The Rise of a New Cyber Adversary: An Overview
The Gentlemen was first spotted in August 2025. It has since become an extremely potent adversary in the world of cybercrime.
This group is different from other opportunistic groups that do not take the time to customize their attacks. The Gentlemen carries out an extensive analysis of the security setup of the target before launching attacks. This makes this adversary extremely dangerous.
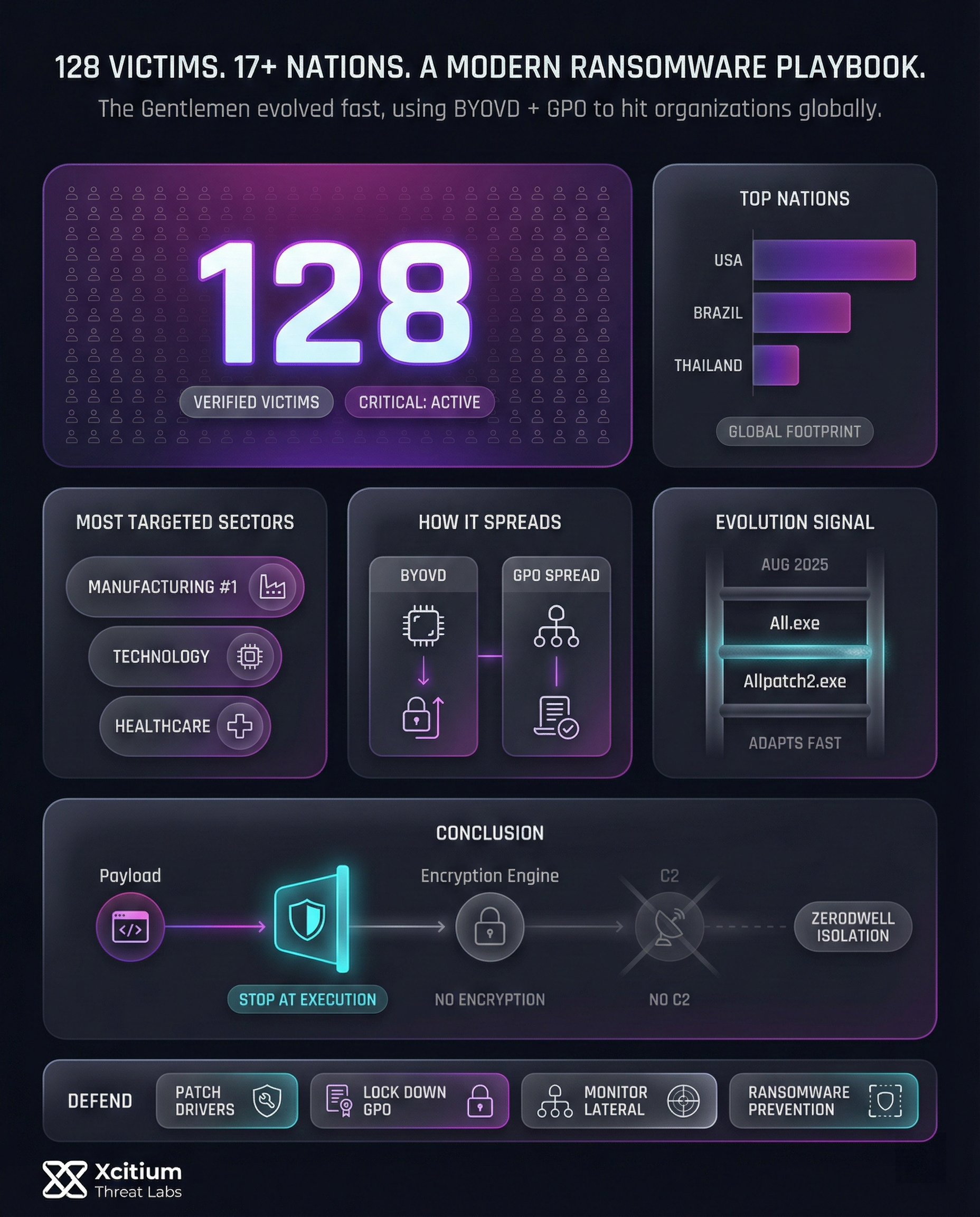
This ransomware adversary makes use of custom-made tools that are capable of evading certain security software. They use this tool by means of Bring Your Own Vulnerable Driver (BYOVD), which makes it possible for the execution of harmful code with escalated privileges.
The other way that this adversary carries out attacks is by using Group Policy Objects (GPO) with the intention of spreading the attack over the entire domain.
Evolution of a Threat: History and Adaptive Tactics
Since its first detection in August 2025, The Gentlemen ransomware has demonstrated an aggressive rate of evolution with respect to its approach to attacks. In its initial stage, the group could be said to have employed relatively basic anti-AV tools.
