A critical Bluetooth Fast Pair flaw lets hackers hijack your headphones to eavesdrop on conversations and even track your location no user interaction needed.
You might be listening to music with your wireless headphones without knowing how the stranger walking next to you might access the music on the wireless headphones without even disturbing you. Unfortunately, the above-mentioned scenario is now possible. As stated above, the recently announced vulnerability, called WhisperPair or CVE-2025-36911, allows attackers to access the victim’s Bluetooth audio devices without even disturbing the user. In addition to this, the recently announced Bluetooth Fast Pair vulnerability affects hundreds of millions of devices worldwide.
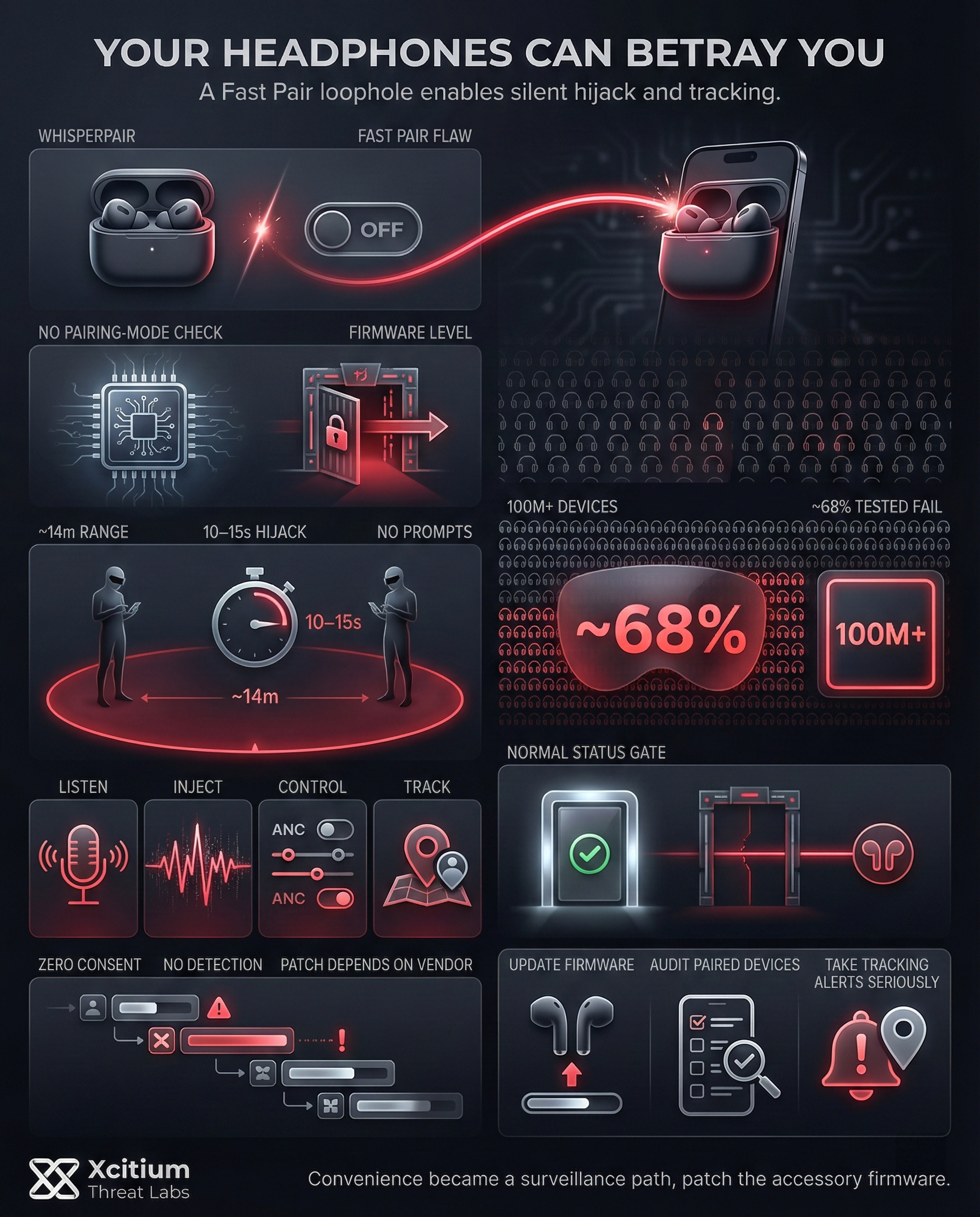
WhisperPair is a critical flaw in Google’s Fast Pair implementation. Researchers found that many accessories accept connections without verifying if the device is in pairing mode.
This firmware-level exploit allows attackers to hijack devices silently. Even Google-certified models are vulnerable, affecting hundreds of millions of audio peripherals worldwide.
What Is WhisperPair? The Fast Pair Loophole Explained
WhisperPair is a critical flaw in the implementation of Google’s Fast Pair protocol on many Bluetooth accessories. Fast Pair is designed to make pairing wireless headphones and earbuds quick and seamless on Android devices. However, security researchers at KU Leuven University discovered that many manufacturers failed to enforce a key security step: checking if the accessory is in pairing mode before accepting a connection.
As a result, an attacker within Bluetooth range can initiate a pairing at any time even when your device isn’t in discoverable mode and the accessory will mistakenly accept the request. This loophole is essentially a free pass for hackers to connect to vulnerable devices without permission.
Crucially, this isn’t limited to Android users. The flaw resides in the accessory’s firmware, not your phone or laptop. In other words, headphones from brands like Sony, Jabra, JBL, Marshall, Xiaomi, OnePlus, Soundcore, Logitech, and even Google’s own Pixel Buds were found to be vulnerable. Hundreds of millions of Bluetooth audio devices are affected, spanning many flagship models.
