Discover how state-linked attackers used XenoRAT malware in spear-phishing emails to breach multiple embassies in South Korea. Uncover the multi-stage campaign, malware features, and key security takeaways.

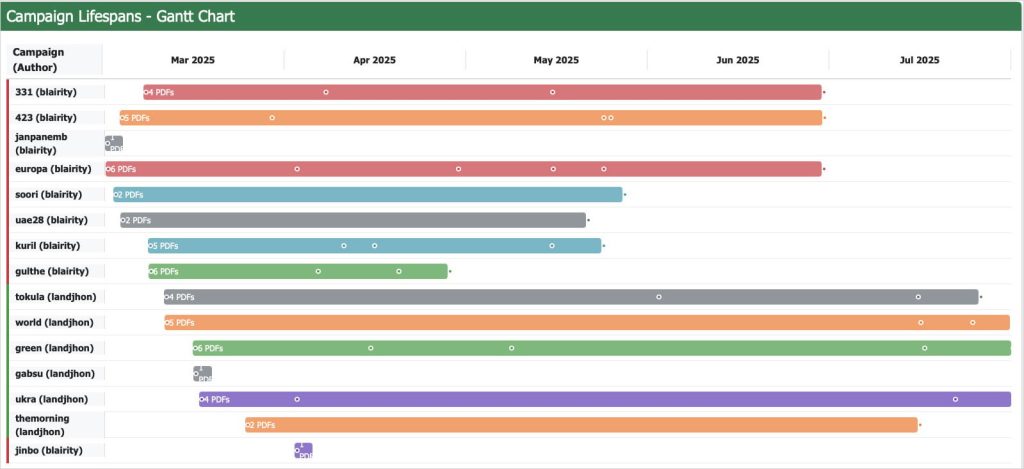
A state-linked espionage campaign targeted several foreign embassies in Seoul by delivering the XenoRAT Trojan through carefully crafted emails. Security researchers report that this operation, discovered in mid-2025, used tailored spear-phishing lures to trick targets into installing malware. Since March 2025, at least 19 malicious emails have been sent to high-value diplomatic staff, exploiting trust in official-looking communications. In this blog, we break down how the attackers operated, what the XenoRAT malware can do, and why these incidents matter for diplomatic cybersecurity.
XenoRAT Malware Overview
XenoRAT is an open-source Remote Access Trojan (RAT) first published on GitHub. Written in C#, it comes with a broad set of built-in features for remote system management. For example, it includes a SOCKS5 proxy and a hidden VNC (Virtual Network Computing) module, allowing attackers to tunnel network traffic and view or control an infected PC’s desktop. The malware even provides a “builder” tool so attackers can generate customized variants of XenoRAT. This open availability means that sophisticated threat actors can readily weaponize it: Cisco Talos researchers observed that a North Korea-linked APT group created a fork of XenoRAT dubbed “MoonPeak” for a recent campaign.
Once running on a victim’s computer, XenoRAT turns it into a powerful spy tool. It can log every keystroke, capture screenshots, and even activate the system’s webcam and microphone to record the user’s activity. It also supports remote file transfers and can execute arbitrary commands, essentially giving attackers full control over the compromised machine. Importantly, XenoRAT loads its code directly into memory (a “reflective” injection) and is packed with Confuser Core obfuscation. These techniques mean it leaves little trace on disk and can evade many antivirus and detection tools.
Tailored Spear-Phishing Campaign Against Embassies
Trellix researchers found that the attackers used a multi-phase spear-phishing campaign to reach their victims. In the first phase (March 2025), attackers sent probing emails to test defenses – the earliest mail targeted a Central European embassy. In the second phase (May 2025), the lures became much more sophisticated. For instance, on May 13 an email was crafted to look as if from an EU delegation official, inviting a Western European embassy to a “Political Advisory Meeting”. In June and July, the themes shifted to the U.S.–South Korea military alliance. In each phase, the attackers mainly aimed at European embassies in Seoul, sending messages about meetings, policy briefings, or event invitations from fake diplomatic senders.
Source: Trellix
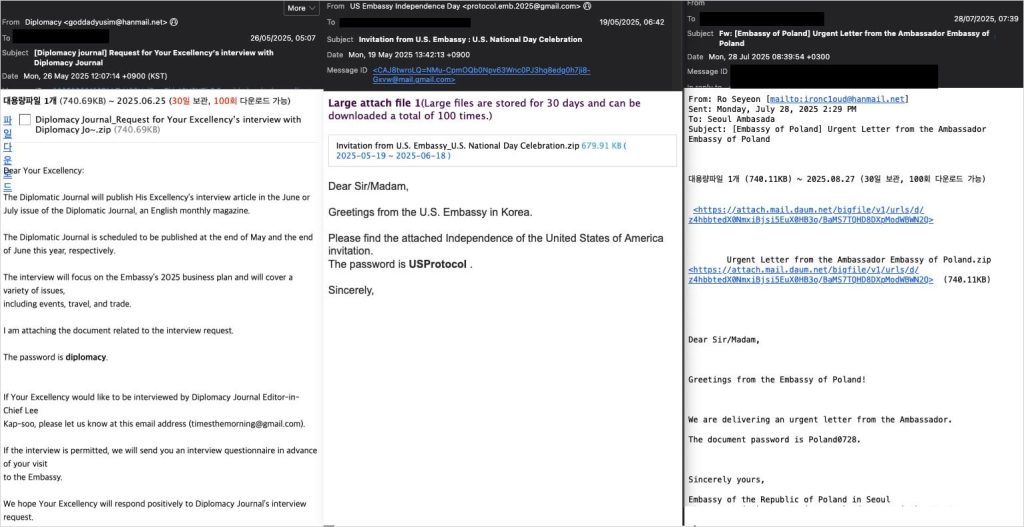
The phishing emails were highly contextual and multilingual. Messages were written in Korean and in relevant foreign languages (English, Persian, Arabic, French, and Russian) to match the target. The attackers also timed many emails to coincide with real events or official schedules, making the fake invitations and letters seem credible. For example, the May 13 email aligned with an actual meeting date, adding to the illusion of legitimacy. By mimicking real diplomats and events, the attackers boosted the chances that recipients would trust and open the malicious attachments.