However, the group has since moved on to more targeted versions of attacks, as demonstrated by the evolution from All.exe to Allpatch2.exe. This is indicative of the group’s efforts at evading security systems.
The group’s approach is characterized by reconnaissance, which is necessary in planning attacks that are targeted at specific systems. Rather than launching attacks on a wide scale, the group takes time to survey the security systems they are targeting.
Recent Campaigns and Noteworthy Attacks
The Gentlemen ransomware group continues to operate, and the latest attacks have highlighted their activities. For instance, towards the end of January 2026, various organizations have been impacted by the group’s activities. This shows that the group continues to target various entities.
Notable recent victims include:
- Nobel Hygiene Pvt (India): Discovered on January 31, 2026.
- Wieson Technologies (Taiwan): Also discovered on January 31, 2026.
- Lawsoft (US): An attack discovered on January 31, 2026, with an estimated attack date in February 2025.
- Röben Tonbaustoffe GmbH (Germany): Discovered on January 31, 2026, with an estimated attack date in January 2026.
The examples have highlighted the Gentlemen ransomware group’s ability to target organizations across the globe. The estimated dates of the initial attacks on some of the organizations, which go back to the start of 2025, have highlighted the possibility of the group operating with a significant lag between the initial attack and the public announcement or the encryption of the data.
The Gentlemen Intel
Recent Confirmed Operations
| Target Entity | Actor | Timeline | Breach Intelligence |
|---|---|---|---|
| Nobel Hygiene Pvt India (Healthcare/Manufacturing) | The Gentlemen | Disc: 2026-01-31 | Confirmed breach of internal databases and operational documents in India. |
| Wieson Technologies Taiwan (Technology) | The Gentlemen | Disc: 2026-01-31 | Source code and engineering blueprints suspected compromised. |
| Lawsoft USA (Legal Technology) | The Gentlemen |
Disc: 2026-01-31 Est: 2025-02-14 |
Long-term persistence identified. Massive PII and legal document exfiltration. |
| Röben Tonbaustoffe GmbH Germany (Manufacturing) | The Gentlemen |
Disc: 2026-01-31 Est: 2026-01-15 |
Production line interruption following encryption of central servers. |
Targeted Industries and Global Reach
Gentlemen ransomware group has created a wide footprint of operations, including various sectors and geographic locations. Currently, the group has recorded 128 victims, as of 4 February 2026. The ransomware attacks are not specific to a given sector or industry, but they have created a wide footprint of operations with a comprehensive targeting strategy.
Key sectors frequently targeted include:
- Manufacturing: This industry accounts for the highest number of reported incidents.
- Technology: Tech companies are also heavily impacted, reflecting the group’s technical prowess.
- Healthcare: Attacks on healthcare organizations are particularly concerning, given the critical nature of their services.
- Financial Services: This sector remains a prime target due to the sensitive data it handles.
- Education: Educational institutions have also fallen victim to their campaigns.
Gentlemen ransomware group has created a wide footprint geographically, although the United States, Brazil, and Thailand are the primary targets for the ransomware group, with other countries affected including at least 17 nations, including France, India, Indonesia, Colombia, Vietnam, the United Kingdom, and Mexico.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs)
Since The Gentlemen is relatively new profile, TTPs are based on observed samples and affiliate behavior.
The Gentlemen TTPs
Case Study: Xcitium vs. The Gentlemen Ransomware
This demonstration showcases how Xcitium protects endpoints from ransomware attacks in real time through a prevention-first security model. Seven live Gentleman ransomware samples are executed in a controlled environment to replicate a realistic, multi-sample attack scenario.
Rather than depending on signatures, reputation scoring, or reactive detection, Xcitium’s ZeroDwell isolation technology identifies each Gentleman payload as untrusted at the moment of execution and immediately restricts its execution within an isolated environment.
As a result, The Gentleman ransomware is unable to progress through its attack lifecycle. Encryption routines are stopped before activation, persistence mechanisms fail to deploy, and no command-and-control communication is established despite the samples being fully functional.
By removing the exposure window entirely, Xcitium keeps the endpoint fully operational and uncompromised. This video demonstrates how modern ransomware threats like The Gentleman are neutralized instantly using continuous zero-trust execution and real-time isolation.
Indicators of Compromise (IOCs): Identifying the Threat
To identify and contain The Gentlemen ransomware, it is crucial to be watchful and to have the ability to identify certain indicators of compromise (IOCs), which are digital markers to identify the presence of the malware or to analyze past attacks.
