The Hidden Danger in Windows Shell
Microsoft has recently announced a critical alert related to a sophisticated zero-day vulnerability that is currently being exploited in the wild.
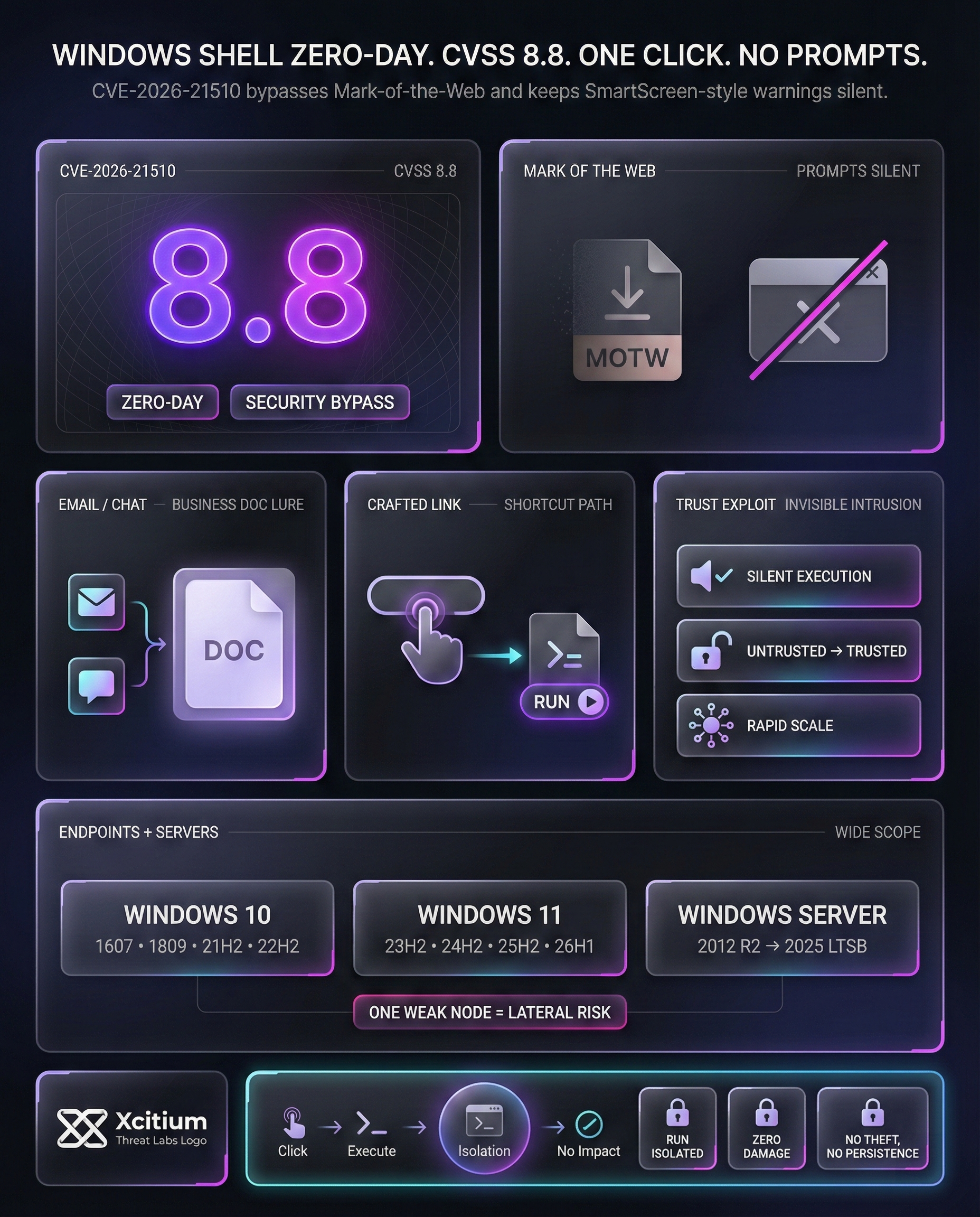
This vulnerability, named CVE-2026-21510, is related to the Windows Shell component of Windows. It allows remote attackers to bypass essential protection mechanisms. In addition, it is rated at a high CVSS score, which is 8.8.
The Windows Shell is responsible for providing a platform for user interaction. It determines how we interact with folders and how we open our files.
However, this provides an extensive entry point for hackers to invade our systems. They target how we interact with certain file types. Therefore, our normal interactions can become a source of danger to our systems. This problem was found by Microsoft and Google security experts.
