
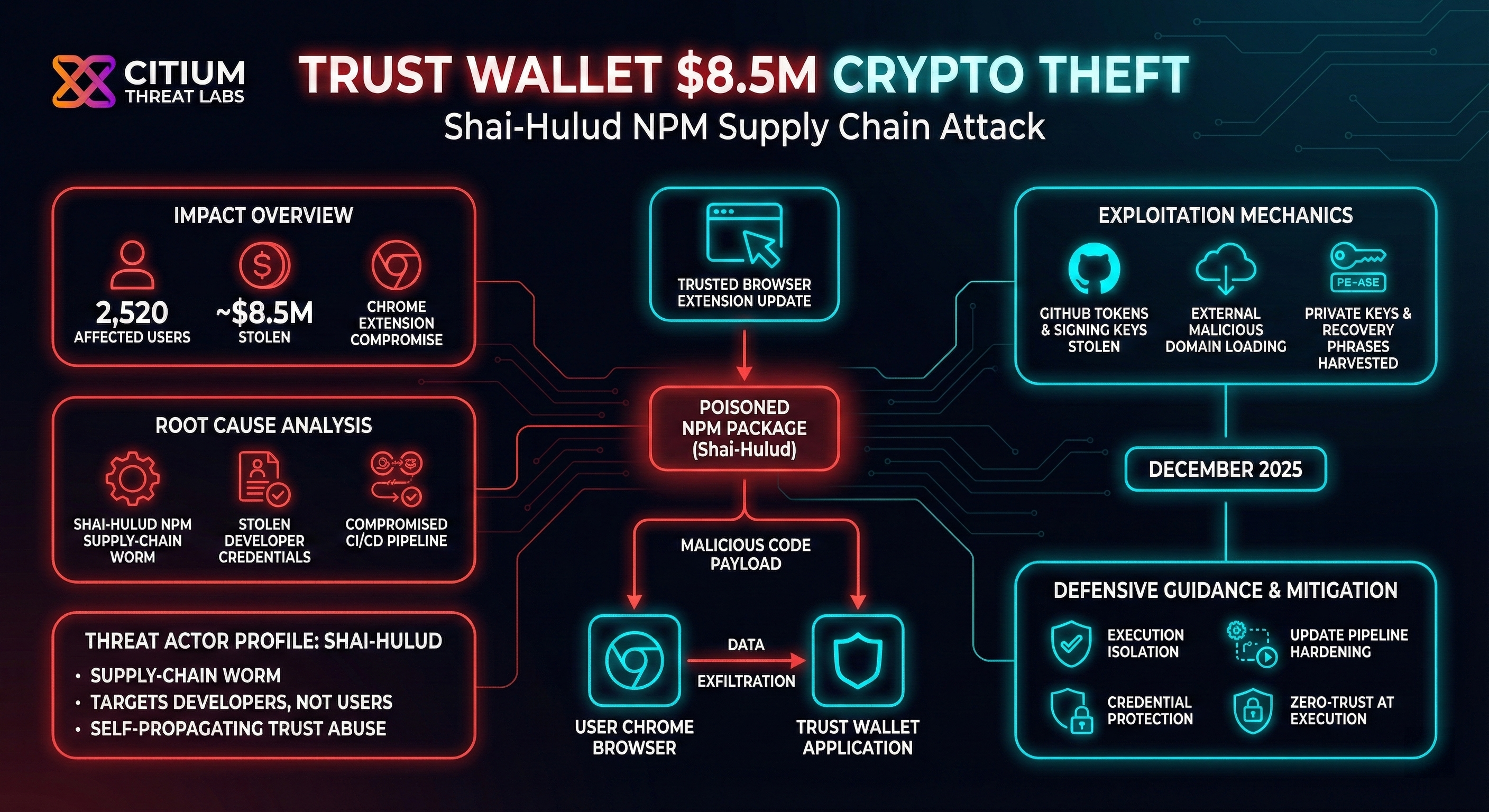
The browser extension of the Trust Wallet was compromised by a supply chain worm attack; hence, 2,500+ wallets lost $8.5 million. Discover how the Shai-Hulud NPM attack made the entire process of this cryptocurrency theft possible.
In the latter part of December 2025, the Trust Wallet, a widely popular crypto wallet with over 200 million users, experienced a severe security attack when the crypto wallet’s Chrome extension was hacked by the attackers, leading to the loss of cryptocurrency for over 2,500 users worth $8.5 million. However, the hacking incident is not the only event experienced by the Trust Wallet; rather, it is connected to another massive software supply chain attack called Shai-Hulud.
Trust Wallet Breach Summary
Root Cause Analysis
Attackers compromised Trust Wallet’s internal secrets through the Shai-Hulud NPM supply-chain malware campaign.
Action Taken
- Patch Release: Clean update (v2.69) was deployed immediately.
- User Reimbursement: Financial recovery process initiated for affected wallets.
- Forensic Investigation: Continuous auditing of internal CI/CD pipelines.
How Attackers Exploited Trust Wallet’s Extension
- Stolen developer credentials (GitHub token + Chrome Web Store publishing key) were compromised.