Key IOCs associated with The Gentlemen ransomware include:
- KILLAV Tool SHA1: c0979ec20b87084317d1bfa50405f7149c3b5c5f
- Ransom Note: README-GENTLEMEN.txt
- Encrypted File Extension: .7mtzhh
- Tox ID: F8E24C7F5B12CD69C44C73F438F65E9BF560ADF35EBBDF92CF9A9B84079F8F04060FF98D098E
- Onion Site: tezwsse5czllksjb7cwp65rvnk4oobmzti2znn42i43bjdfd2prqqkad.onion
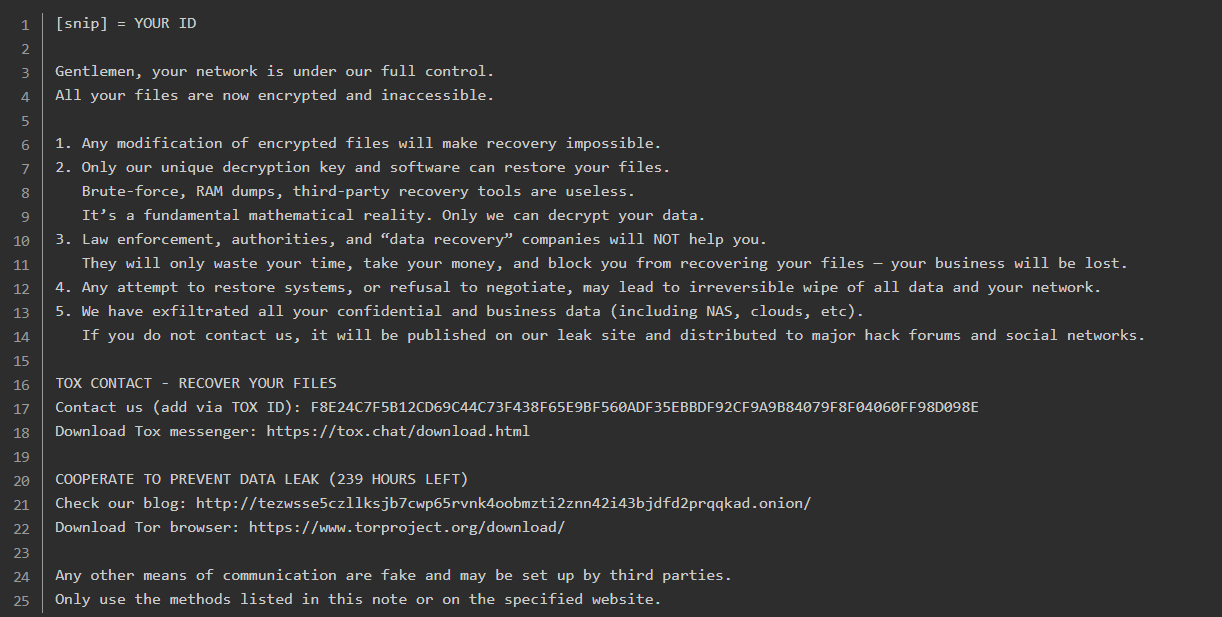

These indicators of compromise should be integrated into the security architecture of the organizations. This is a preventive measure to identify the presence of The Gentlemen ransomware in the network of the organizations. It is also crucial to ensure the availability of the latest updates regarding the indicators of compromise.
The Gentleman Ransomware SHA-1 Samples & Zero‑Dwell Threat Intelligence Reports
Conclusion: A Targeted Ransomware Built to Outsmart Defenders
The Gentlemen is not a noisy smash and grab ransomware crew. It studies your environment first, then uses custom tooling, BYOVD privilege escalation, and domain-wide deployment via GPO to turn one foothold into enterprise scale impact. That is why this threat is rising fast, and why it is showing up across multiple countries and sectors.
Why This Threat Is Harder Than It Looks
The danger is not just encryption. It is the operational discipline behind it.
- Reconnaissance before action, tailored to your defenses
- BYOVD to gain elevated privileges and bypass security controls
- GPO-based spread to accelerate domain-wide disruption
- A lag between initial access and public impact, which buys attackers time
Why Organizations Stay Exposed
Many environments still give ransomware the one thing it needs, execution freedom.
Security gaps that The Gentlemen can exploit include weak visibility into pre-attack reconnaissance, inconsistent control over driver abuse paths, and the ability for malicious tooling to execute and expand before teams can respond.
Where Xcitium Changes the Outcome
If you have Xcitium Advanced EDR, this attack would not succeed.
- Payloads may start, but code can run without being able to cause damage
- Encryption is stopped before activation
- Persistence attempts fail to deploy
- Command and control communication does not establish, even when samples are functional
Prevent the Next Targeted Ransomware Event
The Gentlemen demonstrates the modern ransomware truth, attackers do not need chaos, they need execution. Remove that advantage, and the attack chain collapses before business operations do.