemented with these. Employees must be educated on the dangers of “gray market” electronics to their personal privacy and job security. Companies must also offer clear advice on safe devices to use at home on their networks. Regular security audits on access logs can also help detect suspicious activity before breaches happen.
The battlefront in cybersecurity has shifted from the data center to homes. We must evolve to assume that every network is compromised. Using SASE and Zero Trust can help us build strong defenses, even against internal threats.
Conclusion: Your “Home” Network Is Now the Threat Surface
Kimwolf shows how quickly consumer IoT can become operational risk. A low-cost Android TV box can be compromised at scale, then repurposed as a residential proxy node, a stealthy foothold, or part of massive DDoS activity, all while sharing the same WiFi as corporate endpoints.
Why This Matters for Remote Work
The weak link is no longer the data center. It is the living room.
Kimwolf targets unmanaged devices, abuses open ADB exposure and poisoned supply chains, and hides command and control through encrypted channels that traditional controls struggle to inspect.
Why Most Organizations Are Vulnerable
Even mature companies inherit home network risk.
- Unvetted “gray market” devices sit on trusted LANs
- Visibility stops at the perimeter, yet the attacker is already inside the same WiFi
- Encrypted C2 and hard-to-seize infrastructure reduce simple blocking options
- VPN-style access can expand blast radius once any nearby device is compromised
Where Xcitium Changes the Outcome
If you have Xcitium, this attack would NOT succeed in the way attackers need.
With Xcitium Advanced EDR, unknown execution on the corporate endpoint is stopped at runtime, code can run without being able to cause damage. Even if a compromised IoT device shares the network, the attacker cannot turn proximity into endpoint compromise, data access, or disruption.
Secure Remote Work for the World We Actually Live In
Assume the home network is untrusted. Enforce Zero Trust access, reduce exposure, and stop execution risk on endpoints before consumer IoT turns into enterprise impact.