Source: Trellix
Delivery Mechanism and Infection Chain
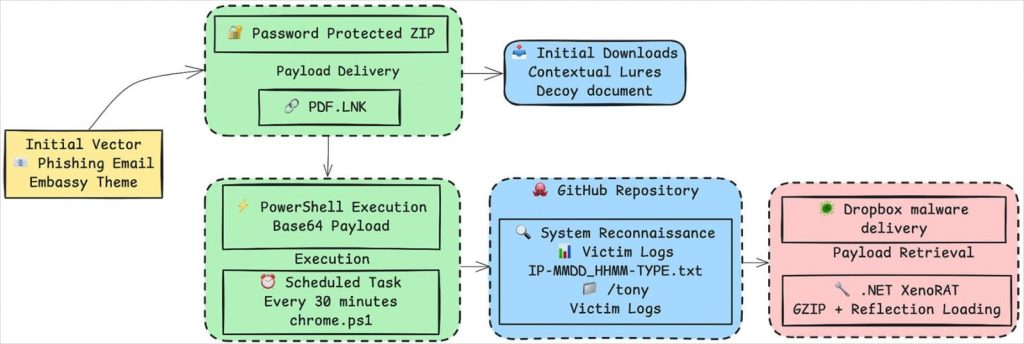
Across all phases of the campaign, the attackers used a consistent infection method. Each phishing email contained a password-protected ZIP archive (a tactic to evade email scanners) hosted on a cloud storage service like Dropbox, Google Drive, or South Korea’s Daum cloud. Inside the ZIP was a Windows shortcut file (.LNK) disguised with a PDF icon. When the victim opened this file, it executed an obfuscated PowerShell script. The script then downloaded the real XenoRAT payload from a remote source (either GitHub or another cloud storage) and installed it on the machine. Finally, the script created a scheduled task to ensure the malware would run persistently on the system. This multi-step chain – email → ZIP → shortcut → PowerShell → XenoRAT – allowed the attackers to bypass many security controls and quietly deploy the Trojan.
XenoRAT Capabilities and Stealth
Once installed, XenoRAT gave the intruders extensive monitoring and control over the infected computer. The researchers noted it could record all keystrokes, capture screenshots of the desktop, and activate the webcam and microphone, turning the device into a live spy camera. The RAT’s file transfer and remote shell functions allowed attackers to upload or download data and run commands at will. Crucially, because XenoRAT is injected into memory and heavily obfuscated, it avoids writing obvious files to disk. This in-memory execution and Confuser Core packing make it very stealthy, helping the malware hide from antivirus and forensic tools.
Source: Trellix
Attribution and Suspected Actors
The sophistication and targeting of this campaign strongly suggest state-sponsored backing. Trellix analysts point out that many details match the known methods of North Korea’s Kimsuky group (also known as APT43). Clues include the use of Korean-language email services, abuse of GitHub for command-and-control, and an internal GUID/mutex that Kimsuky has used in prior malware. In fact, some of the IP addresses and domains involved were previously tied to Kimsuky operations. On the other hand, some evidence hinted at Chinese involvement: the attackers’ working hours and holiday breaks aligned with China’s time zone (they paused on Chinese holidays but not on Korean ones). Due to this mix of factors, Trellix attributes the attack to Kimsuky/APT43 with medium confidence, acknowledging a possible Chinese sponsorship or cooperation. In any case, this remains a sophisticated cyber-espionage campaign against diplomatic targets.
Global Context and Implications
This South Korean embassy incident is part of a broader trend of cyber-espionage against diplomatic missions. Similar campaigns have been seen elsewhere. For example, Mandiant reported that in early 2023 Russia’s APT29 (also known as Cozy Bear) ran a spear-phishing wave against Turkish diplomats, using earthquake-themed lures to infect target systems. In another case, security researchers found that Belarusian hackers had quietly targeted foreign embassies for nearly a decade by tricking diplomats into installing malware disguised as Windows updates. These examples highlight that foreign ministries and embassies are prime intelligence targets worldwide, and attackers will employ sophisticated social engineering and malware to breach them.
Conclusion and Defense Measures
In summary, the XenoRAT campaign against South Korean embassies shows how modern attackers combine social engineering with powerful malware to steal information. The attack used realistic, context-aware phishing messages to deliver an open-source RAT that provides full remote access and surveillance. To defend against such threats, organizations should enforce strict email security controls: block or quarantine unexpected password-protected attachments, validate unexpected meeting invitations through secondary channels, and train staff to recognize official vs. suspicious messages. Technical defenses should include monitoring for unusual outbound traffic (such as connections to public GitHub repos or cloud storage) and deploying advanced endpoint protection that can detect in-memory malware behavior. By staying vigilant and layered in defense, even high-level targets like embassies can reduce the risk of falling victim to these state-level cyber-espionage campaigns.