Continuous Malware Research delivering Early Warning, Actionable Intelligence, and Preemptive Protection against emerging cyber threats Worldwide.

20,000 WordPress sites are vulnerable due to a backdoor in an Elementor add-on plugin, allowing...

A critical Bluetooth Fast Pair flaw lets hackers hijack your headphones to eavesdrop on...

Droppers are stealthy Trojans designed to install other threats (viruses, ransomware). Discover how...
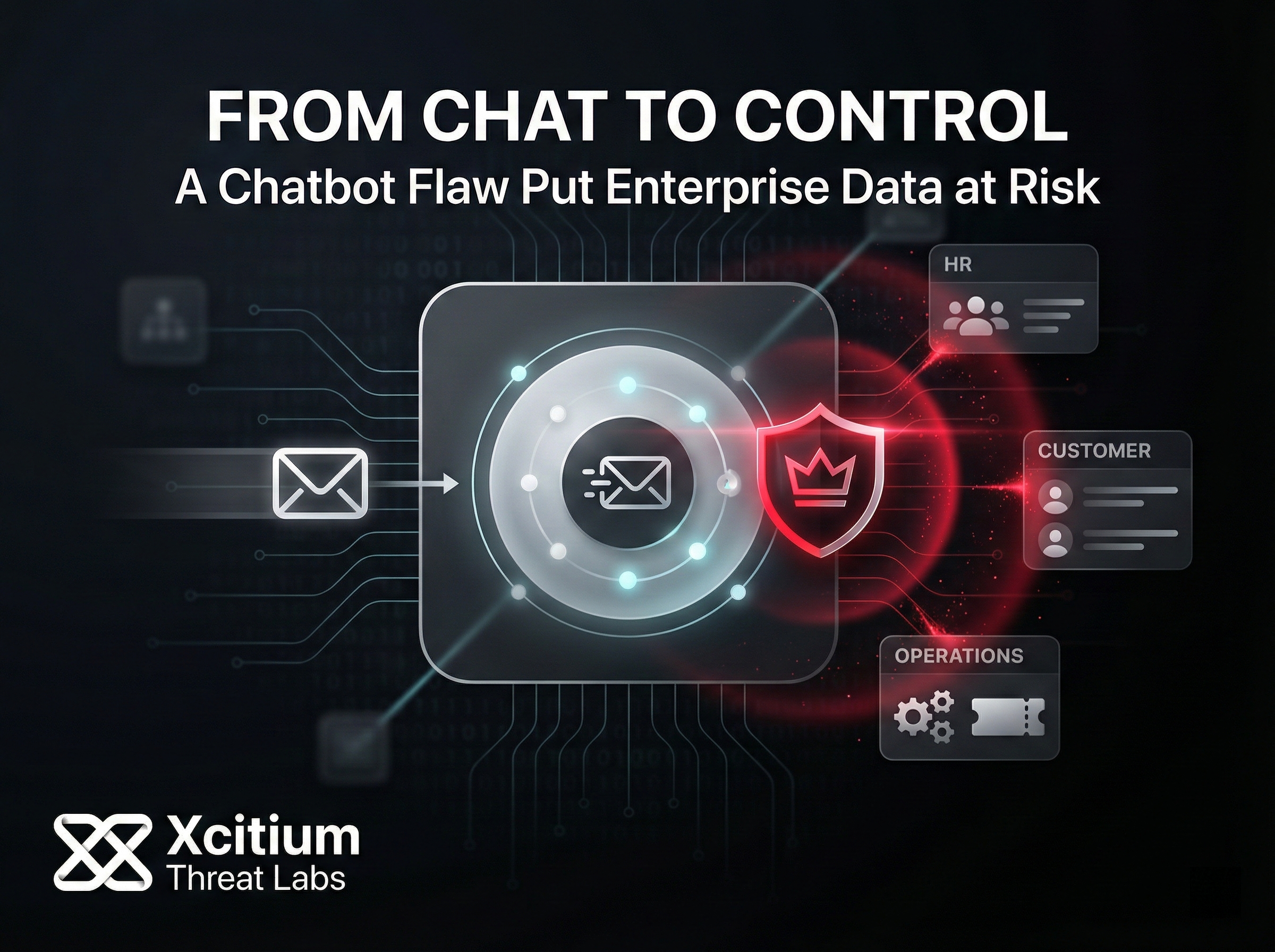
A critical AI flaw in ServiceNow let attackers impersonate users and seize full control. Learn what...
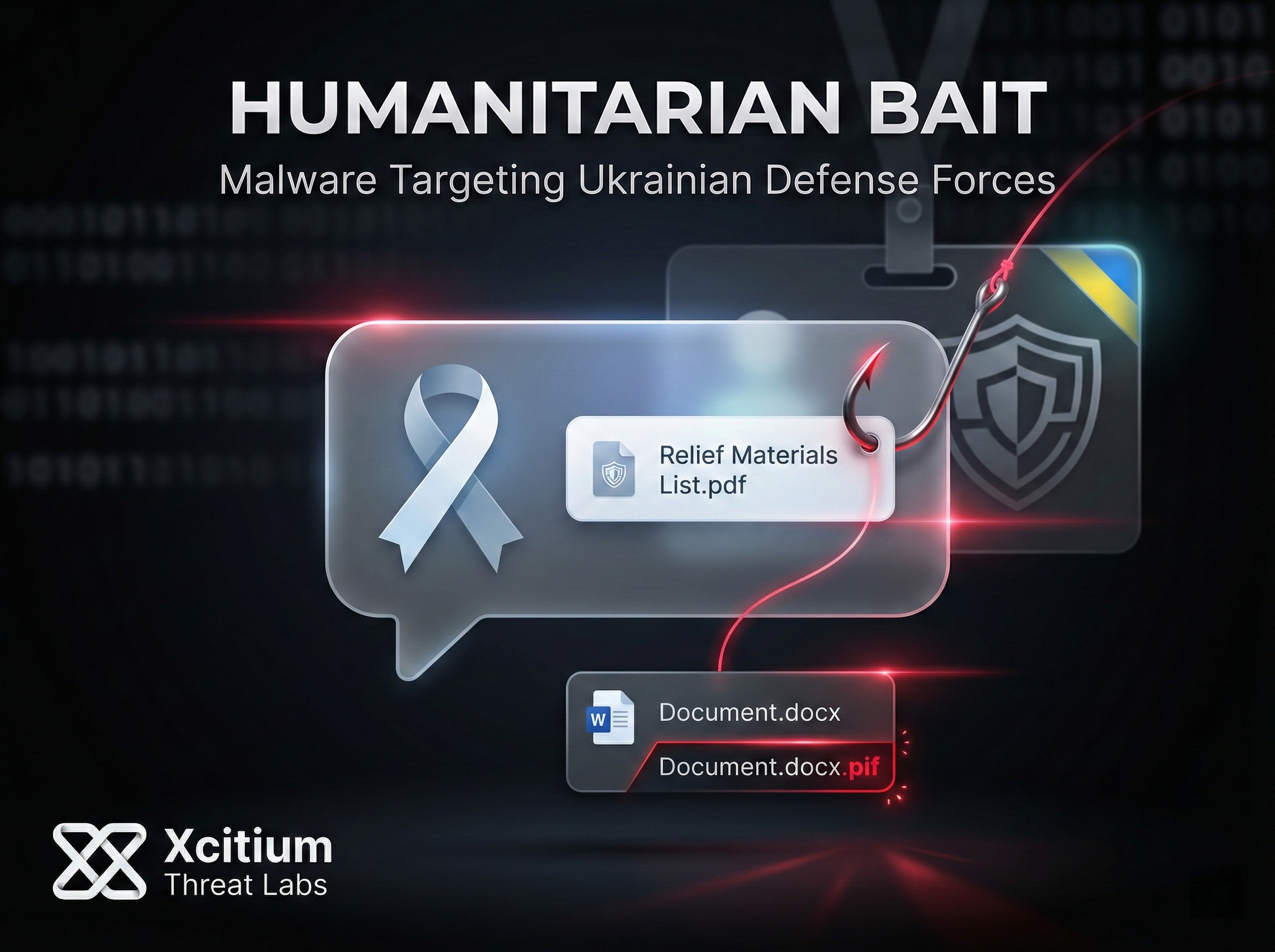
Ukraine’s army officials were targeted by a fake charity scam delivering the PluggyApe...