Furthermore, the issue is systemic: even devices that passed Google’s certification for Fast Pair can have this weakness. In testing, researchers found roughly 68% of popular models they examined could be hijacked via WhisperPair. This widespread impact makes WhisperPair one of the most significant Bluetooth security flaws in recent memory.
How Hackers Exploit the WhisperPair Vulnerability
The WhisperPair attack is alarmingly easy to carry out and requires only a Bluetooth-enabled device and proximity to the victim (around 14 meters). By continuously broadcasting Fast Pair requests, an attacker can force vulnerable headsets or speakers to accept a connection even when they are not in pairing mode.
The hijacking process can take as little as 10–15 seconds and happens silently, with no user prompts or warnings. Once paired, the attacker can fully control the audio device, such as playing sounds or adjusting volume. If the device includes a microphone, this access may also allow eavesdropping on conversations or surrounding audio, effectively turning the accessory into a remote listening device.
Attackers gain unauthorized access to the device’s microphone, turning it into a wireless surveillance tool.
Full override of audio streams. Attackers can inject high-volume disruptive noise or prank audio at will.
Ability to change ANC (Active Noise Cancellation) levels or trigger native voice assistant commands remotely.
Once established, the link remains active without any UI indicators, pop-ups, or confirmation logs on the host device.
What can a hijacker do with your headphones? Once WhisperPair gives an attacker access, they can potentially:
- Eavesdrop on you: Activate the accessory’s microphone to quietly record or stream audio of your conversations and environment.
- Disrupt or inject audio: Play sounds or music through your headphones at will, which could range from prank noises to distressing audio at high volume.
- Modify controls: Use the device controls (pause, skip, voice assistant triggers) or change settings, effectively behaving as the device’s owner.
- Track your movements: If the accessory supports location features, the attacker might leverage them (more on this below).
All of this happens without the legitimate owner’s consent or knowledge. There are no visible indicators that anything is amiss your headphones won’t ask for permission or show a new pairing in an obvious way during the attack. This stealth factor makes WhisperPair especially dangerous, as victims typically remain oblivious while their device is being misused.
Eavesdropping and Tracking: Real-World
In WhisperPair, the threat of device hijacking has taken a new level. There are significant privacy threats. If the device has a microphone, the attacker can eavesdrop or record conversations, including business conversations or other sounds. This violates the assumption that conversations carried out via the earbuds are private.
More worrisome is the possibility of location tracking. Many of these Bluetooth devices support Google’s Fast Pair and Find My Device/Find Hub services, where the first Android account to pair with the device becomes the registered “owner.” WhisperPair allows the attacker to do just this, giving the attacker the ability to claim the device as their own and use it to track the user’s location via Google’s services.
This is particularly useful for real-world stalking situations, where the actions of a victim can be tracked without their awareness. If notifications do display, they could also misleadingly label the tracking device as the victim’s own headphones and thus not heeded. All users could potentially experience these dangers, and non-Android users could particularly be at risk, unaware their earbuds even support Google’s Fast Pair technology.
Protecting Yourself from WhisperPair Attacks
The good news is that awareness and prompt action can greatly mitigate the risk. Manufacturers and Google have been made aware of the WhisperPair vulnerability, and they are releasing firmware updates to address the flaw on the devices that are vulnerable to the exploit. To take the necessary precautions, the following measures are advisable:
Check companion apps or support sites. Install patches immediately.
Sony, JBL, Jabra, OnePlus are affected. Verify your specific model list.
Avoid busy areas with unpatched devices. Watch for odd connections.
Don’t ignore tracking alerts. Regularly audit paired devices.
The experience with WhisperPair serves as a reminder that the added convenience we enjoy with some devices can often leave us with security vulnerabilities that we are not aware of. This time, the quest for speed in the device’s ability to connect with other devices has become the backdoor that hackers can exploit. We can enjoy the added convenience that wireless devices offer without the unwanted company of eavesdroppers or stalkers.
Conclusion: Convenience Turned Into a Surveillance Risk
WhisperPair shows how a “fast” pairing feature can become a silent access path. When an accessory fails to verify pairing mode, proximity is enough for a hijack, and the victim may never see a prompt or warning. The result is not just nuisance audio, it can enable eavesdropping and even location tracking through Fast Pair ownership behavior.
Why This Threat Matters Beyond Headphones
This is a firmware-level weakness in widely used peripherals, including Google-certified models, and it works within Bluetooth range in seconds. Disabling Fast Pair does not fix the underlying flaw, only vendor firmware updates can address it.
Why Many Users Stay Exposed
- Accessories accept pairing without verifying pairing mode
- No user consent is required, hijacks can occur silently
- Patching depends on each manufacturer’s firmware rollout
- Users rarely audit paired devices or take tracking alerts seriously
Where Xcitium Changes the Outcome
For this specific vulnerability, the definitive fix is a manufacturer firmware patch. Whether any Xcitium product can directly prevent WhisperPair accessory hijacking is insufficient data to verify.
What Xcitium can do, is reduce secondary risk around devices and user behavior:
- Xcitium Cyber Awareness Education reinforces “pause and verify” habits for pairing prompts, tracking alerts, and unusual device behavior.
- Xcitium Vulnerability Assessment can help surface missing updates and weak security posture across managed endpoints, supporting faster remediation planning.
Secure the Devices People Trust Most
Update accessory firmware as soon as patches land, treat tracking alerts as high priority, and enforce visibility over device hygiene before convenience becomes exposure.