Discover how the Sneaky 2FA phishing kit uses AiTM and BitB techniques to bypass multi-factor authentication. Learn about the latest cyber threats and how to protect your digital assets.
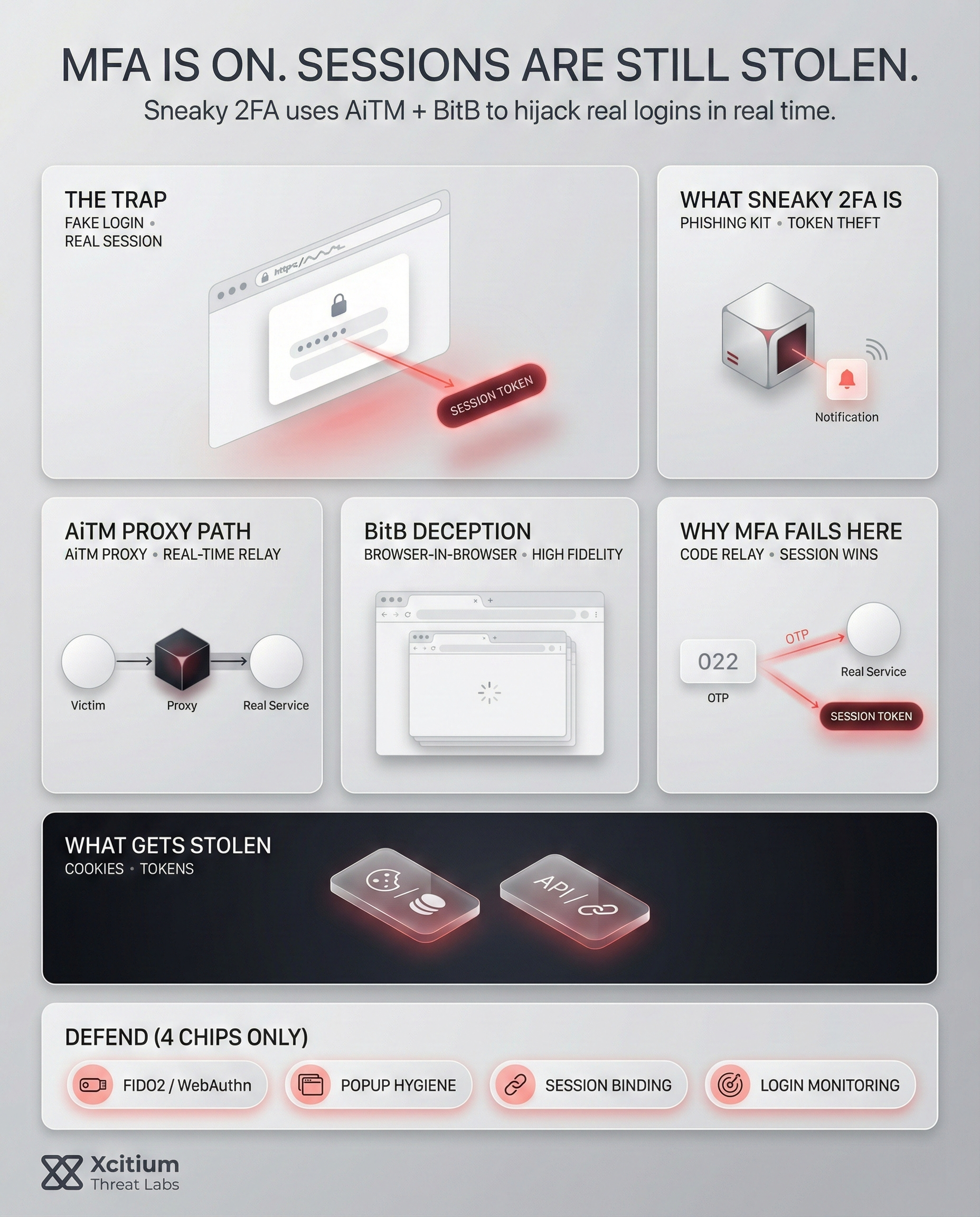
The cyber security environment is constantly changing with the development of new and sophisticated tools for evading security. The most recent and frightening development is the appearance of the Sneaky 2FA phishing kit. This is a sophisticated phishing kit that targets the most trusted security practices. This means that multi-factor authentication is no longer the answer to all security questions. We need to be aware of the new threats.
The Rise of Adversary-in-the-Middle Attacks
The Sneaky 2FA kit mainly functions by utilizing a method named Adversary-in-the-Middle (AiTM). This method is different from traditional phishing, where attackers only steal user passwords. Instead, the Sneaky 2FA kit functions as a real-time proxy, which means it works as an intermediary between the victim and the legitimate service provider. This allows attackers to skip the 2FA process altogether by hijacking an already authenticated session.
Furthermore, the technical structure of these kits is extremely robust. This is because they usually use high-performance reverse proxies, which guarantee that latency is as low as possible. This means that the victim will not notice any delays during the process. The kit will intercept the 2FA token as soon as the user enters it. Later, it will immediately forward it to the legitimate service provider to create a legitimate session for the attacker.
A terrifying feature of the Sneaky 2FA kit is its use of Browser-in-the-Browser (BitB) attacks. This method creates a fake browser window within the actual browser.
Users see a perfectly rendered Microsoft or Google login popup, mimicked down to the address bar and SSL padlock, yet entirely controlled by the attacker.
Realistic animations and loading icons to bypass suspicion.
Functional “Forgot Password” links leading to deep-phishing.
Full support for multiple languages targeting global users.
Designs that work perfectly across all mobile devices.
Because the popup looks so authentic, even tech-savvy users lower their guard. The success rate for these attacks has skyrocketed as 2FA codes are provided without hesitation.