CIRO, Canada’s investment regulator, was hit by a data breach after a phishing attack that...

Google’s $4.75B energy deal highlights a trend: tech giants are investing in power to run AI data...

Global-e data breach exposed personal info of Ledger customers. Learn what was leaked, why your...
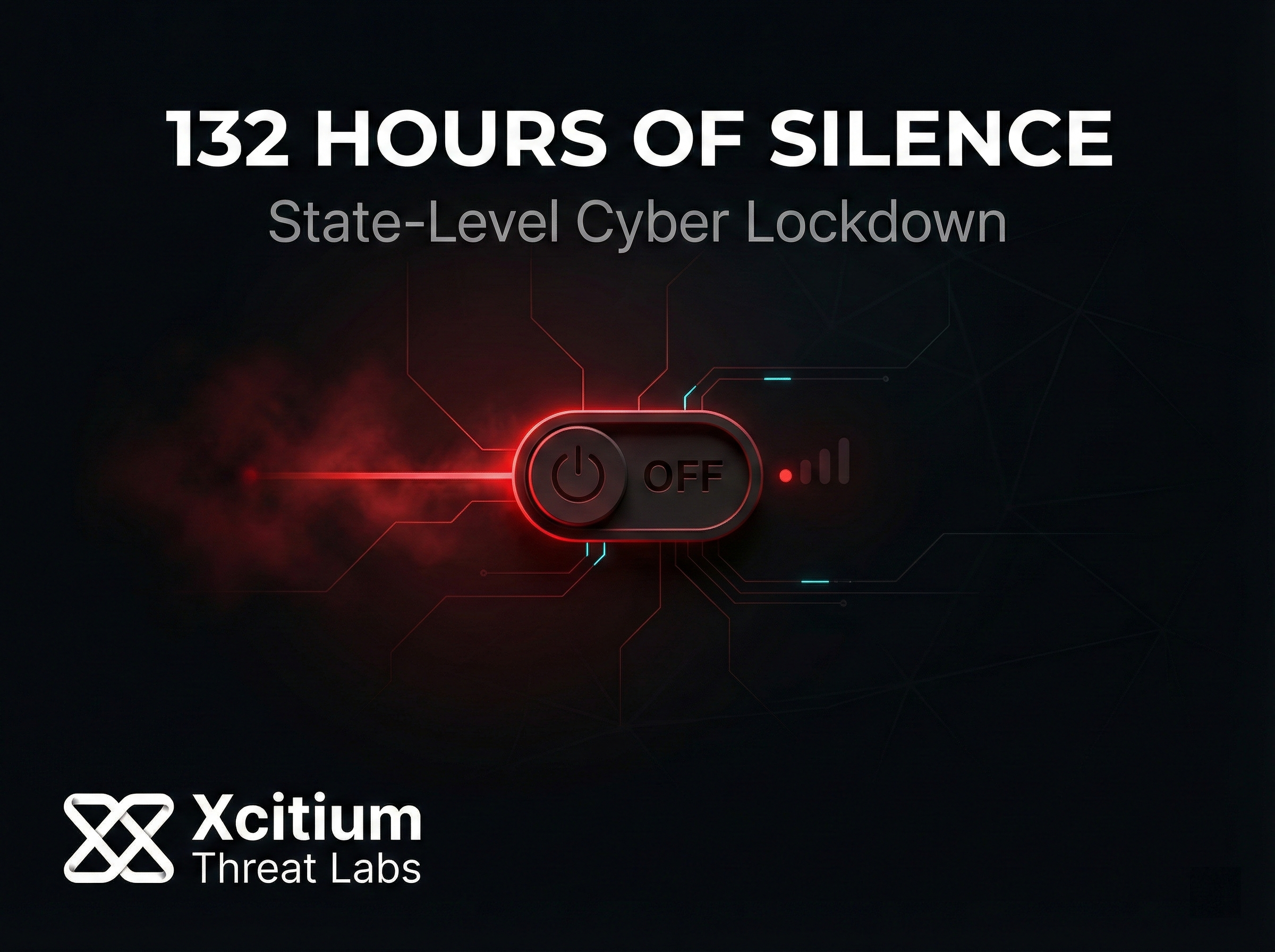
Recently, Iran imposed a sweeping internet blackout to stifle nationwide protests. This post...

CISA Warns of Zero-Day, High-Severity Gogs Vulnerability That Enables Remote Code Execution and Is...

Explore Nova ransomware (formerly RALord) its recent attacks, evolution, and key indicators. Learn...

Discover the critical RCE vulnerability CVE-2025-59470 in Veeam Backup & Replication. Learn...
Xcitium exists to ensure that people can embrace technology fully, without the shadow of insecurity hanging over them. We’re here to give users the freedom to explore, create, and connect without fear. Whether it’s preventing unknown files from compromising systems or offering innovative approaches to endpoint protection solution, Xcitium’s technology is designed to foster confidence. We believe that by keeping the digital ecosystem secure, we’re directly contributing to human evolution—by enabling people to take full advantage of the tools that define our era.
Book a Demo