- This allowed attackers to infiltrate Trust Wallet’s official release pipeline.
- A trojanized Trust Wallet browser extension (v2.68.0) was uploaded.
- The malicious version went live on the Chrome Web Store on December 24, 2025.
- The update was automatically pushed to users as a routine extension update.
- Attackers registered a fake domain:
metrics-trustwallet.com. - The compromised extension loaded external malicious scripts from this domain.
- These scripts harvested: Recovery phrases, private keys, wallet authentication data
- The stolen data was used to authorize unauthorized crypto transactions.
- Any user who accessed Trust Wallet via the extension during the attack window effectively handed full control of their funds to the attackers.
Trust Wallet’s Response and Recovery Efforts
Trust Wallet’s team reacted quickly once the breach was discovered. They immediately took several steps to contain the damage and secure their platform:
Incident Response
Access Revoked
API keys and developer credentials invalidated.
Domains Blocked
Malicious hosting domains suspended.
Clean v2.69 Live
Extension patched. Immediate update required.
Full Compensation
Assets returned to 2,520 affected users.
- Revoked Developer Access: The exposed API keys and developer credentials (including the Chrome Web Store API key) have been immediately revoked in order to stop the attackers from distributing further malicious updates.
- Malicious Domains Shut Down: Notified the registrar of the rogue domain hosting malware, which suspended it and ceased the malware data flow.
- Secured Extension Update: The group released a clean version 2.69 of the Chrome extension and encouraged users to install it to remove the malicious version.
- Affected Users Reimbursement: Commenced reimbursing about 2,500 users for stolen property, vowing to compensate all users back to wholeness after the occurrence.
- Security Alerts: Warned users of follow-up scams (such as impersonators pretending to be from Trust Wallet support with “compensation” forms), and reminded everyone to communicate only through authorized channels.
Moreover, Trust Wallet’s release process in the future will be even more secure for its customers. For example, updates for new extensions will need additional approvals before they are allowed for release. Therefore, even when accounts or keys are compromised, there will be no single point of failure through which malicious code can easily be delivered to customers in the future.

Shai-Hulud: The Supply Chain Worm Behind the Breach
The Shai-Hulud malware attack was a huge attack on a software supply chain that targeted the NPM package ecosystem towards the end of 2025. This self-replicating worm attacked thousands of JavaScript libraries and leaked all the sensitive data of any development environment that used them to the attackers by including any necessary malicious code.
In essence, there were a total of hundreds of thousands of private credentials made vulnerable in the Shai-Hulud operation. Unfortunately, the result is also reflected in the fact that the developer secrets of the Trust Wallet were breached as well. This is how the attackers acquired possession of the necessary keys in order to backdoor the Trust Wallet extension.
Why Shai-Hulud Is More Dangerous Than Traditional Malware
Shai-Hulud was more than just a malware attack, in that it was a supply chain worm that was self-propagating in nature, aimed at weaponizing trust in the context of modern software development.
While traditional ransomware or info stealers would target end users, Shai-Hulud focused on developers, CI/CD tools, and package managers the factories where the software the world runs on is produced.
After the infected NPM package had been introduced onto the scene by one developer, the malware silently operated in the following way:
- Stole GitHub tokens, NPM credentials, cloud API keys, and signing secrets
- Exfiltrated them to attacker-controlled servers
- Used those stolen identities to move laterally into build systems
- Then injected malware into legitimate software updates
This is how Shai-Hulud scales.
It doesn’t need to hack companies one by one it lets companies unknowingly hack themselves.
Conclusion: When Supply Chains Become the Attack Vector
The Trust Wallet breach delivers a clear warning for every organization building, shipping, or distributing software. This was not a user mistake and not a traditional malware outbreak. It was a supply chain failure, where a single stolen developer secret enabled attackers to push malicious code to millions of trusted endpoints.
Once the update pipeline was compromised, the damage scaled instantly.
Why This Threat Changes the Risk Model
Modern software trust is fragile, and attackers know exactly where to strike:
- Developer credentials grant direct access to release pipelines
- CI and build systems execute code by default
- Browser extensions update automatically without user scrutiny
- One poisoned package can impact millions of users at once
- Trust is inherited, not verified, at execution time
When software updates are trusted blindly, every user becomes a downstream victim.
Where Xcitium Changes the Outcome
For organizations using Xcitium Advanced EDR, this attack fails at execution.
- Trojanized updates are isolated the moment they attempt to run
- Malicious scripts cannot access keys, wallets, or browser data
- Code can run without being able to cause damage to the real system
- Credential theft and lateral movement never begin
- Supply chain abuse loses its ability to scale
Xcitium removes the attacker’s advantage by enforcing execution control, even when trusted software is compromised.
Secure the Software Your Users Trust
Supply chain attacks succeed because they exploit trust, not vulnerabilities. Prevention must happen where trust breaks, at execution.
Protect your developers.
Protect your update pipelines.
Protect your users.
Choose Xcitium Advanced EDR.