Why Your Traditional 2FA Might Be Failing
Existing 2FA methods such as SMS-based 2FA and Time-based One-Time Passwords are no longer effective. These methods are effective against traditional credential stuffing attacks but are not effective against real-time interception attacks. For example, if a user employs Sneaky 2FA, the attacker can intercept the SMS-based 2FA code the moment the user types the code. This way, the attacker can utilize the 2FA code instantly without the code expiring.
In addition to this, users have become overconfident with the presence of 2FA. This has made them vulnerable to attacks by the latest kits. These kits are programmed to take advantage of the overconfidence of users. These kits are programmed to trick the users into performing the 2FA process on a fake website.
Comparing the Titans of Modern Phishing
As of now, the cybercrime market is flooded with a variety of different Phishing as a Service (PhaaS) products. Even though Sneaky 2FA is the most popular, it still has to compete with other products like Tycoon 2FA and Whisper 2FA, each with its own unique set of features. For example, Tycoon 2FA is known for its heavy use of social engineering attacks. It usually uses AI-generated emails to trap its victims.
On the other hand, Whisper 2FA is designed to be stealthy and patient, using low-frequency harvesting to avoid network-based security warnings. However, Sneaky 2FA is still the favorite among attackers due to its superior capability in intercepting real-time tokens. It provides a smooth experience for the attacker, as it usually works well with Telegram bots. Thus, the information is sent directly to the criminal’s phone within a matter of seconds.
The Staggering Cost of 2FA Phishing
The financial consequences of the use of these sophisticated phishing kits are enormous. According to recent statistics, the number of 2FA phishing attacks recorded globally in 2025 was 45% higher than in the previous year. The increase in the number of 2FA phishing attacks can be attributed to the availability of sophisticated phishing kits like Sneaky 2FA. The financial consequences of the attacks were recorded at $1.2 billion worldwide last year, a 60% increase from the previous year.
Driven by the weaponization of Sneaky 2FA bypass kits globally.
A staggering 60% increase in financial devastation within 12 months.
Of corporate infiltrations now successfully bypass 2FA protocols.
In fact, over 70% of targeted attacks on corporate accounts now involve some form of 2FA bypass. These numbers highlight the urgent need for better security strategies. Therefore, organizations must move beyond basic awareness training and implement technical controls.
Strengthening Your Defenses Against Stealthy Kits
Defending against kits such as Sneaky 2FA demands a multi-layered approach. The most effective defense against such attacks is to adopt FIDO2 and WebAuthn. The advantage of these protocols is that they use public-key cryptography to ensure that the authentication is website-specific. In other words, even if an attacker enters credentials on a phishing website, the hardware key will not sign the challenge. In effect, this neutralizes both AiTM and BitB attacks.
Secondly, it is also possible to use browser security tools to provide an additional layer of security. In fact, some browsers now offer advanced heuristic analysis to detect BitB windows. Thirdly, it is also recommended to use session-binding technologies. The advantage of these tools is that they ensure that a session cookie cannot be used on a different device or IP address. In other words, even in case of cookie theft, it will be immediately ineffective.
Finally, it is also important to monitor such attacks to ensure that they are detected. For instance, unusual login patterns or impossible travel alerts can be set to detect such attacks. For instance, a login from a different country just a few minutes after a successful local login can be a major red flag.
Inside Sneaky2FA: How Adversary-in-the-Middle Phishing Bypasses MFA
This video is a technical explanation of the Sneaky2FA phishing kit and its effectiveness. Unlike other phishing kits that are simple credential harvesters, Sneaky2FA is an adversary-in-the-middle approach that sits between the victim and a legitimate service such as Microsoft.
All authentication traffic is proxied in real-time, enabling the phishing kit to relay the authentication flow seamlessly while intercepting the session cookies and authentication tokens after the user has completed the multi-factor authentication process. These tokens are then used by the attackers to take over the active session without the MFA challenge being performed again.
Sneaky2FA is a showcase of the evolution of phishing attacks from simple credential phishing to a more sophisticated approach involving the interception of active sessions. This approach emphasizes the weakness of MFA as a standalone security control and the importance of other security controls such as domain awareness, phishing-resistant MFA, conditional access, and session monitoring.
Conclusion: MFA Is Not the Finish Line Anymore
Sneaky 2FA is a reminder that modern phishing is no longer about stealing passwords, it is about stealing sessions. With Adversary in the Middle proxying the login flow and Browser in the Browser popups mimicking trusted brands with high fidelity, even careful users can be tricked into handing over an already authenticated session.
Why This Threat Matters Now
This is a scale problem, not an edge case. The post cites a 45% year over year rise in 2FA phishing attacks in 2025, with global damages recorded at $1.2B, and notes that over 70% of targeted corporate attacks now involve some form of 2FA bypass.
Why Every Organization Is Vulnerable
Attackers win when users believe the presence of 2FA means they are safe. AiTM kits exploit that confidence by making the experience feel normal, then quietly capturing what matters most, the session token. Traditional SMS and TOTP flows cannot stop real time interception, because the attacker uses the code immediately.
Where Xcitium Changes the Outcome
For organizations using Xcitium Cyber Awareness Education and Phishing Simulation, this attack would not succeed.
- Employees learn to spot AiTM signals, suspicious URLs, and BitB popups before entering credentials.
- Simulated campaigns build a consistent pause and verify habit under realistic pressure.
- Credential entry drops, session hijack attempts collapse, the attacker loses the advantage at the human decision point.
Move Beyond Basic 2FA
Phishing resistant MFA like FIDO2 and WebAuthn, session binding, and monitoring are highlighted as essential layers for defending against these kits. User training must match the same level of urgency.