How Attackers Bypass the Mark of the Web
The basic problem with this weakness is that it is related to the “Mark of the Web” feature. Windows utilizes this information to mark Internet-sourced files.
As a result, it is aware of which files should be treated with caution. SmartScreen typically alerts users to untrusted downloads. Nevertheless, with CVE-2026-21510, attackers can avoid all these measures completely. They can create specially crafted links or malicious shortcuts, which are not suspicious to the internal scanners of the operating system.
The attackers use social engineering as a tool to start the attack. They often use emails or messaging apps to send these malicious links. The attackers use the content to mimic business documents. Once the user clicks on the link, the bypass happens.
The system does not detect the file’s malicious source. Furthermore, the code runs without any security prompts. The smooth running of the code makes the attack successful. It takes away the last hurdle between the attackers and your data.
Why Your Security Prompts Stay Silent
Security prompts serve as a second opinion for the user. They ask for a confirmation before running a suspicious application. However, this zero-day exploit mutes the security prompts.
This is because the exploit bypasses the authentication step, thus no dialog boxes will be displayed. The user will think that he/she is performing a safe operation, while in the background, the processes have already been compromised. This silence is the most dangerous feature of this exploit.
- Silent Execution: Malicious code runs without user interaction beyond the initial click.
- Trust Exploitation: The system treats unauthorized content as a trusted source.
- Invisible Intrusion: Traditional antivirus solutions might miss the bypass during the initial stage.
- Rapid Deployment: Attackers can scale these campaigns quickly across various platforms.
This technical failure affects the fundamental trust in the operating system. When security features are made invisible, the user loses his primary defense.
Additionally, the complexity of the bypass makes it hard to detect. It needs deep system-level analysis to detect the intrusion. Therefore, proactive patching remains the only reliable solution.
Millions of Systems Left Vulnerable
CVE-2026-21510 affects a wide range of Microsoft products. Specifically, both modern and legacy versions of Windows are at risk.
This includes various editions of Windows 10 and Windows 11. Windows Server users must also take immediate action. The following table summarizes the primary affected systems:
CVE-2026-21510
Security Vulnerability Report| Windows 10 | 1607, 1809, 21H2, 22H2 |
| Windows 11 | 23H2, 24H2, 25H2, 26H1 |
| Windows Server | 2012 R2 through 2025 LTSB Editions |
Unpatched legacy systems represent the primary vector for unauthorized intrusion.
A single vulnerable node exposes the entire internal architecture to lateral movement.
Zero-day exploitation potential necessitates immediate administrative intervention.
As shown above, the vulnerability spans a decade of software releases. This extensive impact means that almost every enterprise environment is vulnerable.
Moreover, many home users still run older versions of Windows 10. These systems are particularly attractive targets for opportunistic hackers. IT administrators must prioritize this update across their entire infrastructure. Neglecting even one server could lead to a network-wide breach.
Conclusion: When Windows Trust Becomes the Attack Path
CVE-2026-21510 exposes a dangerous reality, attackers can turn everyday Windows actions into silent compromise. By bypassing Mark of the Web and muting SmartScreen style warnings, a single click on a crafted link or shortcut can run code with no security prompts, removing the last moment where users normally stop and reconsider.
Why This Threat Still Matters
This zero-day is not about tricking tools, it is about breaking trust at the operating system layer.
- Silent execution after the initial click
- Trust exploitation, untrusted content treated as safe
- Invisible intrusion, early stages can evade traditional antivirus
- Rapid deployment across email and messaging driven campaigns
Why Nearly Every Environment Is Exposed
The scope is wide, spanning modern and legacy Windows builds across endpoints and servers. That means almost every enterprise has exposure somewhere, and attackers only need one weak node.
- Windows 10 and 11 versions are impacted, plus Windows Server 2012 R2 through 2025 LTSB editions
- Unpatched legacy systems are the primary entry point
- One vulnerable machine can open the internal architecture to lateral movement
Where Xcitium Changes the Outcome
If you have Xcitium Advanced EDR, powered by Xcitium’s patented Zero-Dwell platform, this attack would NOT succeed.
- Unknown processes are isolated the moment they execute, even when they arrive through trusted looking links and shortcuts
- Code can run without being able to cause damage, because it cannot interact with real data or system assets
- The attacker loses the ability to turn a prompt bypass into encryption, theft, or persistence
Patch immediately across endpoints and servers, then adopt execution time control that keeps silent bypasses from becoming real impact.